Protect user credentials from AI-powered phishing and browser-based attacks














AI-powered local web inspection ensures users only interact with real login pages. Detect and prevent credential submissions to fake phishing sites to protect your corporate accounts, OAuth tokens, and sessions with browser-level security.
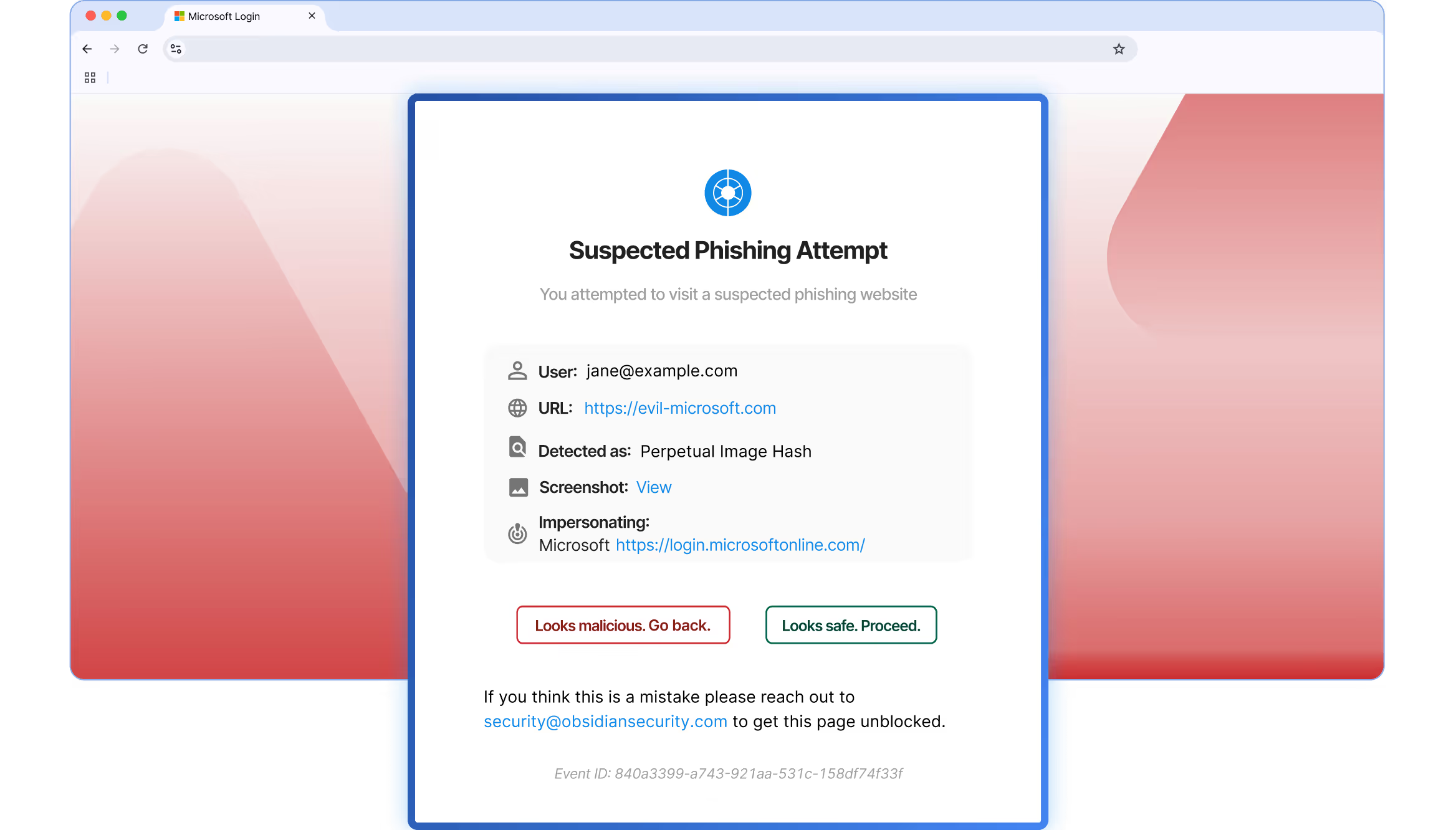
