

Local SaaS logins create an easy path around SSO and MFA. Spot and eliminate misconfigured access policies so every user authenticates through secure controls.
Of SaaS apps are not behind SSO
Of SaaS that have local login access sensitive data
Increase in SaaS without SSO controls every three months
Find and eliminate every direct authentication path between users and SaaS to enforce strict, consistent access controls through your identity perimeter.
GET A DEMOEasily spot local access misconfigurations and SSO bypass.
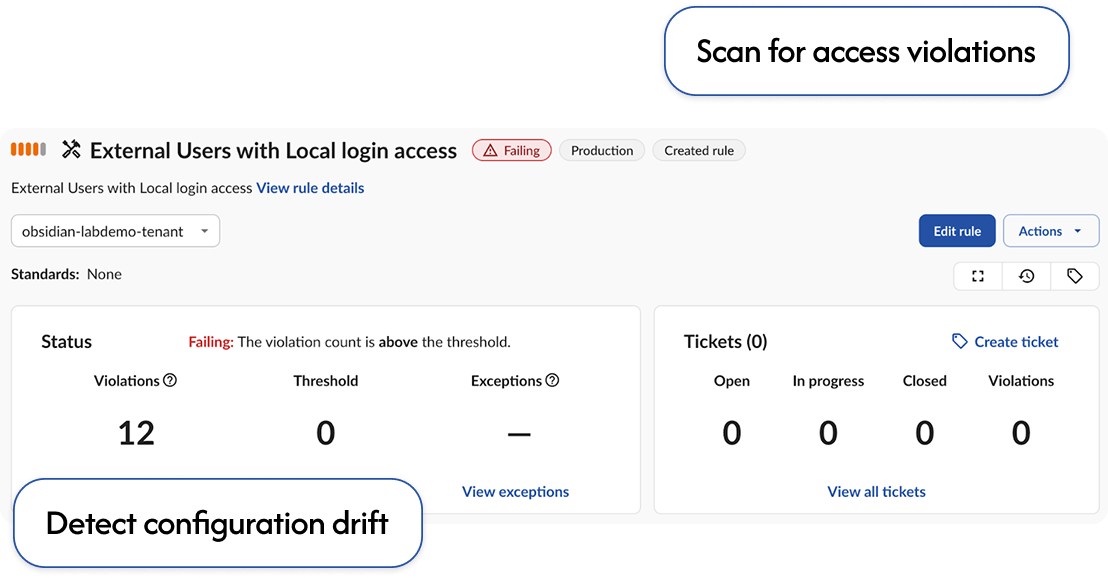
Fix misconfigurations that allow authentication by legacy accounts.
Bring every app and account in compliance with access policy.
Find and secure unmanaged SaaS and block unsanctioned apps.
Review misconfigurations that allow local authentication and global policy bypass, including for legacy accounts.
reduction in SaaS attack surface
Bring hidden SaaS under centralized access controls to enforce secure authentication and compliance.
