Most organizations believe their biggest SaaS risk lives inside the applications they manage directly. In reality, the real exposure often sits one integration away.
Modern businesses run on SaaS, stitching together hundreds of cloud applications with OAuth, APIs, service accounts, and automated workflows. These connections are powerful, but they quietly extend trust beyond your security controls. Attackers have noticed. Instead of breaking into well-defended enterprise accounts, they compromise one vendor, one integration, or one overlooked token, then ride those trusted connections straight into customer environments.
This shift is not theoretical. Incidents like the Salesloft-Drift breach and the downstream impact resulting in the Gainsight breach demonstrate a hard truth: you don’t need to be the primary target to be breached. As Patrick Opet, CIO of JPMorgan Chase recently warned in his open letter to suppliers, modern SaaS integration models are eroding decades of carefully architected security controls, collapsing authentication and authorization into overly simplistic trust relationships that attackers actively exploit. If your business runs on SaaS, you are part of a supply chain and that supply chain has become one of the most critical and least understood attack surfaces today.
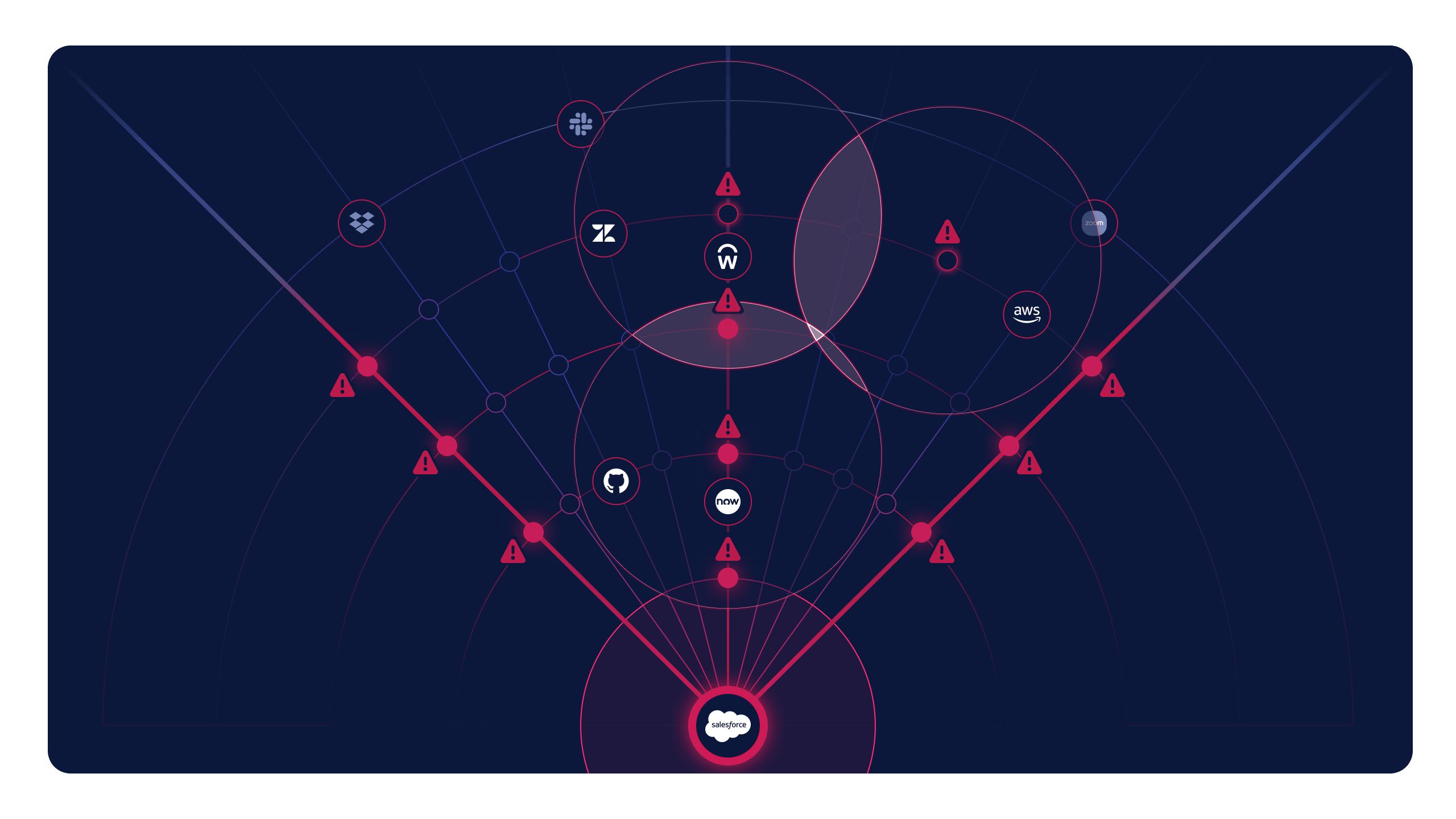
The anatomy of a modern SaaS Supply Chain
In cybersecurity, a supply chain refers to the network of third party vendors, partners, services and software that an organization relies on. Similar to how a physical supply chain involves the movement of materials, a digital supply chain encompasses the flow of data and permissions between connected systems. This includes SaaS applications, cloud services, APIs and OAuth integrations.
