SaaS didn't just change how we work, it changed our approach to security.
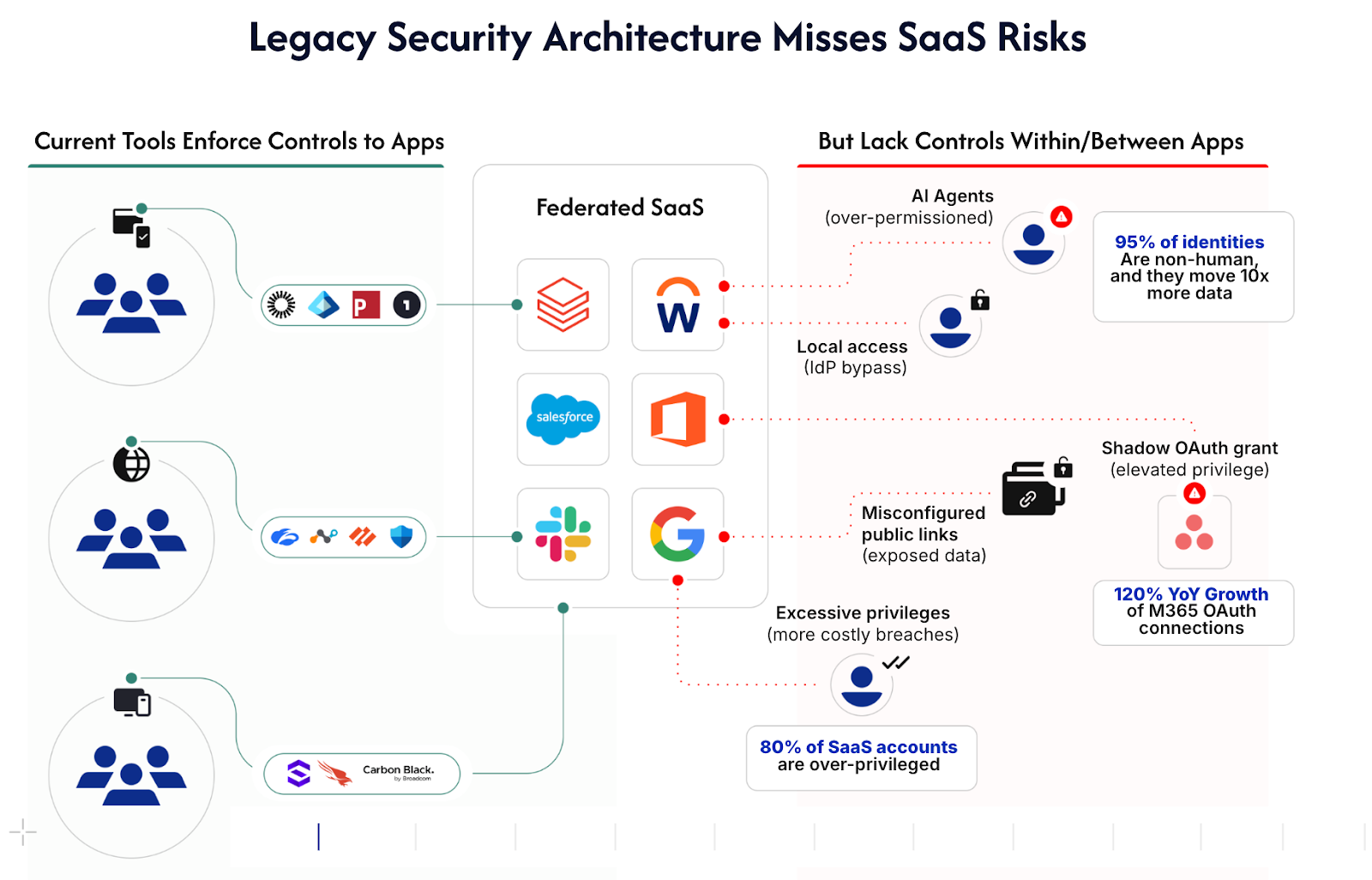
Every enterprise now relies on SaaS applications for everything from strategic planning to workflow automation. Yet, traditional security approaches focus on controlling the perimeter by maintaining strict controls around who can access what, and from where. IAM platforms like Okta and SASEs like Netskope excel at this but lack visibility and context to secure where risk actually lives today: inside SaaS.
As business units rapidly adopt new SaaS and AI tools, security teams grapple with a number of challenges:
- How do I block risky OAuth integrations my SASE can't even see?
- How do I stop service accounts from exfiltrating data when they're just as invisible?
