

Compromised SaaS accounts let attackers sneak in, steal data, and pivot across your environment undetected. Quickly detect and contain these identity attacks before impact escalates.
Rise in SaaS breaches
SaaS incidents begin with compromised identity
Breaches are not detected internally
Bring all SaaS activity and threat signals into a single platform to improve time to detection, investigation, and remediation across SaaS.
GET A DEMOShift left with in-browser prevention to stop account takeover before it begins.
Near real-time detections built for SaaS and informed by real world threat intelligence.
Easily follow attack paths on the only platform trusted by leading incident response firms for SaaS.
Detailed instructions and actionable steps to contain compromises before they spread deeper into SaaS.
Prevent users from submitting their credentials into phony phishing sites.
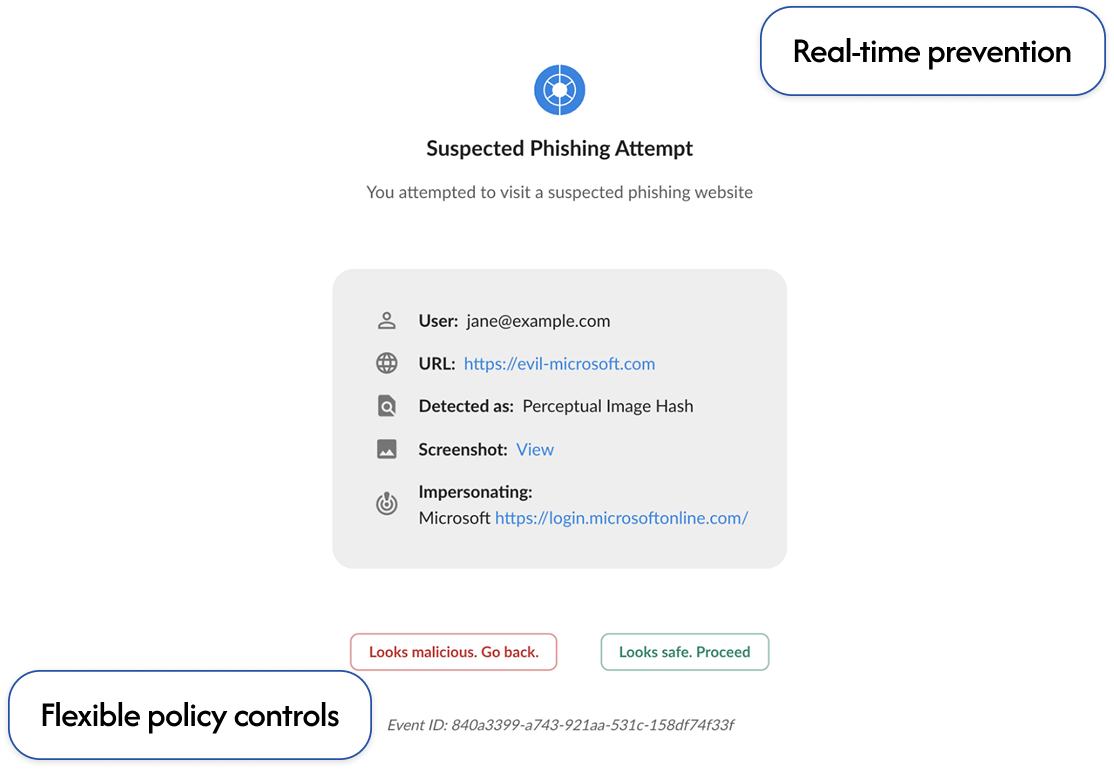
block rate against popular phishing kits like Evilginx and Tycoon
Get high-fidelity, true-positive security alerts the moment your SaaS events are processed, tuned by learnings from 500+ SaaS IRs.