AI-to-SaaS integrations extend the same SaaS-to-SaaS trust model, but with greater complexity. For AI agents to operate autonomously, they need business knowledge from your organization, which often means that they need to request broad permissions, access multiple applications at once, and chain actions across other agents. Together, these connections create a web of dependencies that keep your business running and are growing at an unprecedented rate, making the supply chain increasingly complex. According to Obsidian’s network data, the number of SaaS integrations and AI agents created have increased by 123% and 223% respectively.
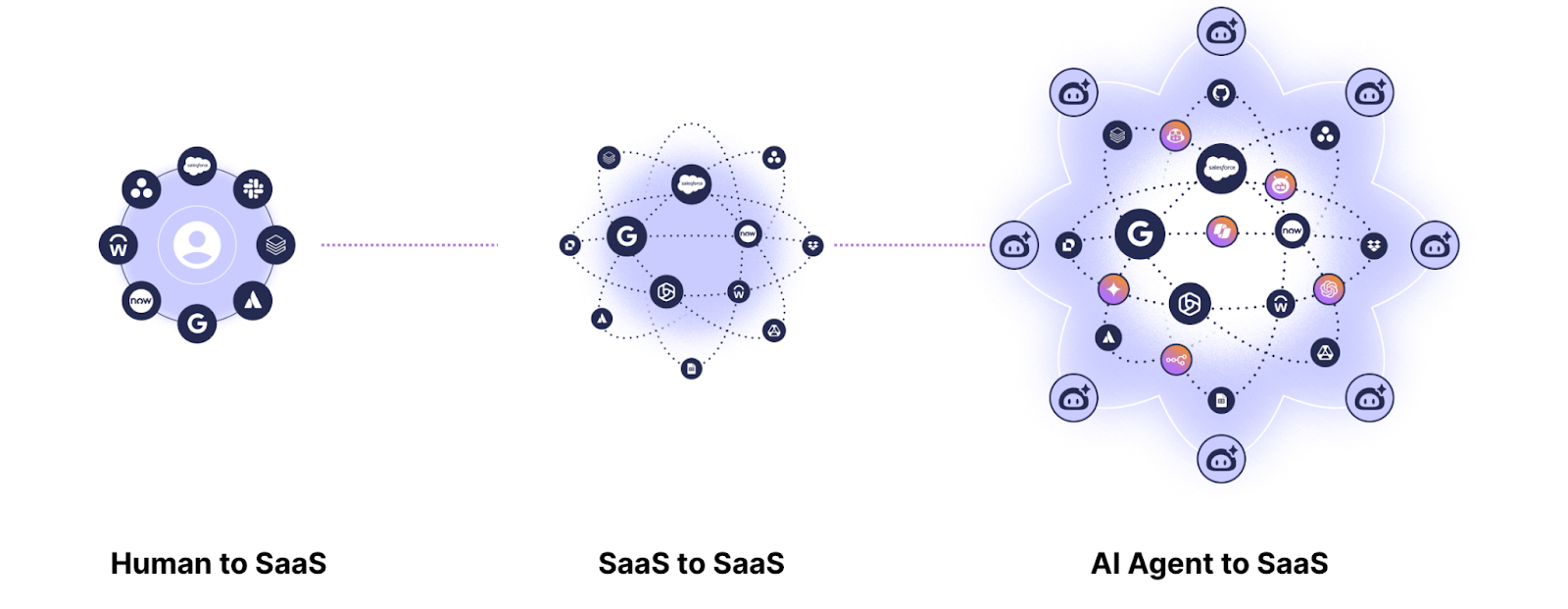
The gap in your SaaS Supply Chain: Integration Risks Explained
SaaS supply chain attacks thrive on the interconnected nature of cloud applications, where systems communicate using programmatic credentials like API keys, OAuth tokens, and service accounts. These credentials quietly power SaaS-to-SaaS integrations, often operating outside traditional security controls. When visibility is limited, governance is weak, or permissions are inherited and never revisited, these integrations create gaps attackers can easily exploit without being detected.
