How trusted integrations become breaches
For security teams, the day rarely begins with an incident. It begins with a queue. Alerts to triage. Access requests to review. Exceptions to approve. Meanwhile, third-party SaaS integrations connected to platforms like Salesforce and Google bypass IT approval, often requesting broad OAuth scopes that are difficult to fully assess under pressure.
What is not visible is where real risk accumulates. A trusted Salesloft integration, deeply embedded in daily revenue workflows with access to sensitive customer data, has already been compromised. The API calls appear legitimate. OAuth tokens are valid. Activity blends into normal business operations. Traditional controls continue to monitor endpoints and users, while SaaS-to-SaaS access between Salesloft, Drift, and Salesforce operates quietly in the background.
Attackers take advantage of that trust. They replay tokens, move laterally across connected SaaS applications, and access sensitive data over time without triggering alerts. There is no malware. No anomalous login. Nothing that clearly signals an incident.
Days turn into weeks before a vendor disclosure finally surfaces the breach. Security teams scramble to pull incomplete logs, reconstruct timelines across multiple platforms, and answer urgent questions about exposure and impact with limited visibility.
This is the reality of modern SaaS supply chain breaches. Detection happens late. Investigation is manual.
Your SaaS Supply Chain security needs a new approach
What made breaches like Salesloft–Drift so damaging wasn’t a single missed alert, but a security model never designed for modern SaaS ecosystems.
SaaS sprawl is outpacing security
As organizations adopt thousands of SaaS applications, business teams increasingly connect new tools and integrations to move faster and drive productivity. In fact, across our customer environments, we observed an average 120% year-over-year increase in new integrations in Microsoft alone. OAuth access is granted rapidly, broad scopes are routinely approved, and integrations become deeply embedded in daily workflows, often without a clear understanding of the access paths and permissions being introduced. Without the right tools, security teams can’t keep pace, lacking continuous visibility into connected integrations, evolving permissions, and hidden dependencies across their SaaS supply chain.
The shared responsibility gap
In the event of a breach, organizations cannot rely on SaaS vendors to investigate or contain incidents on their behalf. While platforms like Salesforce or Salesloft enable third-party integrations, the shared responsibility model makes customers fully accountable for the security and use of connected applications and OAuth access.
When a SaaS environment is compromised through a third-party integration, the liability and impact rest with the customer, not the SaaS vendor. Vendors may disclose incidents only after a breach is confirmed, but they lack visibility into how trusted access is used within each customer environment and are not positioned to monitor, investigate, or respond to SaaS supply chain attacks in real time.
How legacy tools are failing you
This disconnect is compounded by how third-party risk is typically managed today. Most programs remain point-in-time exercises: vendors are reviewed annually, access is approved once, and integrations are forgotten. Meanwhile, OAuth tokens persist indefinitely, permissions expand, integrations evolve, and non-human identities operate without clear ownership, creating ideal conditions for attackers to exploit trusted access as a backdoor.
This problem runs deeper: legacy security tools were never designed to understand what happens inside and between SaaS applications. They operate at the perimeter, focusing on user logins, network traffic, or isolated application activity while modern SaaS risk propagates entirely within the SaaS layer itself.
In attacks like Salesloft–Drift, that access looks entirely legitimate with tokens and API keys seeming absolutely normal. Traditional tools such as CASBs or SIEMs weren’t designed to question trusted behavior or understand how access propagates across SaaS applications. As a result, security teams are left with fragmented visibility – stitching together identity data, SaaS logs, and vendor details only after a disclosure, when meaningful damage has already been done. On top of that, these tools are often messy and difficult to read, taking long times for teams to understand what has gone wrong. For example, this is how Salesforce logs look like and teams have to decipher this across multiple SaaS platforms, and spreadsheets before they understand what happened exactly.
