In today’s cloud-first world, adopting SaaS applications accelerates productivity, but it also introduces new SaaS security risks. A dangerous misconception persists that a vendor like Salesforce, Google, or Microsoft handles every aspect of SaaS security. In reality, security is a shared partnership.
Your vendor secures the infrastructure, while your business must apply SaaS security best practices to protect data, identities, and configurations. In short: they secure their platform, not your business.
This widespread misunderstanding of security ownership leads to significant posture gaps and is the root cause of many SaaS-related security incidents.
- Microsoft disclosed a critical breach carried out by the Russian state-sponsored group Midnight Blizzard against their Office 365 instance due to an unsecured tenant
- In 2024, Snowflake was in the news due to attacks targeted at 165 customer-owned systems where misconfigured MFA settings allowed unauthorized access
- Hundreds of organizations leaked private data via a Salesforce misconfiguration, exposing sensitive data to external individuals or groups
- Obsidian Security was involved in over 150 incident responses last year related to SaaS compromises—up 300% year-over-year
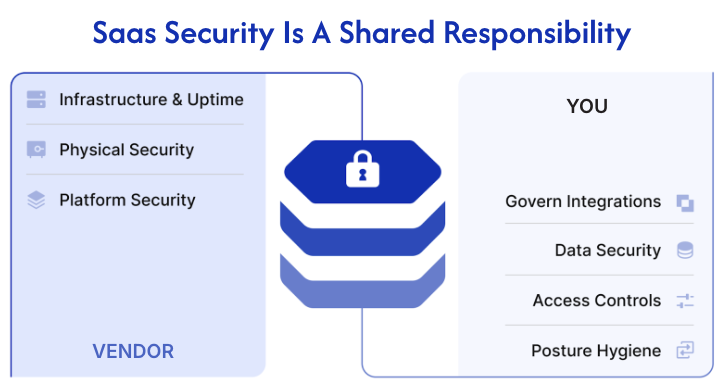
What is the SaaS Security Shared Responsibility Model?
The SaaS security shared responsibility model is a framework that delineates vendor versus customer duties for securing cloud-based applications and the data they hold. Rather than shifting all risk to one party, it defines a partnership where both the SaaS vendor and the customer have distinct, yet interconnected, security duties.
Why Businesses Misunderstand SaaS Security
The ease of deploying and using SaaS applications often lulls businesses into a false sense of security. An employee can sign up for a new SaaS tool, integrate it with other core applications, and start using it within minutes. This convenience, while powerful, doesn't come with built-in, out-of-the-box security for how you use the service.
The misconception stems from a fundamental misunderstanding of the "security of the cloud" versus "security in the cloud":
- Security "of" the cloud: This is the vendor's domain.
- Security "in" the cloud: This is the customer's responsibility.
Because SaaS vendors handle the underlying infrastructure, it's easy to mistakenly believe they handle everything. And because most app owners are not security minded, they may be unaware of their role in securely deploying these applications, or how misconfigurations can drift over time and create even more risk.
This unawareness of the shared responsibility model leaves SaaS applications vulnerable to misconfigurations, excessive privileges, and data exposure.
What SaaS Vendors Secure
SaaS providers are responsible for securing the foundational elements of their service. Their responsibilities typically include:
- Application Infrastructure: The physical security of their data centers, servers, networking hardware, and the underlying infrastructure that hosts the SaaS application.
- Platform Security: Ensuring the operating systems, databases, and core application code are secure, patched, and up-to-date. This includes vulnerabilities management and secure development practices for the application itself.
- Application Availability and Uptime: Maintaining the core functionality and accessibility of the SaaS service.
Essentially, the SaaS vendor ensures the service works and that the environment it runs on is secure.
What Your Business Must Secure: SaaS Security Best Practices
This is where your critical responsibilities lie. While the vendor provides the secure platform, how you use, configure, monitor, and manage access to that platform is squarely your responsibility. Ignoring these areas creates dangerous security gaps.
Your business's key responsibilities include:
- Data Security: Controlling who can view, modify, or share specific data within the application.
- Identity and Access Management (IAM): Managing user accounts from creation to termination, enforcing multi-factor authentication (MFA) and strong password policies, and granting users only the minimum permissions necessary.