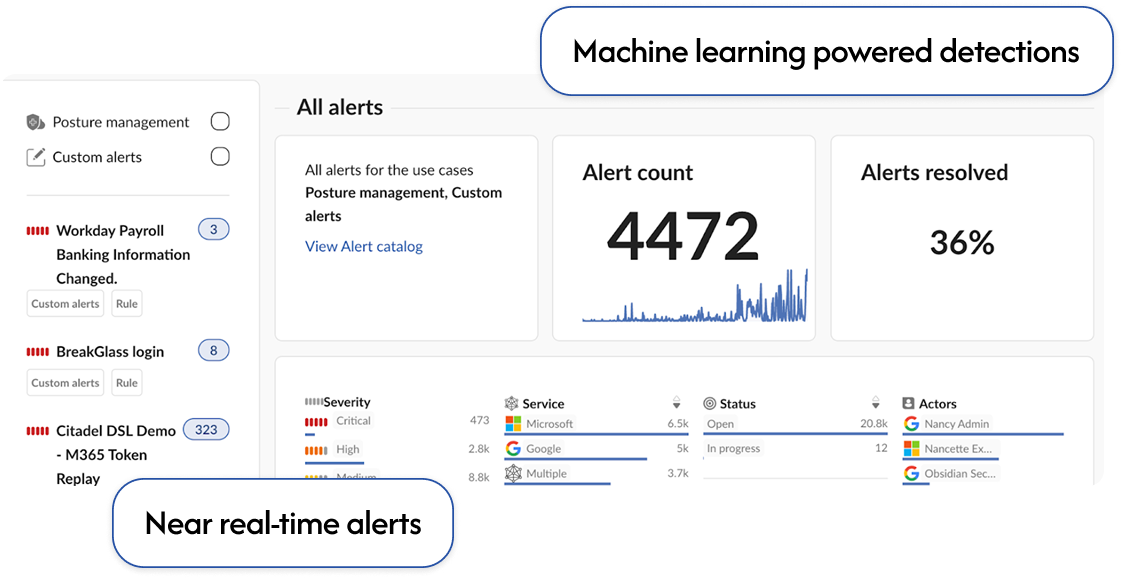
identity threat detection
Speed up investigations with clear timelines and alerts categorized using the MITRE ATT&CK framework.
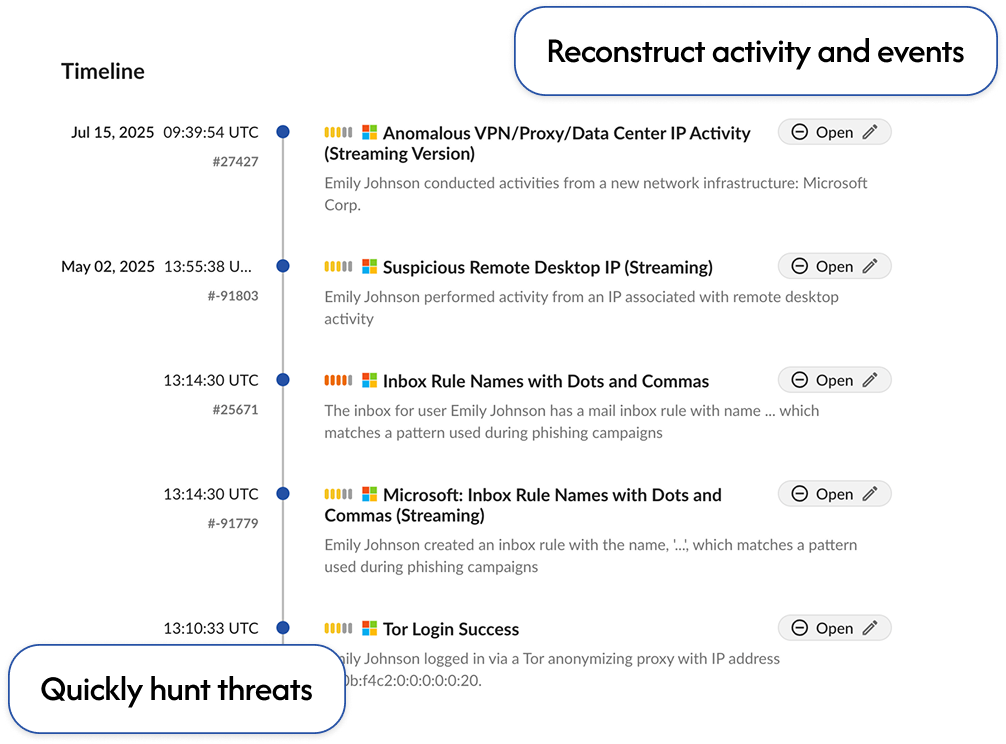
Reduce MTI by up to