

Fix misconfigurations, remove high-risk integrations, and stop malicious activity before it spreads across SaaS.
Increase in monthly SaaS breaches
SaaS accounts have excessive privileges
Shadow SaaS accesses sensitive data
Get the visibility, detections, and guidance needed to ensure every app, account, and setting is secured across your SaaS.
See the productEnd-to-end observability across your SaaS estate with discovery of hidden access points.
Avoid audit findings and regulatory supervision with secure configuration and access controls for every app.
Consolidated threat feeds with immediate and actionable intelligence to combat attacks to your SaaS.
Apply security policy and governance controls uniformly across AI to confidently adopt new technologies.
Harden controls across SaaS to enforce least privilege and stop SSO bypass to shadow SaaS and local accounts.
Control SaaS permissions →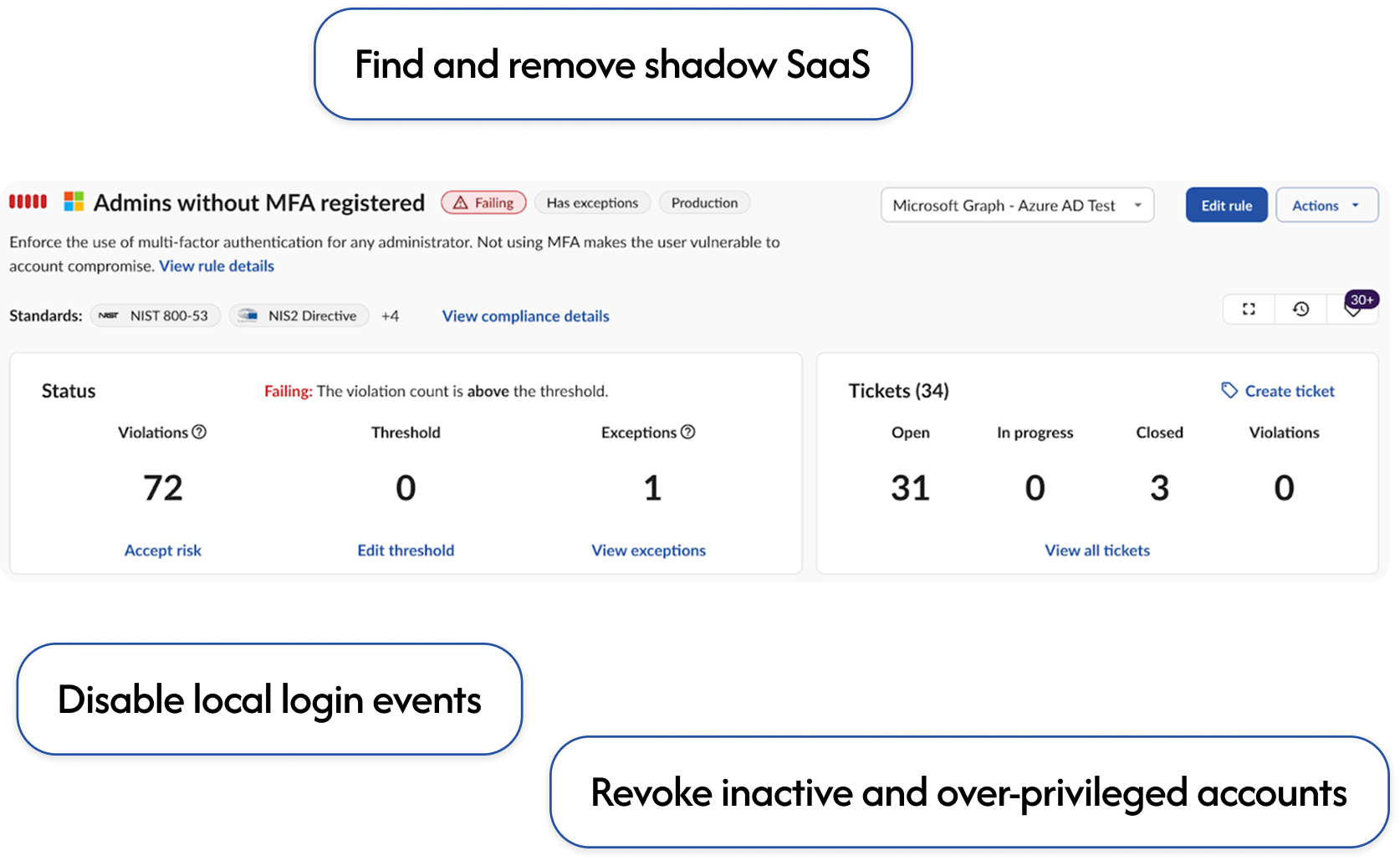
reduction in over-privileged accounts
Stop intrusions from your SaaS supply chain by removing risky integrations and detecting suspicious behavior before public breach notifications.