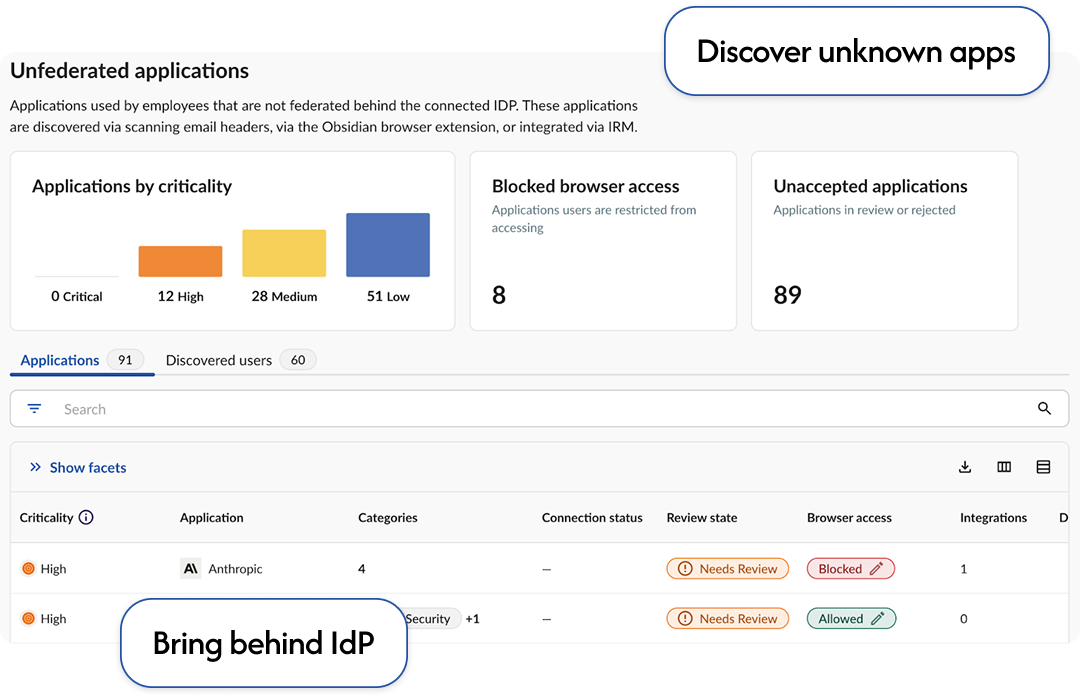
Shadow SaaS discovery
Spot evidence of direct login events to secure user authentication.
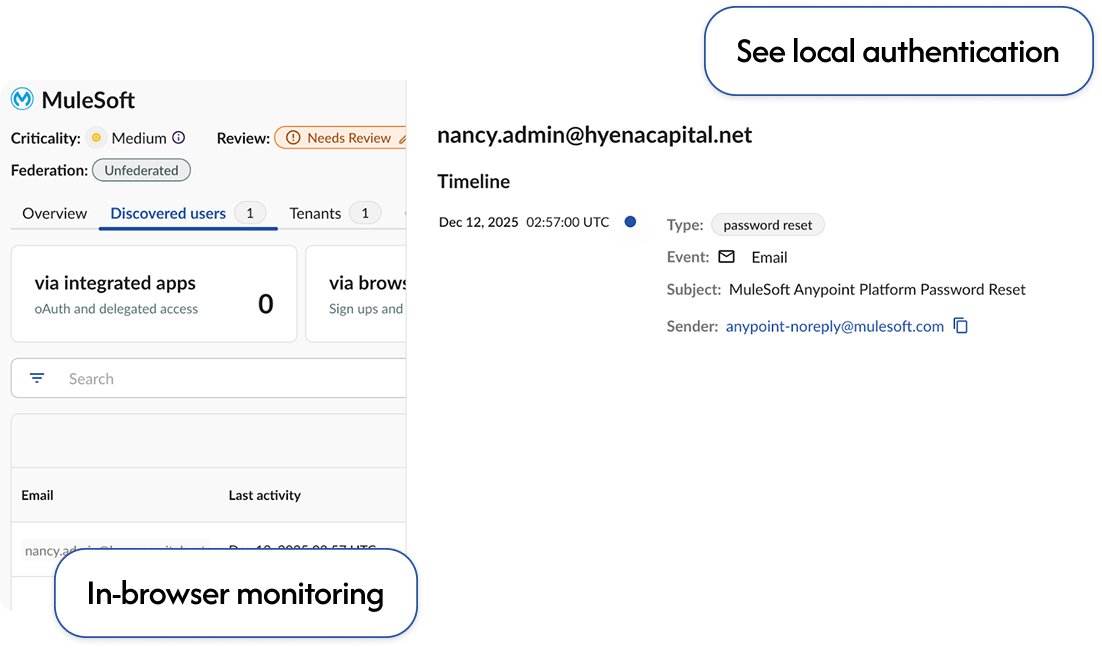
users protected