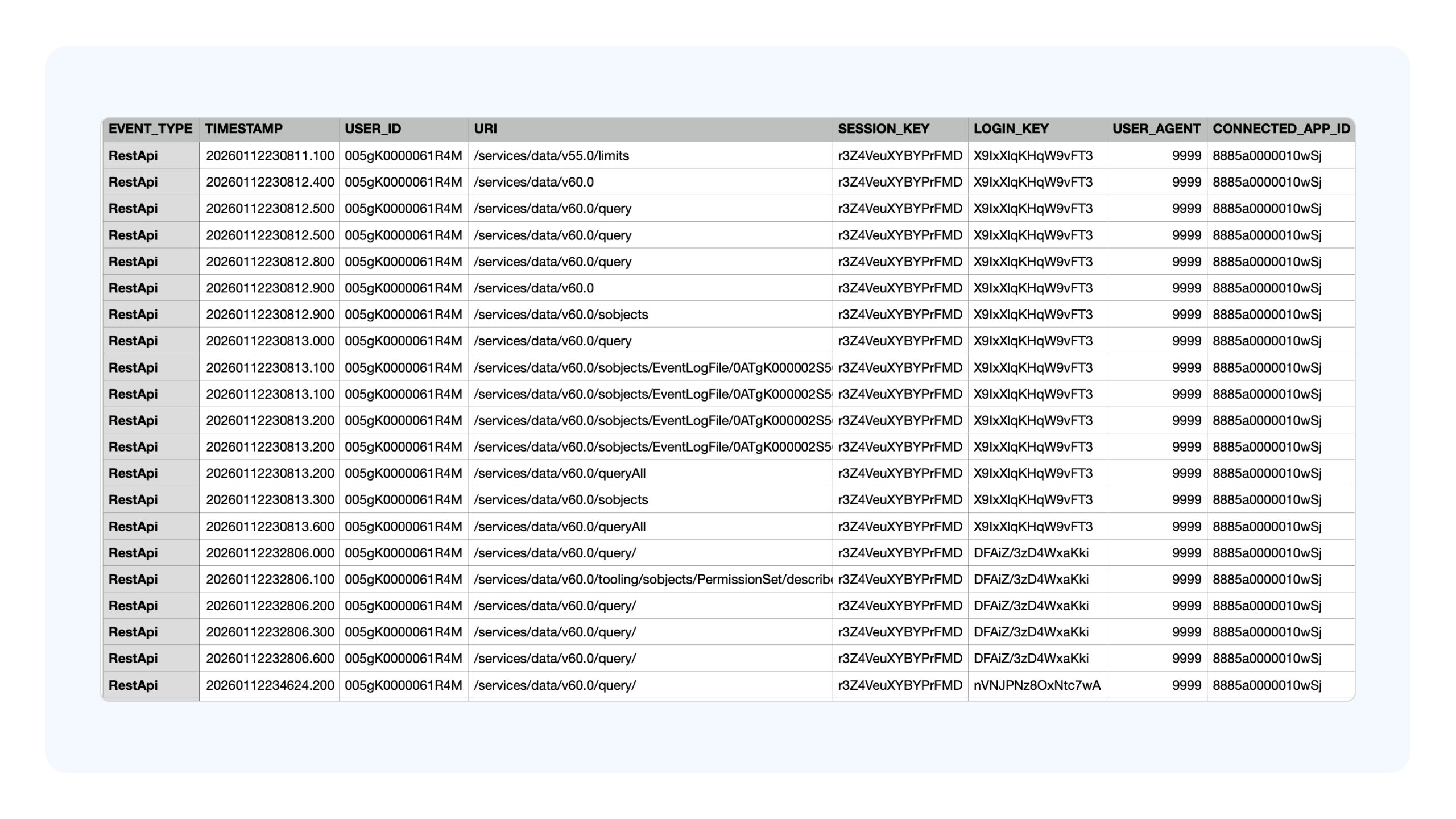
The core issue is that legacy tools are looking in the wrong place - they secure the perimeter of SaaS, while SaaS supply chain risk lives entirely inside it. Without visibility into SaaS-to-SaaS relationships, effective permissions, and real behavior across integrations, organizations are left blind to the very risks attackers are exploiting.
This problem is only going to get worse with AI Agent Adoption
This risk is accelerating rapidly with the rise of AI agents inside the enterprise. Unlike traditional integrations, AI agents don’t just connect systems, they act independently, co-ordinating actions across SaaS applications using long-lived tokens, APIs, and non-human identities. Without clear visibility into the permissions they hold and the actions they take across SaaS environments, organizations are left highly exposed, turning AI agents into powerful, and often invisible, entry points for SaaS supply chain attacks.
Together, these challenges make one thing clear: securing the SaaS supply chain requires a fundamentally different approach. Integrations and non-human identities don’t behave like users, making perimeter-based defenses, static controls, and periodic reviews ineffective. It demands continuous visibility into integrations and access, an understanding of how trusted access is actually used, and detection rooted in behavioral baselining rather than static rules. Just as importantly, it must enable fast, confident responses with clear insight into blast radius and impact, without waiting on vendor notifications to catch up.