Stop supply chain attacks →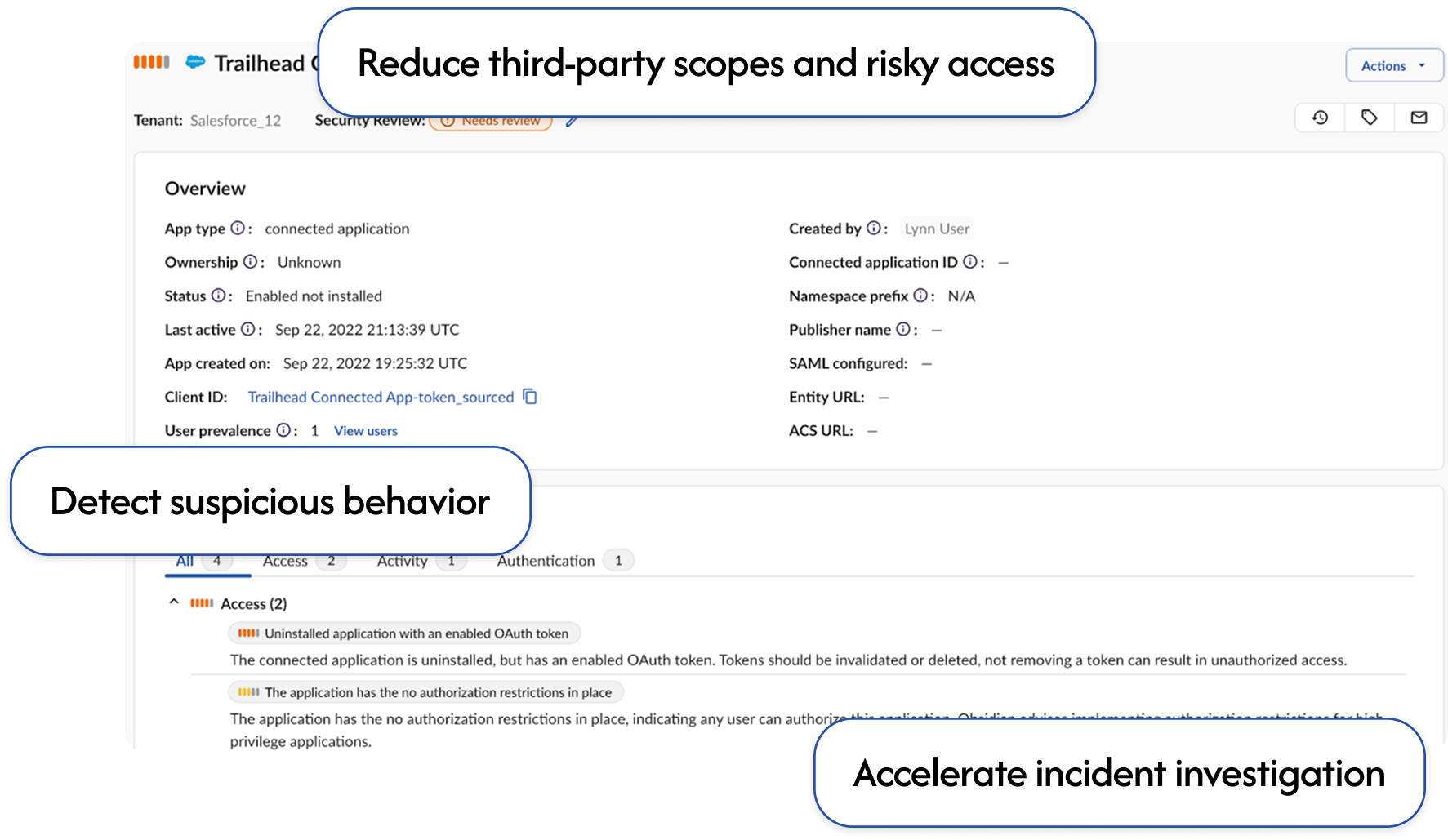
decrease in SaaS attack surface
Secure autonomous workflows at scale by detecting and removing risky or unauthorized AI agent actions in SaaS.