Non-human identities: service accounts
A service account is a non-human account used by applications and automated workflows to run continuously in the background, often with persistent access and the ability to act within SaaS apps (for example, sending emails, posting messages, or generating reports). Service accounts are typically used when long running automation or system level access is required.
A service principal is an application identity used for SaaS to SaaS authentication via OAuth or APIs, allowing one service to securely access another on behalf of a user or the organization. Service principals are commonly used for integrations where one SaaS platform needs delegated or app-level access to another.
Both are harder to secure in SaaS environments because they are non-human identities, meaning that they are machines operated and therefore, lack MFA. These accounts are designed to run 24/7 for business productivity, independent of the human workforce. As a result, they tend to be long standing access and often accumulate broad, long-lived permissions over time, making them high-impact targets in SaaS supply chain attacks.
Attackers use this to enter SaaS ecosystems and are able to get administrative access to configurations, sensitive data, and downstream SaaS applications. The implications are severe: a single compromised service account can function as a trusted, persistent backdoor into the environment, enabling data exfiltration, policy manipulation, and cross-application lateral movement that is extremely difficult to detect. For example, in the 2020 Solarwinds Orion attack, after gaining initial access, attackers used the compromised Orion server to find and exploit highly privileged accounts, often service accounts with broad permissions to escalate privileges and access highly sensitive environments.
OAuth tokens
OAuth tokens are the credentials that allow SaaS applications to securely access data and services on a user’s behalf without requiring repeated logins. They make access convenient by enabling seamless integrations, background workflows, and automation across SaaS tools but inconsistent standards across providers often result in tokens that are overly broad, long-lived, and widely distributed. OAuth relies on two primary token types: access tokens, which are short-lived, and refresh tokens, which generate new access tokens over time.
Most SaaS apps implement OAuth tokens as bearer tokens, something like a key. Whoever has this key can use it. These tokens aren’t tied to a specific user or person, meaning that if an attacker steals one, it still looks valid and works normally. That means you cannot automatically trust OAuth tokens and must constantly check how and where they are being used
Refresh tokens are especially risky because, like service accounts, they operate outside traditional login flows, often lack visibility, and are stored insecurely in browsers or local applications. If stolen, an attacker can gain persistent access without a password or MFA, continuously minting new access tokens while evading identity alerts. This enables long-term, stealthy access to emails, files, and APIs, sometimes persisting even after password resets. Incidents like the 2023 CircleCI breach and the Gainsight–Salesforce attack demonstrate how stolen or stale refresh tokens can be weaponized to compromise entire SaaS supply chains.
Shadow SaaS and unsanctioned integrations
Shadow SaaS emerges when employees connect third-party applications without IT awareness or approval, usually for business or productivity purposes. For example, an employee creates a Dropbox account using their corporate email to facilitate transfer of files between devices. While it's easy and productive to do this, it introduces a major gap where the integrations are able to inherit access to company files and in the case of an account compromise, attackers get direct access to corporate data without ever having to breach the company’s SaaS environment.
The risk escalates quickly. Sensitive data can flow into unvetted systems, attackers can pivot across SaaS platforms using inherited OAuth permissions, and breaches may go undetected due to limited visibility into these applications.
Additionally, even approved vendors have shadow instances which bypass traditional security such as DLP, CASB and network control which may not be configured to give you visibility into all instances, allowing sensitive data to move freely outside sanctioned environments.