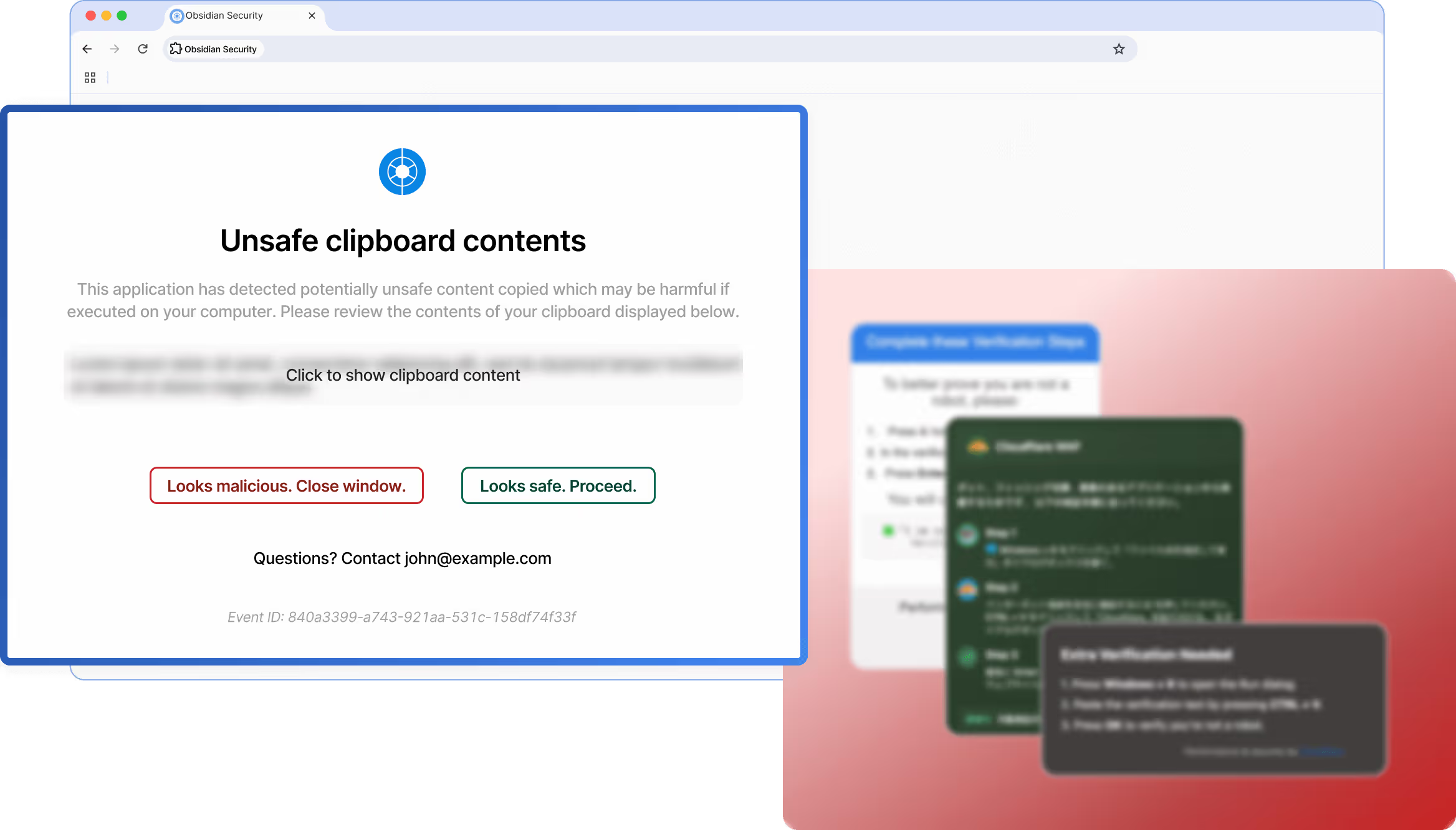
Ensure users interact with safe login pages to prevent account takeover attacks that bypass phishing-resistant MFA using tactics like deceptive CAPTCHAs delivered through search engines. Block session hijacking with AI-powered web detections and real-time alerts that warn users or stop them from clicking on malicious sites.