Govern agent workflows →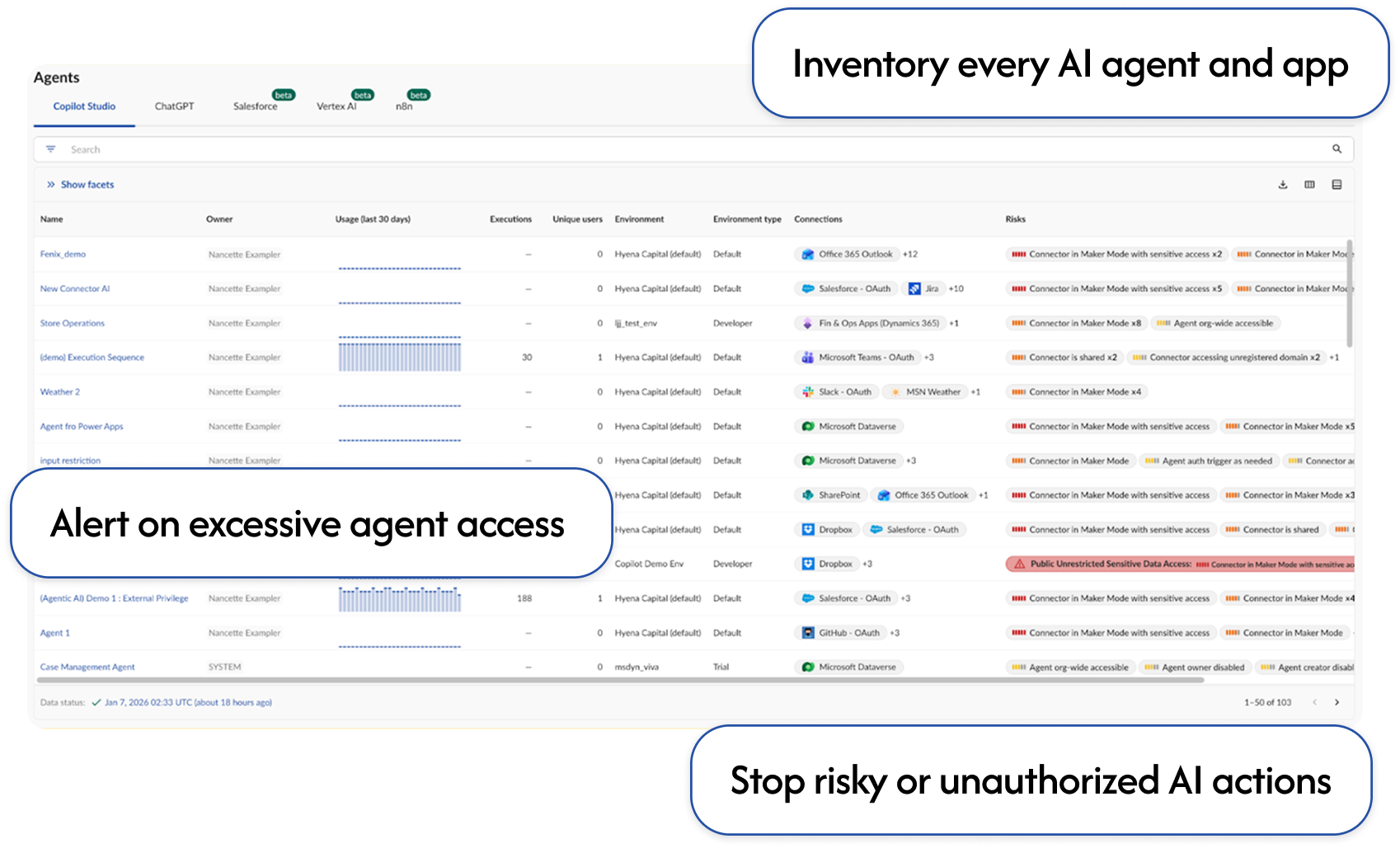
user-to-agent interactions secured
Monitor configuration drift and spot violations to automate SaaS compliance reporting and shorten SaaS security reviews.
