Reduce risky integrations, detect supply chain abuse early and contain impact quickly.

Increase in breach impact when attackers exploit third party integrations
Organizations breached through the Salesloft-Drift integration to critical SaaS apps
Increase in third party breaches year over year
Expose the attack surface, reduce integration risk, detect compromises early and contain impact quickly.
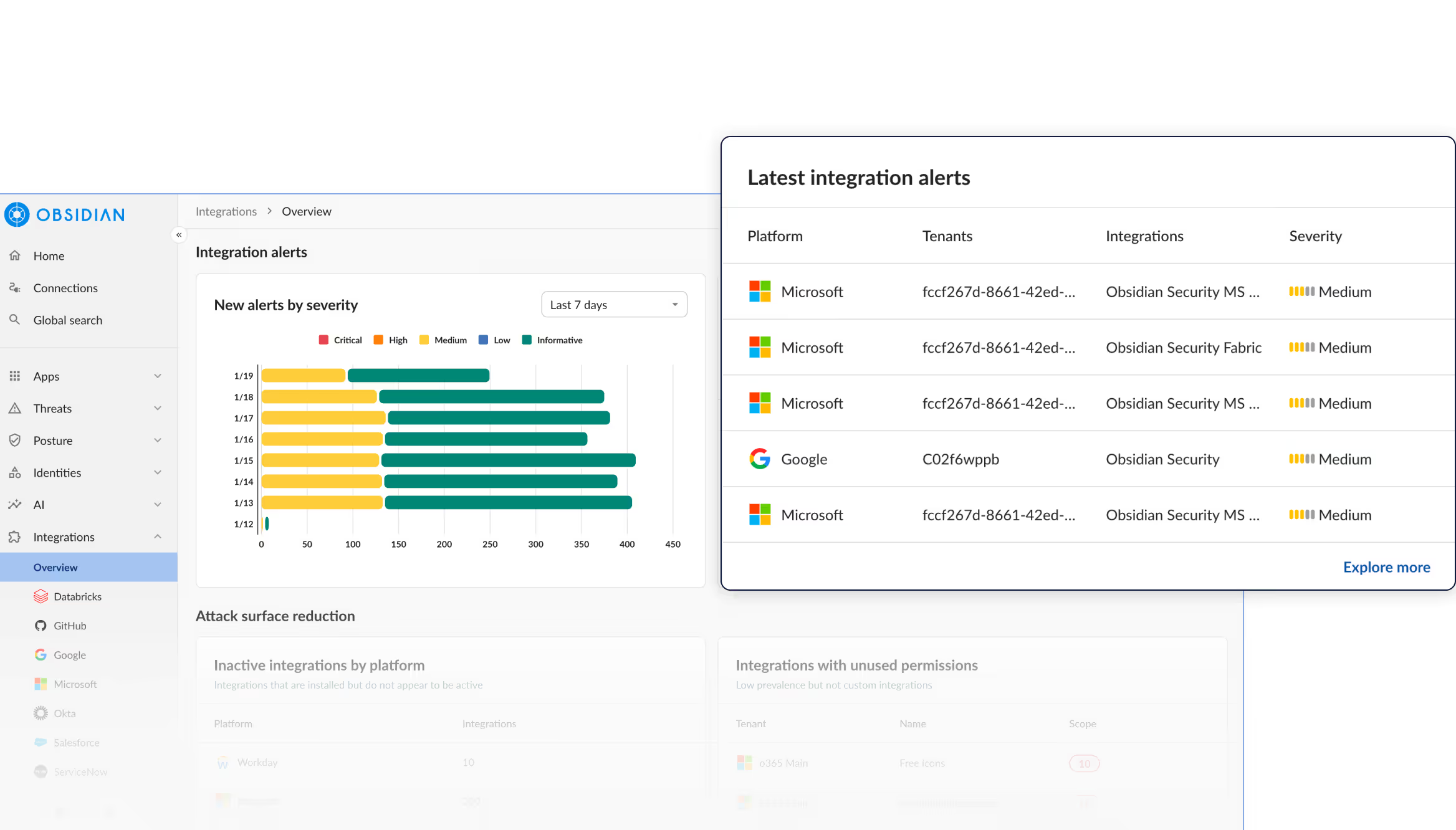
See the productInventory every SaaS integration, including shadow apps, to know exactly who and what has access to your data
Identify risky connections and enforce least privilege to shrink blast radius before attackers exploit it
Spot abuse the moment integrations behave abnormally, before an application breach spreads downstream
Get instant impact clarity on affected apps & attack paths visibility to contain exposure and respond with confidence
See every SaaS integration, understand the risk it introduces, and act quickly when something goes wrong.
