

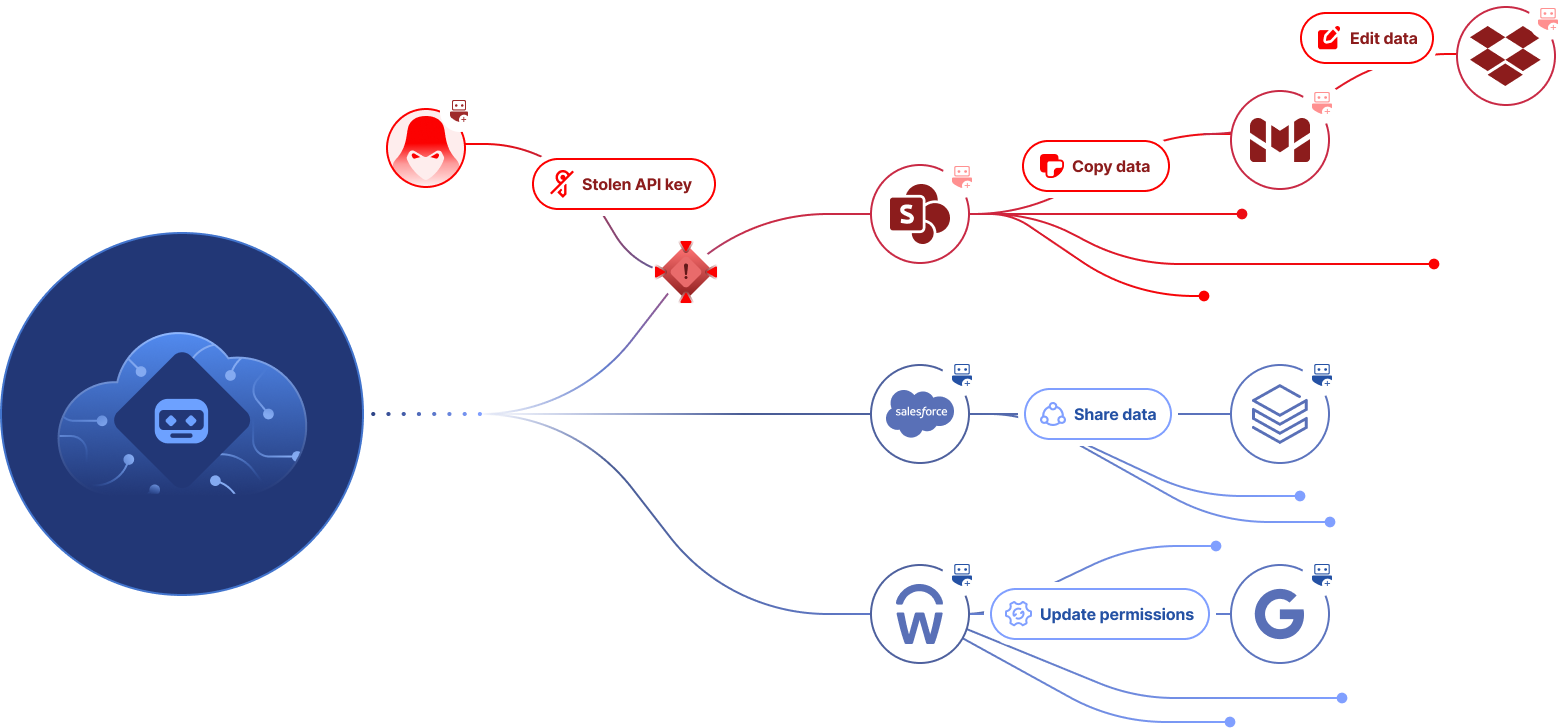
Criminal groups like ShinyHunters are leveraging stolen OAuth tokens to compromise app-to-app integrations into Salesforce and steal sensitive customer data. These SaaS supply chain attacks can affect hundreds of organizations, because when a SaaS vendor is compromised, threat actors can exploit the direct connections customers make into their Salesforce environments to access data.
In August 2025, Salesforce breaches via the Salesloft–Drift integration impacted over 700 companies. In November 2025, attackers claim to have accessed roughly 285 additional Salesforce instances after compromising Gainsight, with stolen tokens and secrets from the earlier Salesloft–Drift supply-chain compromise.
.png)
Obsidian Security protects businesses from SaaS supply chain attacks targeting Salesforce integrations with proactive visibility and management of app-to-app risk, and unique threat alerts built on real-world data.
of organizations have local login enabled
Obsidian Network Data
Of SFDC tenants have publicly-exposed files
Obsidian Network Data
organizations leaked private data via misconfigured SFDC accounts
KrebsOnSecurity
A ‘do-it-yourself’ approach to Salesforce security creates unmanageable complexity and misses critical gaps.