Streamline compliance →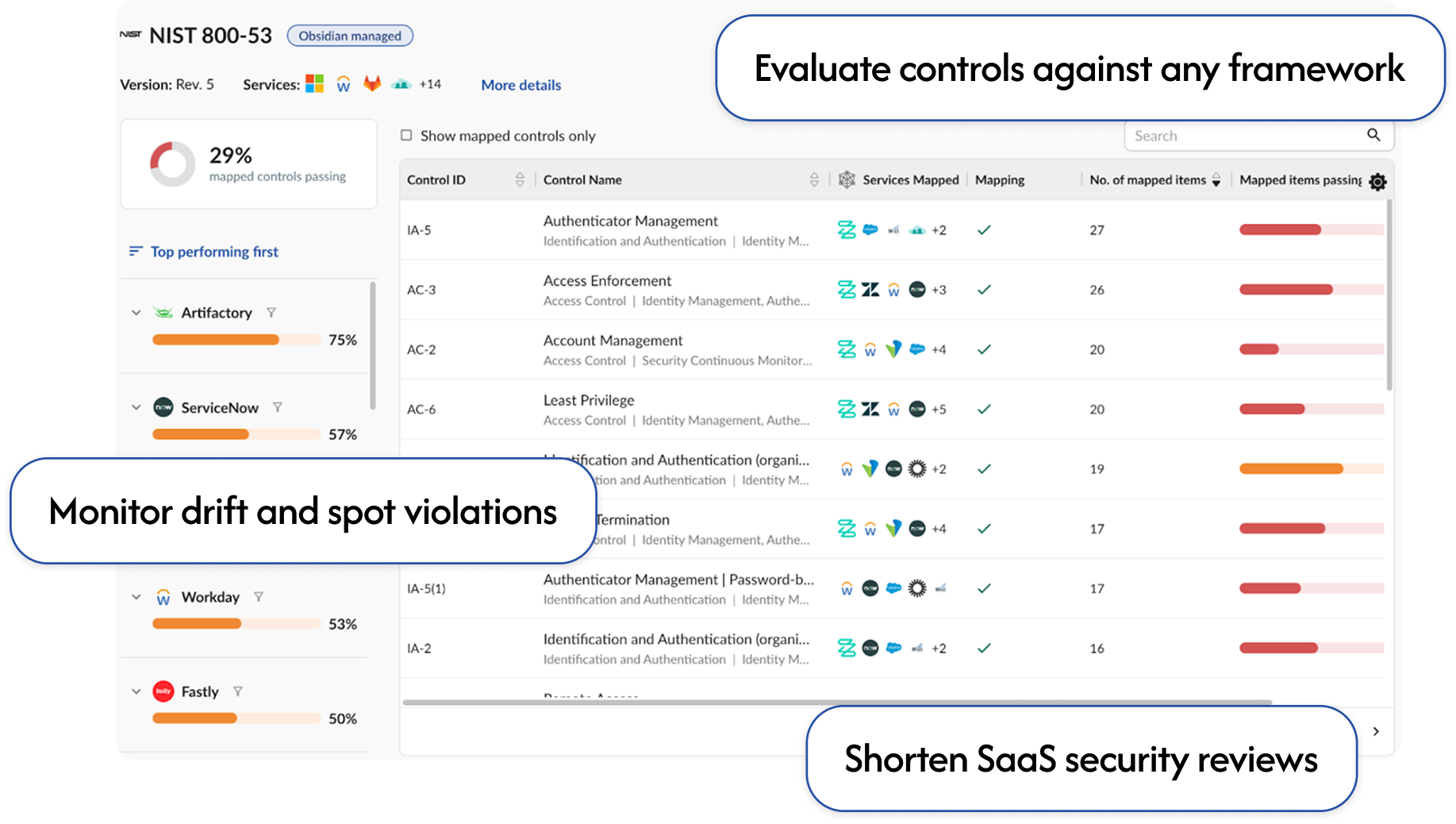
reduction in audit prep time
Prevent SaaS account takeover with inline defenses to stop credential and session theft paired with alerts to speed investigation and response.