Secure your SaaS supply chain end to end with Obsidian
Obsidian enables security teams to move from reactive investigation to proactive, confident protection of their SaaS supply chain by exposing the attack surface, detecting abuse early and accelerating response with full confidence .
Let’s see what this looks like in practice:
Continuous visibility into your SaaS supply chain
Obsidian automatically discovers and inventories every SaaS integration, including OAuth apps, APIs, service accounts, non-human identities, and shadow integrations. With an always-up-to-date view of access and data flow, security teams reduce blind spots, shrink attack surface, and lay the foundation for earlier detection and faster response.
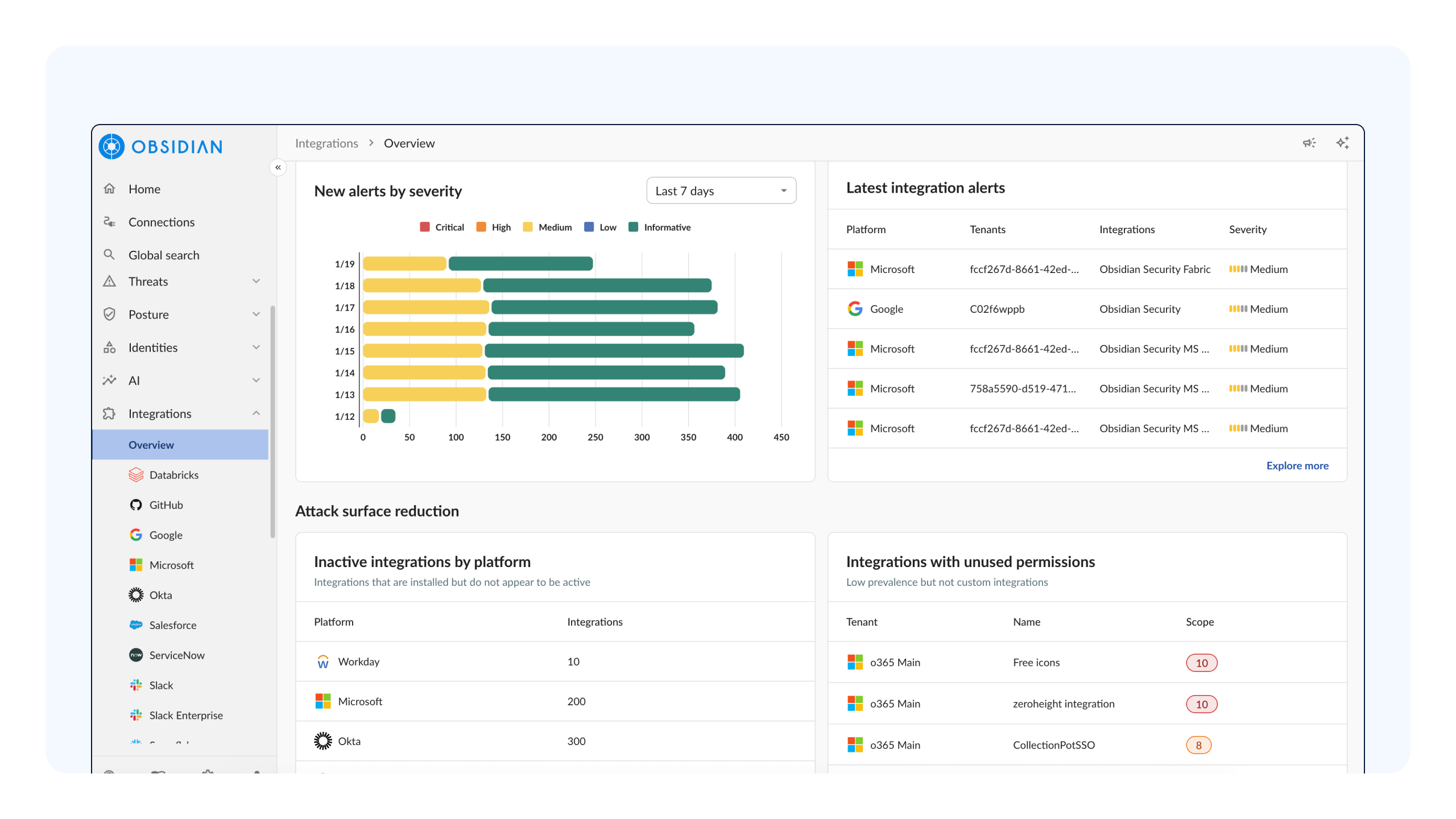
Reduce integration risks before it’s exploited
Obsidian continuously evaluates how integrations are actually used, combining permissions, identity context, and real activity to surface which integrations carry real risks and assigns them a score based on their level of risk. This enables teams to prioritize and take proactive steps such as removing inactive integrations and right-sizing access, reducing supply chain risk without slowing the business.