- Configuration Management: Properly configuring the hundreds, sometimes thousands, of security settings and features within each SaaS application. Cloud misconfigurations are a leading cause of breaches.
- Third-Party Integrations: Ensuring any third-party applications you connect to your SaaS tools are secured and aren’t overly permissioned, allowing easy lateral movement across your environment.
- User Behavior & Awareness: Tracking suspicious user behavior within SaaS platforms.
- Compliance: Ensuring your usage of SaaS applications adheres to relevant industry regulations (e.g., GDPR, HIPAA, SOC 2) and your internal security policies. While the vendor may be certified, your usage must also comply.
Why SaaS Security Is Absolutely Necessary
The reality is that SaaS applications are not inherently secure out of the box in terms of your specific data and configurations. While they offer robust foundational security, the onus of securing your side of the shared responsibility lies entirely with your business.
Ignoring this can lead to:
- Data Breaches: Misconfigured settings or compromised credentials can expose sensitive data.
- Compliance Violations: Failing to manage data access or retention can lead to hefty fines.
- Operational Disruptions: Unauthorized changes or malicious activity can disrupt business processes.
- Reputational Damage: Losing customer or proprietary data can severely impact your brand.
How The Obsidian Security Platform Secures Your SaaS Ecosystem
Understanding the shared responsibility model is one thing; effectively applying it across your entire SaaS estate is another. The challenge often lies in the sheer volume of SaaS applications, the complexity of their security settings, and the fact that many business users are not security experts.
This is precisely where platforms like Obsidian become indispensable.
Obsidian helps bridge the "security in the cloud" gap by providing comprehensive visibility and control over your SaaS security posture. We enable businesses to:
- Discover Shadow IT & Integrations: Identify all SaaS applications in use and their connections.
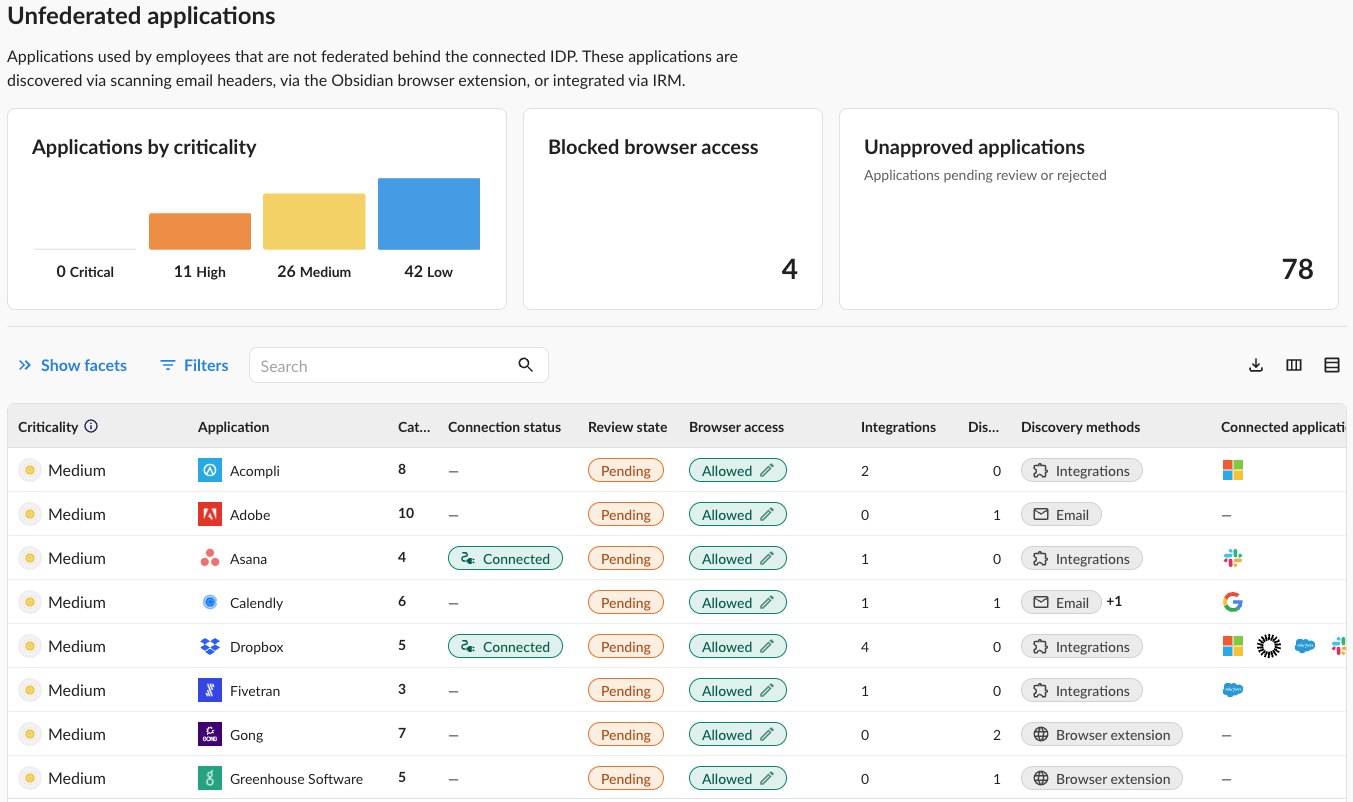
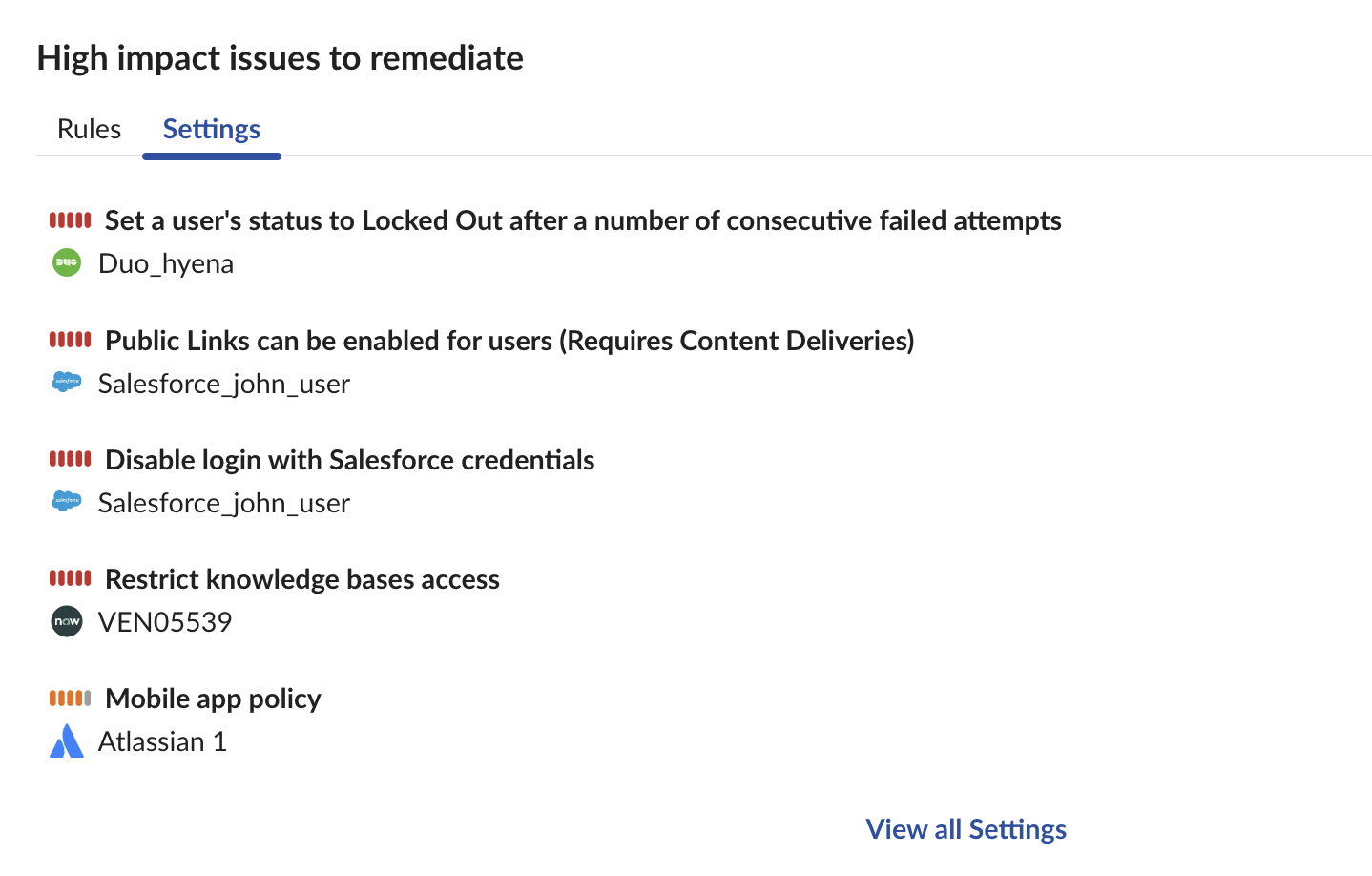
- Continuous Configuration Monitoring: Automatically detect misconfigurations and insecure settings across your SaaS stack, highlighting vulnerabilities before they can be exploited.