Detect SaaS attacks →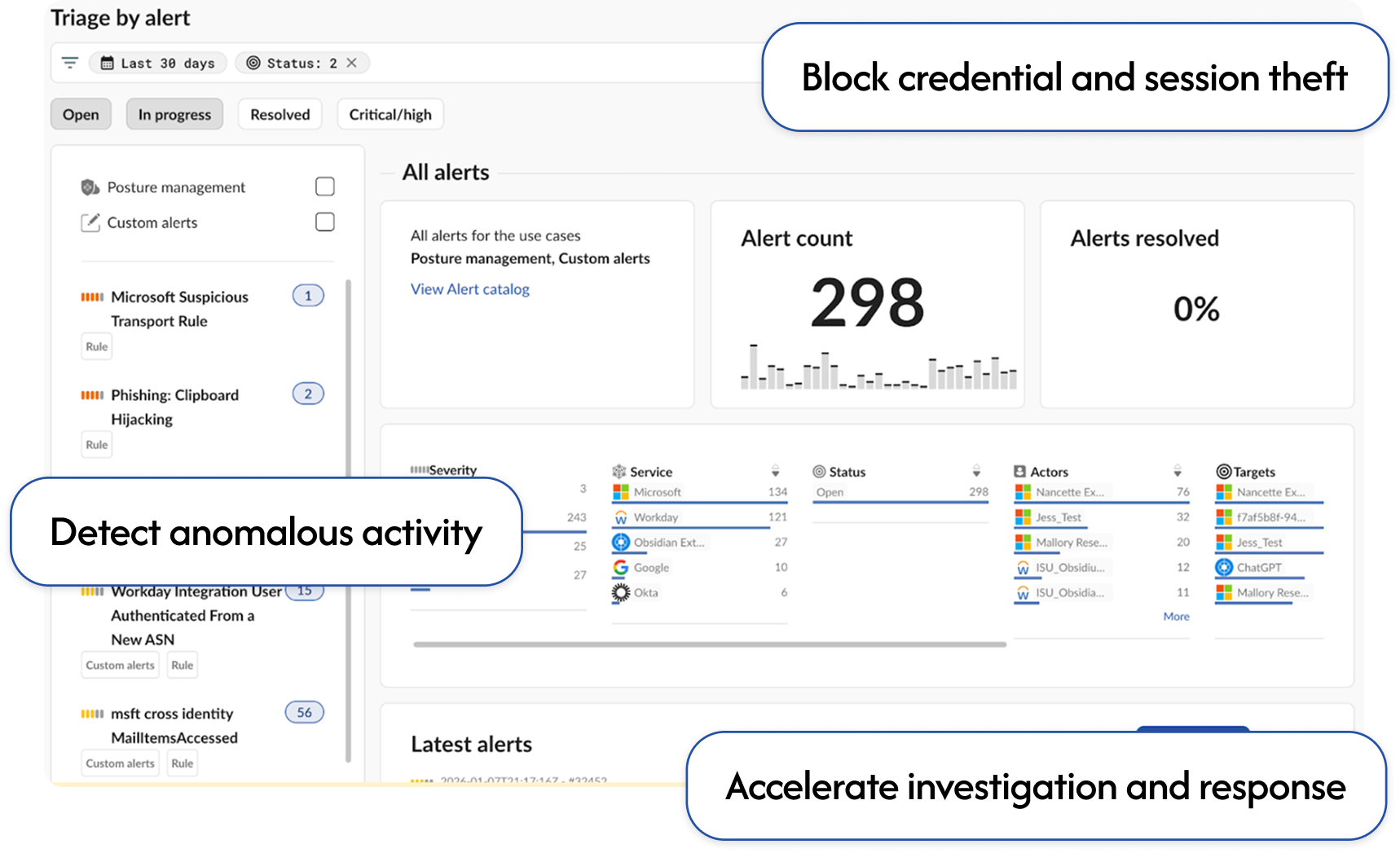
next-gen phishing attacks defeated
Remove data exposure risks and AI policy violations by controlling exactly what information leaves your organization through SaaS.