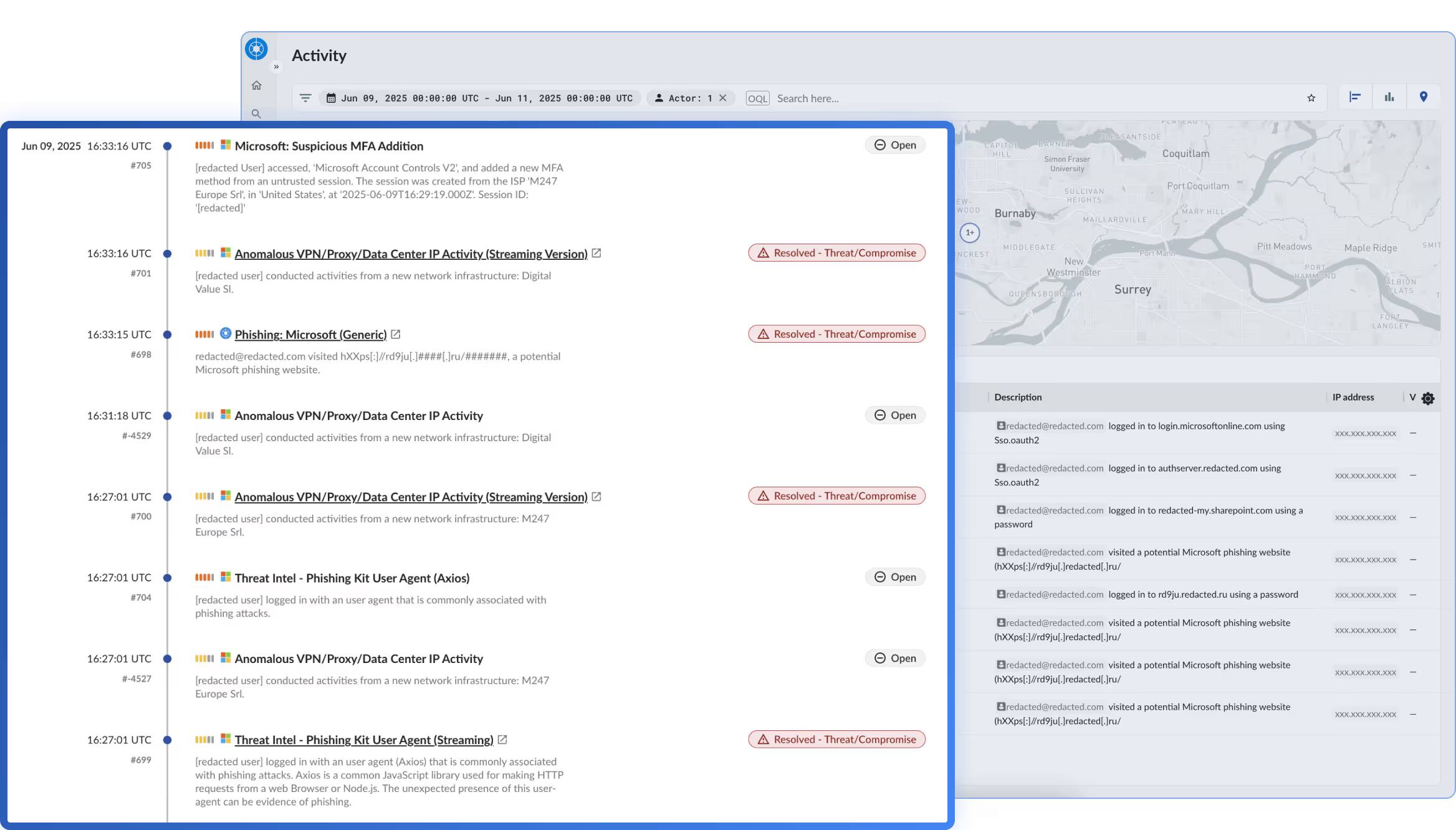
Monitor threat actor activity across the browser and SaaS to generate an immediate forensic trail for incident response. Pivot across systems to assess impact and execute rapid, targeted remediation in minutes.