Get A DemoDiscovers every SaaS-to-SaaS integration, including OAuth apps, APIs, non-human identities, and shadow SaaS for an unified view of who and what has access to your data
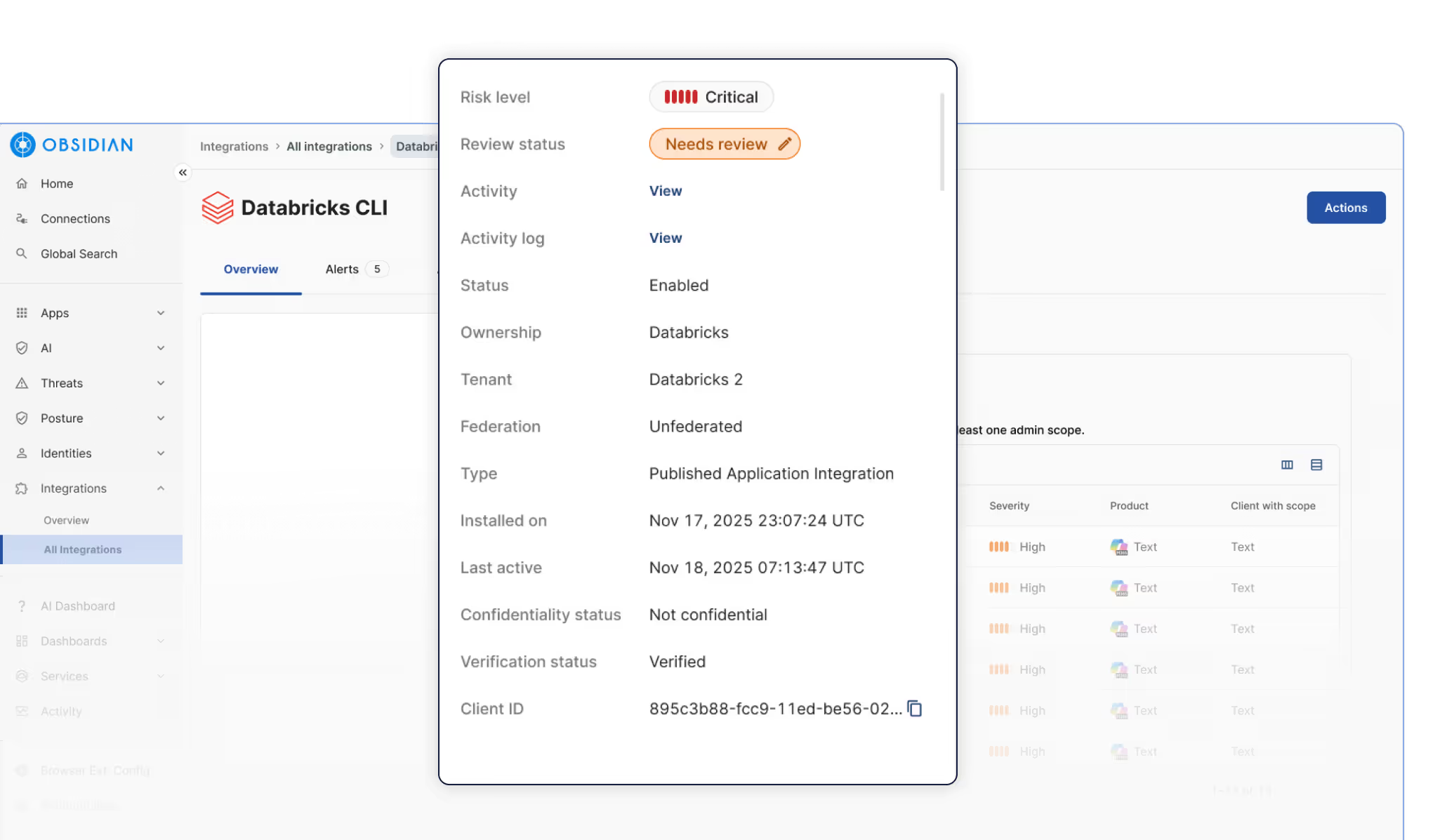
Replace manual reviews and spreadsheets to identify and prioritize risky integrations using real activity and identity context. Enforce least privilege by removing