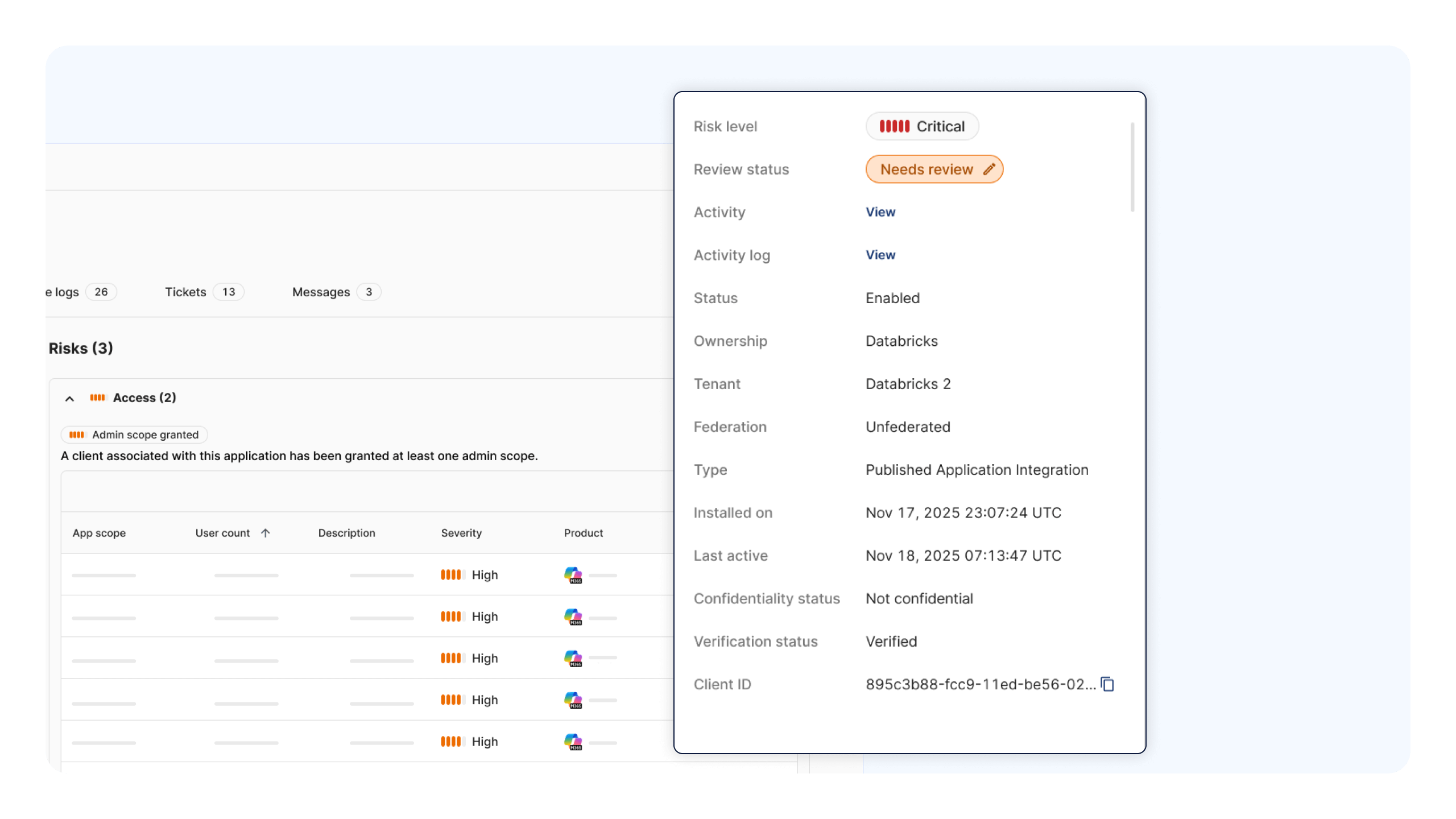
Detect SaaS supply chain attacks at the earliest sign of compromise
Modern SaaS supply chain attacks exploit trust that security teams can’t see. Obsidian detects this abuse early by establishing behavioral baselines across identities, APIs, and integrations, then correlating deviations with threat intelligence and known indicators of compromise. This means teams can identify compromised integrations quicker, reduce attacker dwell time, and stop data exfiltration.