- Granular User Behavior Analytics: Monitor user activity, identify anomalous behavior, and detect compromised accounts or insider threats.
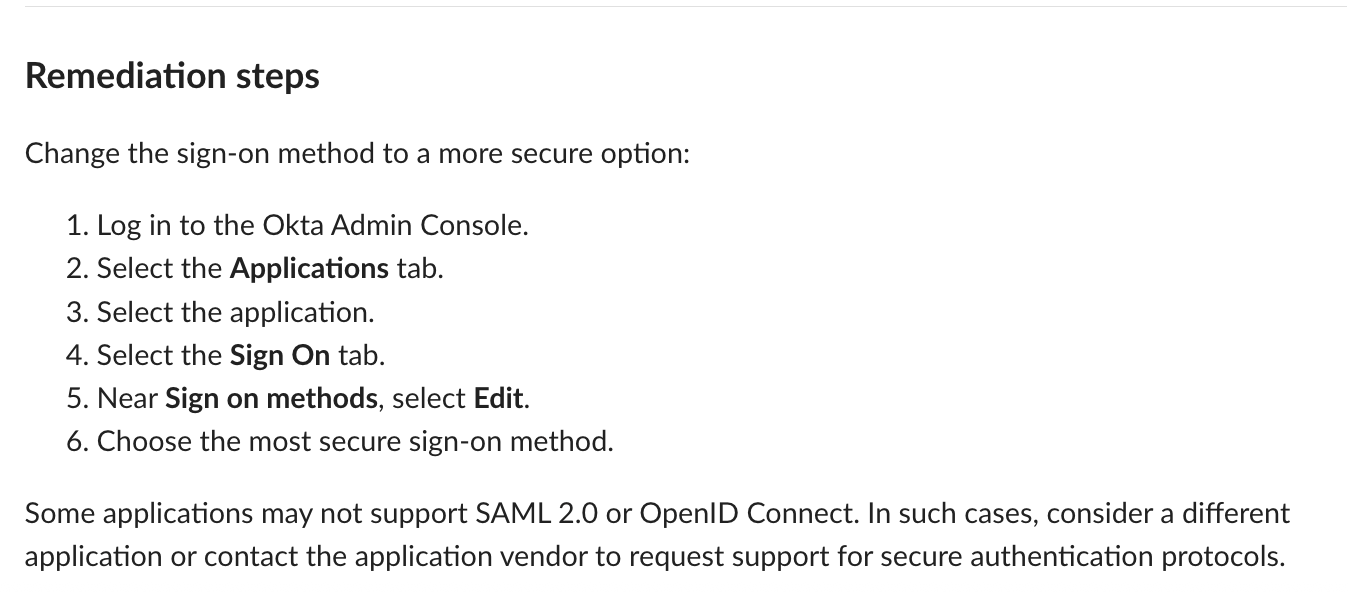
- Automated Remediation: Take swift action to correct security posture issues and enforce best practices.
- Role-Based Access Controls: Protect sensitive data and curb internal threats with robust RBAC to limit app owners from viewing data beyond just their instance
- Centralized Access & Permission Management: Gain a unified view of all user access, roles, and permissions across your SaaS applications, ensuring least privilege is enforced.
Don't leave your SaaS security to chance. Take control of your shared responsibility with a purpose-built SaaS security solution.
Ready to strengthen your SaaS security posture and ensure you're meeting your side of the shared responsibility? Start your free trial today.