risky integrations to reduce the blast radius before risks escalate into a cascading breach
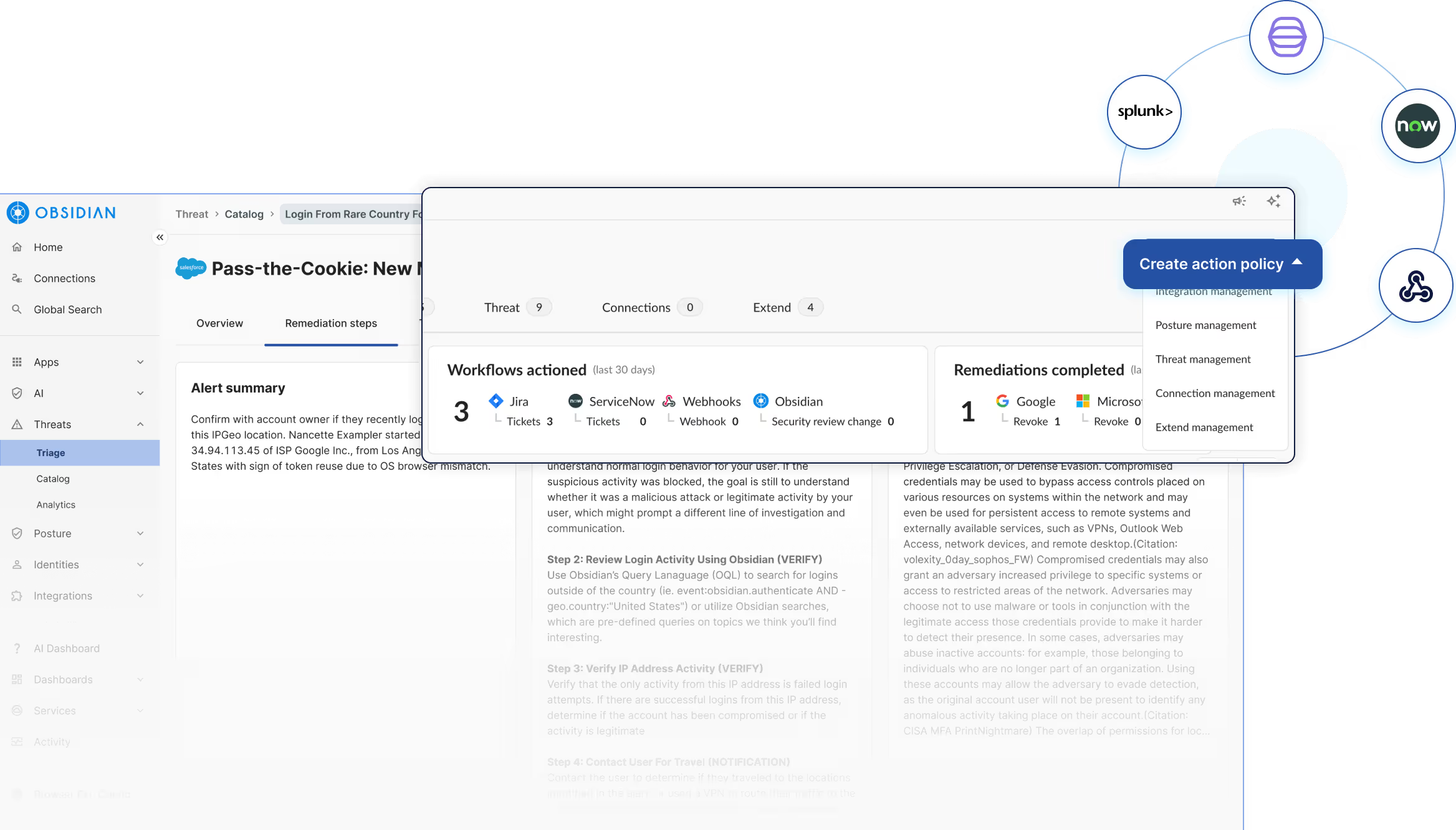
Detect early indicators of compromise the moment trusted SaaS integrations deviate from normal behavior. Correlate these signals with real threat intelligence to surface suspicious activity early and expose supply chain attacks that other tools miss.