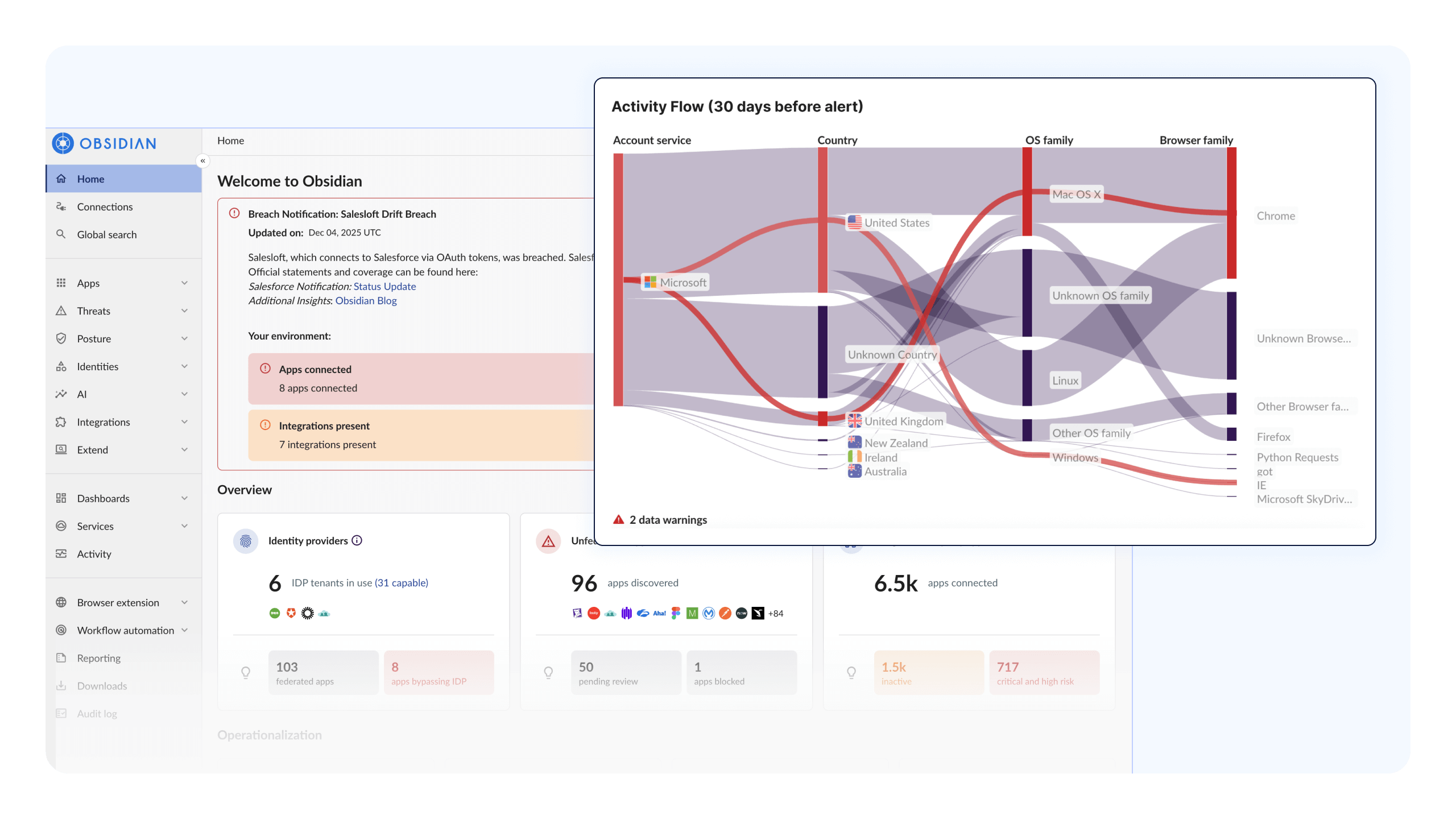
Contain breaches quickly and remediate confidently
When a SaaS integration is compromised, security teams often lose valuable time manually piecing together impact across disconnected tools. Obsidian provides immediate visibility into blast radius by reconstructing full attack paths across identities, integrations, permissions, and activity so teams know exactly what was accessed and what’s at risk. With guided remediation, built-in workflows like ServiceNow and Webhook and the flexibility to integrate your own workflows, teams can contain breaches quickly, limit lateral movement, and resolve incidents with confidence.
