

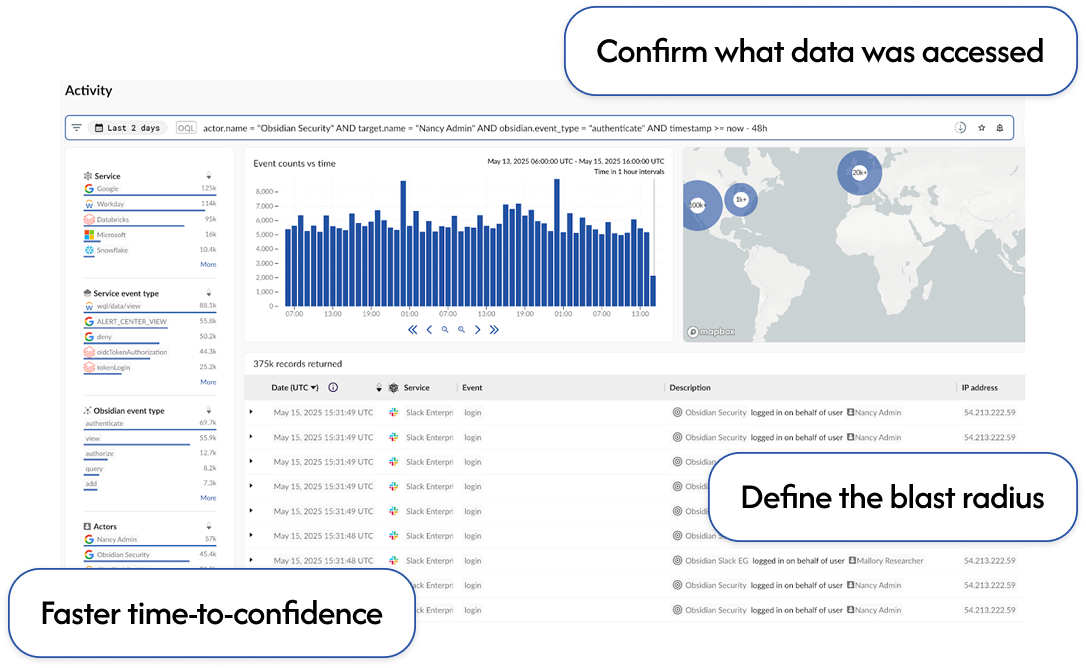
SaaS breaches force a race to prove scope and impact. Get investigation-ready evidence to confirm what was accessed, where activity stopped, and make defensible disclosure decisions fast.
Attack-to-exfiltration can happen in minutes, leaving little time to respond
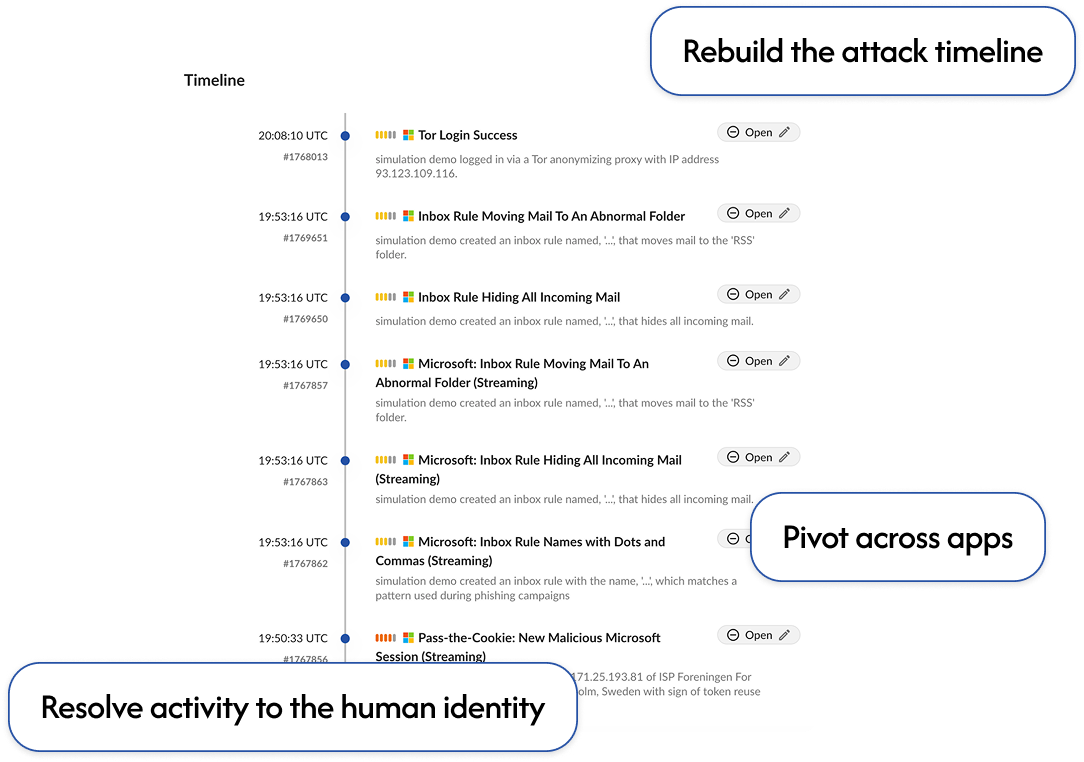
Identify and contain cloud breaches
Estimated profit impact for M&S while scope and impact were unclear
Unify SaaS evidence, resolve actions to real identities, and reconstruct attacker timelines so responders can prove scope and impact fast, without SIEM stitching.
GET A DEMOSee SaaS activity, access changes, sessions, tokens, and integrations across connected apps in one investigation view.
Link accounts, sessions, and OAuth tokens back to the real human identity and privilege context behind the activity.
Automatic breach timelines across apps to cut manual log stitching, exports, and reconstruction.
Reduce SIEM ingest and custom pipeline burden without slowing investigations or losing coverage.
Reconstruct attacker activity across SaaS identities, access paths, and data.
faster MTTI
Determine material impact without guesswork or overreach.
Cut SIEM spend by up to