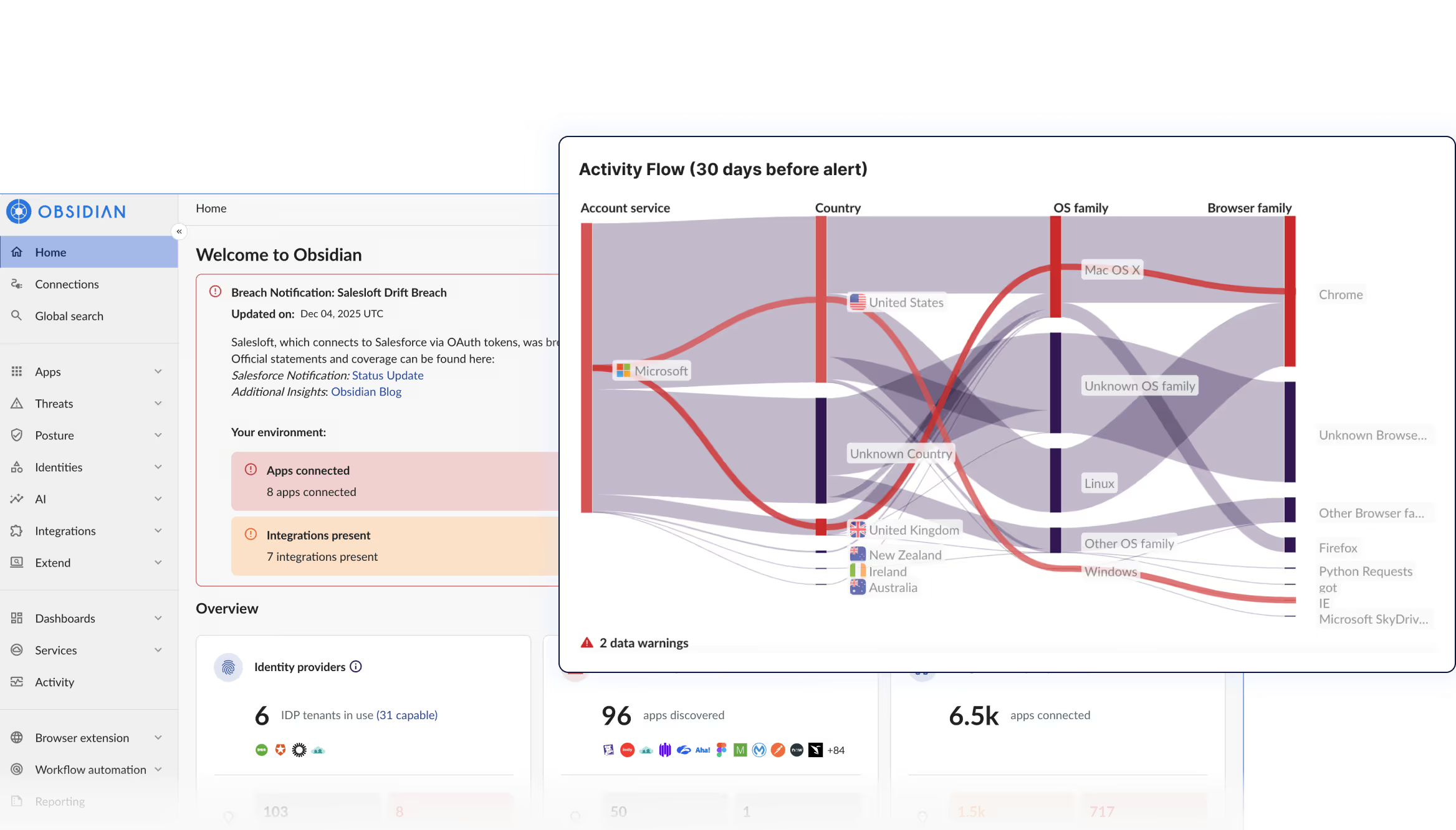
No more cross-SaaS log stitching. Get instant clarity when an incident occurs with guided remediation and incident summaries. See affected apps, attack paths, and actors in a unified timeline for fast, confident forensics, containment, and response.