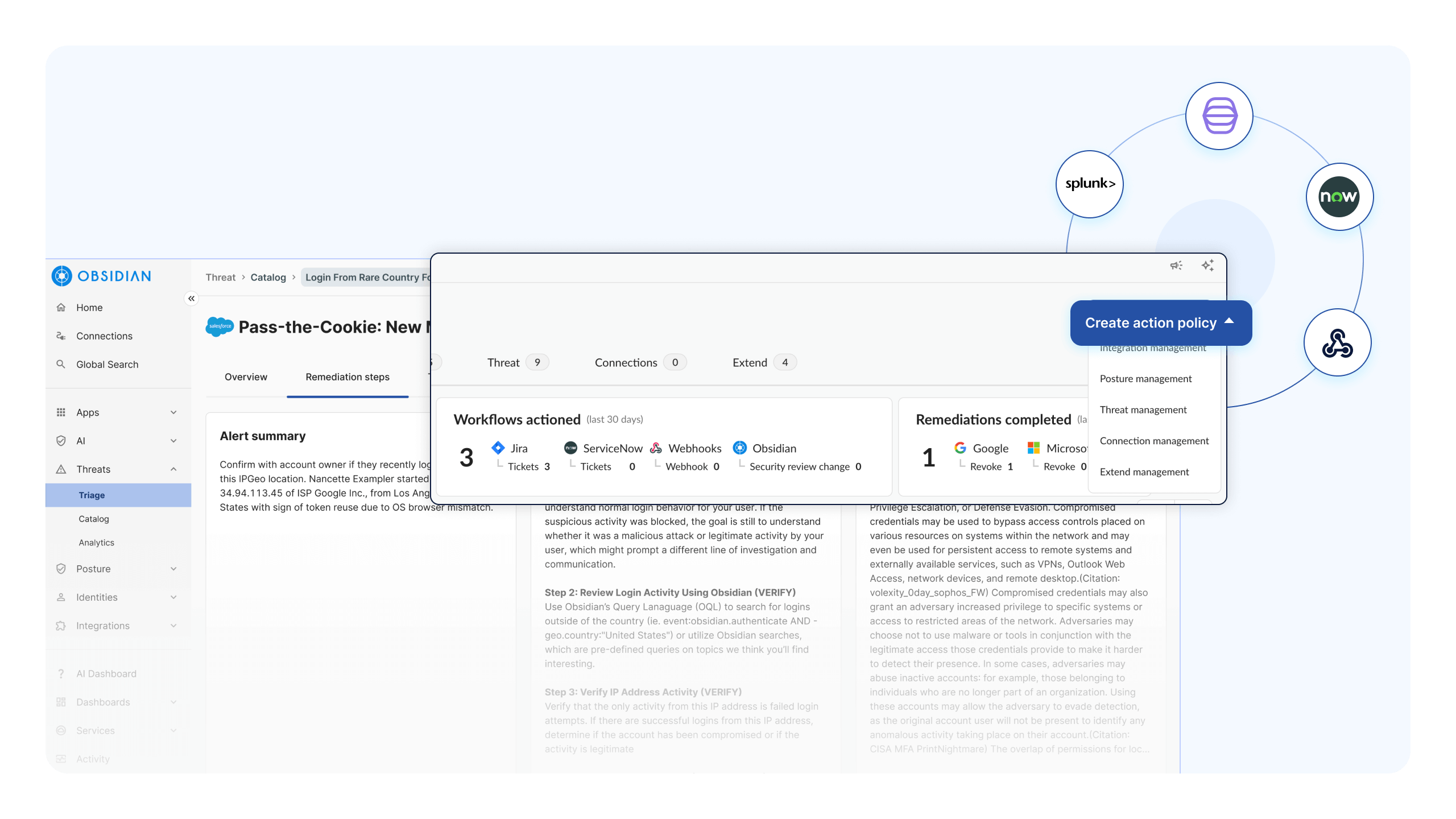
See Obsidian in action
To discover more on how you can secure your SaaS supply chain, check out some of our resources below or if you have any questions, we would love to chat!
- Watch our on-demand explainer video to see how Obsidian protects your SaaS supply chain.
- Join our webinar on the hidden risks behind your SaaS supply chain featuring security experts from Workday, S&P Global and Obsidian Security and get practical guidance from experts on how you can get started. Save your spot!


.png)
.png)