API Keys
APIs serve as the backbone of modern SaaS integrations, enabling applications & automated workflows to exchange data and trigger actions at scale. Compared to OAuth tokens which focus on controlling user access, API keys prioritize simplicity and speed for system access, usually without user context. To enable this access, APIs commonly rely on API keys as they are easy to implement and fast, providing a huge convenience to engineering teams. While API keys can be rotated or set to expire, doing so often introduces operational friction, which leads many teams to treat them like static passwords, embedding them in code, storing them in configuration files, or sharing them across systems.
This presents a great risk. API keys are long-lived, overly-permissive and poorly monitored, making them attractive targets for attackers. Exposed keys in repositories, logs, or build pipelines can impersonate legitimate systems and gain direct access to sensitive APIs. Once inside, attackers can extract data, manipulate business logic, or escalate privileges using poorly secured endpoints. The consequences are substantial: a single leaked API key can unlock multiple integrations, creating a chain reaction that spreads compromise across the organization’s SaaS estate.
Overpermissioned SaaS applications
Over-permissioned SaaS apps arise when users or administrators grant applications more access than they truly need, often through one-click OAuth approvals, inherited roles or default permissions. These permissions often persist long after the app is installed, creating a silent but expansive risk surface.
For example, a Salesforce integration approved only to sync contacts may also inherit access to custom objects, reports, or administrative APIs because it was installed under a highly privileged profile. If that vendor is later compromised, attackers automatically gain the same broad access, without ever needing to escalate privileges themselves. Because most organizations lack visibility into effective permissions and how they’re derived, these over-permissioned apps often remain unnoticed until they are abused to access sensitive data, change configurations, or move laterally across connected SaaS platforms.
Why traditional tools fail to secure your SaaS Supply Chain
Traditional security tools were built for a world with a clear network perimeter. But SaaS has eliminated that perimeter entirely: data, identities, and workflows now live in cloud applications that legacy tools cannot see or control. A security stack designed for on-prem networks simply cannot protect modern SaaS environments.
.png)
This blind spot grows with the rise of shadow apps and unmonitored integrations. Employees can connect third-party apps with one OAuth click, granting broad access to email, files, and identity data. Traditional tools can’t discover these apps or evaluate their permissions, leaving a hidden and expanding supply chain.
Legacy tools also fail because they don’t address identity-based risks, which now drive most SaaS compromises. Attackers exploit OAuth scopes, refresh tokens, and over-privileged service accounts vectors that network-and endpoint-focused tools were never designed to detect.
Finally, even many of the modern tools claiming to protect SaaS supply chains rely on indirect signals, API calls, or periodic check, meaning that they can’t observe the lateral movement , or cross-app activity that happens between integrated SaaS systems. This creates major blind spots, precisely the spaces attackers use to escalate privileges, reuse tokens, abuse OAuth scopes, or pivot from one compromised app into another. Without visibility into how SaaS apps truly communicate and trust each other, these tools fail to detect the most critical parts of a SaaS supply chain attack.
The impact of SaaS Supply Chain attacks
SaaS supply chain attacks don’t stay confined to a single app, they spread through the interconnected web of cloud services organizations rely on. The immediate fallout includes financial loss, data exfiltration, and erosion of customer trust. Stolen data, costly investigations, and operational disruption are only part of the impact; the reputational damage from a third-party breach often lingers far longer.
The real danger lies in the downstream effects. When one integrated SaaS platform is compromised, every connected system becomes vulnerable. Incidents like Salesloft–Drift showed how a single OAuth integration could extend into tools like Gainsight and multiple Salesforce instances, multiplying the number of accounts affected to more than 700 companies being impacted. These attacks can quickly escalate into widespread, multi-organization breaches, as every customer of the compromised vendor inherits the same exposure.
Secure your SaaS Supply Chain with Obsidian Security
- Complete Integration Visibility: Discover and gain a unified view of all OAuth apps, tokens, and permission, shadow integrations, including internal and third-party integrations.
- Continuous OAuth Compromise Detection: Detects token abuse and supply chain threats early using behavioral analytics enriched by the Obsidian Knowledge Graph, correlating activity and identity across your entire SaaS environment
- Reduce Attack Surface & Respond Faster: Get clear, in-product threat recommendations that explain what’s risky and exactly how to remediate, enabling faster, more confident response to SaaS supply chain incidents.