Protect your data →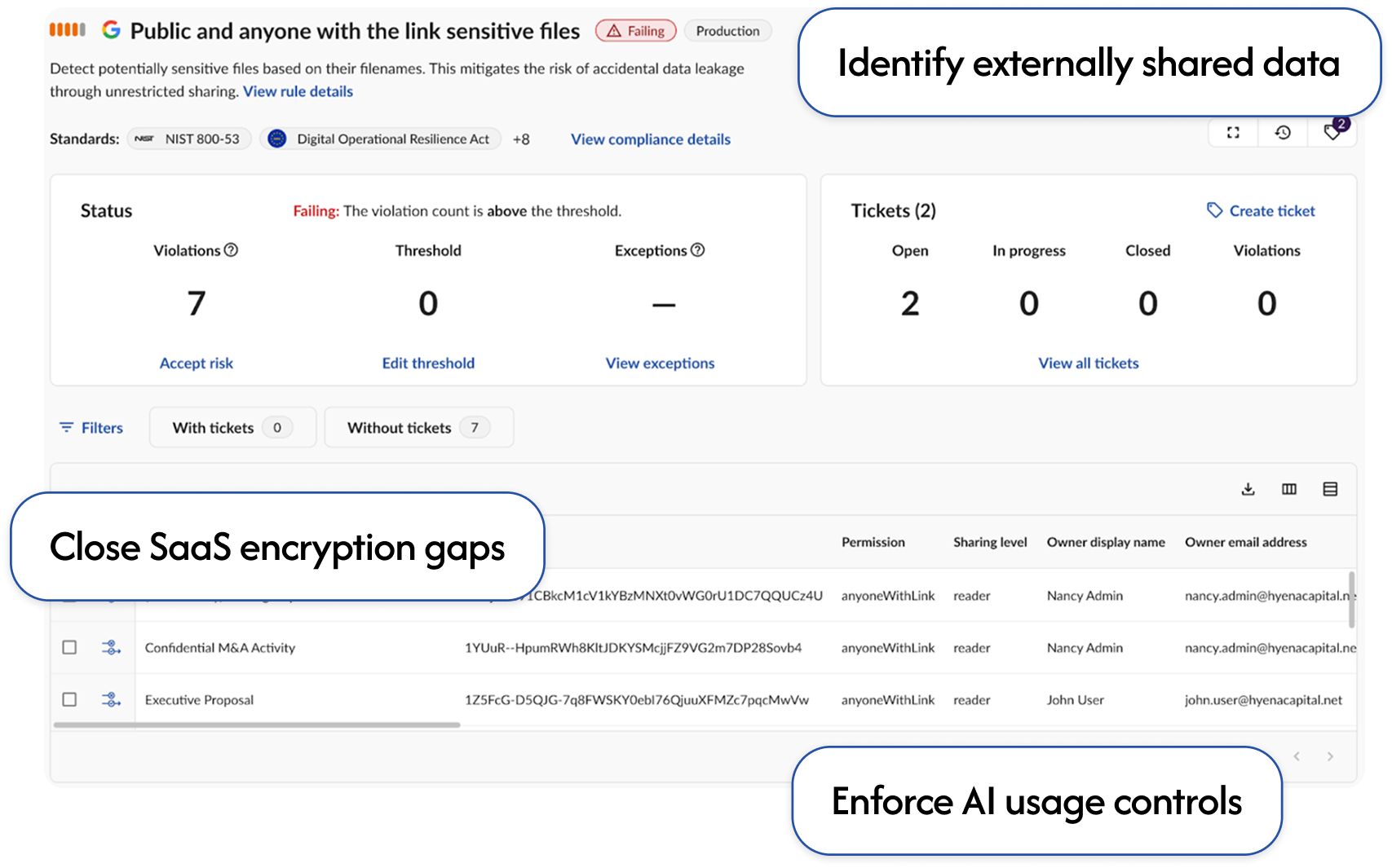
reduction in publicly available files