- How can I address misconfigurations inside apps my EDR wasn’t designed to monitor?
- How can I see if a user is accessing sensitive data if they’re on a personal, unmanaged device?
Being able to answer questions like these isn't just useful. It's essential.
SaaS supply chain attacks are growing in frequency and impact. In the recent Salesloft-Drift breach, attackers exploited a third-party integration to turn a single compromised vendor into a gateway that affected 700+ companies.
Traditional security tools and Zero Trust solutions weren't built to address this. They monitor networks, devices, and cloud infrastructure, but they can't trace how a risky OAuth token moves between apps, how a misconfiguration creates silent privilege creep, or how an AI agent chains access across multiple SaaS tenants. Without purpose-built SaaS security, teams stay blind to the blast radius and can't protect the enterprise where modern risk really lives: inside the SaaS apps themselves.
This article walks through the modern security architecture, what different solutions offer and the critical gap that SaaS security fills.
At a Glance: Why Can’t Legacy Tools Secure SaaS?
The fundamental issue is this: traditional security assumes access happens through users logging in from devices on networks. But in SaaS environments, access increasingly occurs through tokens, agents, and automations that operate inside the applications themselves, creating blind spots for tools that only monitor external traffic and endpoints.
Your existing security stack protects users, devices, and networks. But it can't see how identities, permissions, and integrations within SaaS applications intersect to form the real attack pathways adversaries exploit.
Here’s a quick overview of what each layer solves and where it leaves gaps.
Going Deeper: Where Existing Tools Add Value and Leaves Gaps
IdPs like Okta, Microsoft Entra ID, and Ping authenticate users and federate access via SSO using SAML and OIDC. They enforce MFA at login and centralize identity management across your federated applications.
But IdPs only control what flows through them. Service accounts, direct logins, and OAuth tokens? They authorize access directly between applications, bypassing your SSO and MFA entirely.
CASBs like Netskope, Zscaler, and Palo Alto Prisma Access act as control points between users and cloud services. They route traffic through secure points of presence, restrict SaaS access to managed devices, and provide visibility into cloud application usage through API connections and inline proxies. They enforce security policies and data loss prevention at the network layer.
But CASBs operate at the traffic layer. OAuth integrations bypass CASBs entirely, connecting applications directly without touching your network controls. Shadow SaaS and unmonitored integrations create blind spots in your visibility.
SIEMs like Splunk, Chronicle, and Microsoft Sentinel centralize and correlate events across your security stack, aggregating logs, applying detection rules, and surfacing anomalies for event-based threats.
The limitation is that SIEMs are good at data centralization and correlation to detect anomalous activities, yet fail to map access paths within applications. Understanding who has admin rights across multiple apps requires a relational model spanning permissions, groups, and entitlements that SIEMs weren't built to maintain.
EDRs like Microsoft Defender for Endpoint and CrowdStrike detect malware and endpoint compromise by monitoring process execution, file system changes, and network connections on managed devices. Yet EDR is bound to the endpoint and can't see in-app configurations. Service accounts and API keys operate at the application layer, authenticating between systems without ever touching a monitored device.
The Gap Obsidian Fills
Obsidian understands that modern risk doesn't live in isolated SaaS and AI applications. It lives in the connections between them.
That's why we approach the problem through a knowledge graph that maps how identities, entitlements, and activity actually connect across your SaaS estate. We start by leveraging our deep expertise in SaaS data collection, gathering comprehensive information from across your applications. Then we build the relationships between that data, connecting users, tokens, permissions, and resources into a unified model. Rather than treating each app as a separate system, this approach lets you clearly understand who has access to what, how they got it, and how that access is distributed with verifiable, human-readable evidence.
This isn't about collecting more data. It's about understanding the relationships that drive risk. When a service account holds dormant admin rights, when an OAuth integration has excessive scopes, when an AI agent inherits permissions across tenants, the graph shows it. More importantly, it reveals the path attackers could take and the controls needed to stop them.
This approach transforms complex security questions into clear, actionable outcomes.
- Detect insider misuse and offboarding gaps by mapping actual access across all your SaaS applications, not just federated ones
- Expose overprivileged integrations across your SaaS supply chain before they become attack vectors
- Identify local access and shadow SaaS activity early, even from unmanaged devices
Final Thoughts
SaaS made modern business possible. But it also created risks legacy tools were never designed to solve. In the era of AI agents and autonomous workflows, SaaS security isn't a nice-to-have. It's a must-have.
Want to learn more about Obsidian’s approach? Check out this article: From SaaS Sprawl to a Knowledge Graph.
To see how we bring that vision to life, request a demo.




