

n8n powers faster automation — but without guardrails, AI workflows can create cascading SaaS risks.
Obsidian lets you scale safely while keeping your data and apps protected.
Automation isn’t one-size-fits-all. Each team uses n8n differently.
With Obsidian, every action is visible, controlled and secure.
Automate routine support tasks
Detect and respond to threats faster
Deploy and monitor applications automatically
Onboard new employees quickly
Update CRM records without manual work
Send personalized campaigns at scale
As powerful as n8n is, automation without guardrails can open the door to diverse and significant risks:
n8n agents often request broad access (like “read/write all data”) when only narrow permissions are needed, creating unnecessary exposure.
A single node connecting to core SaaS like Salesforce or Google Drive can become a hidden entry point.
Automated flows can accidentally sync sensitive customer or employee data across systems.
Workflows built outside security’s view make it impossible to enforce policies and monitor agents.
Community nodes or third-party plugins may contain vulnerabilities or malicious code that slip into production workflows.
Obsidian secures your n8n deployment with visibility, continuous monitoring, and actionable guidance—so your teams can harness AI automation confidently.
Get a live directory showing who created the agent, what SaaS apps it touches, the privileges it holds, and every action it takes.
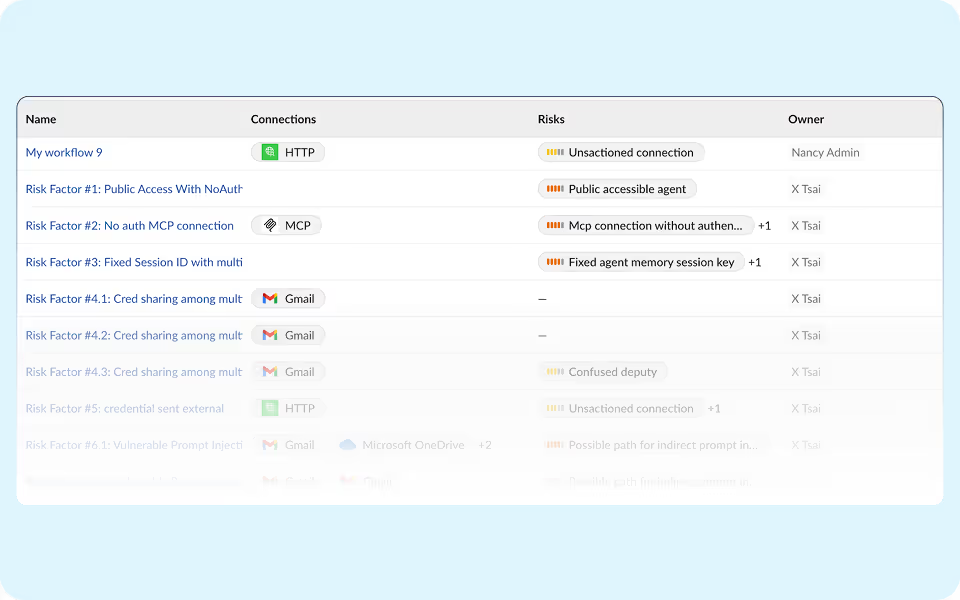
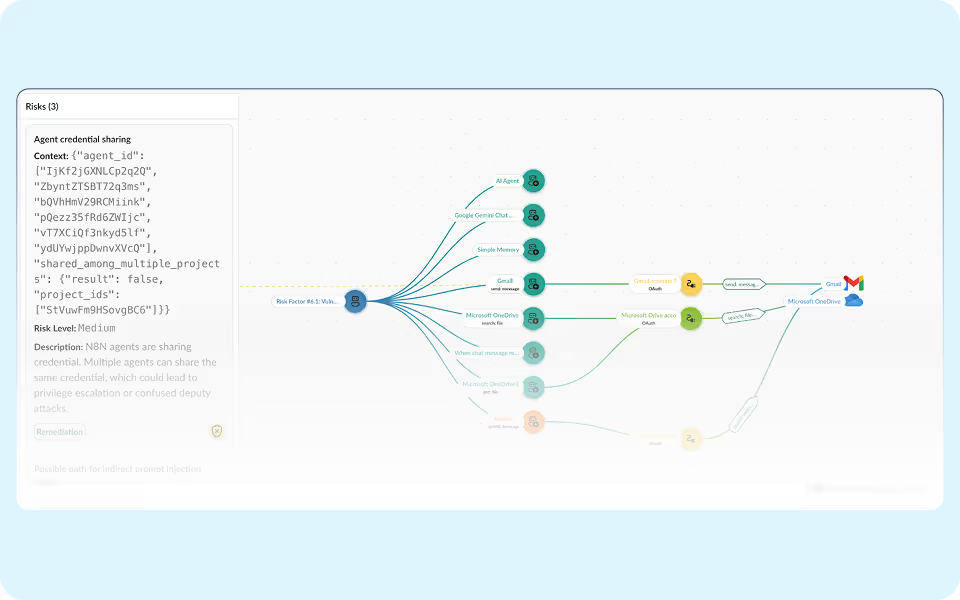
Track privileges, data access, and connected apps in real time. Spot shadow workflows the moment they appear.
Prevent data leakage by auditing AI agent execution against SaaS activity logs.
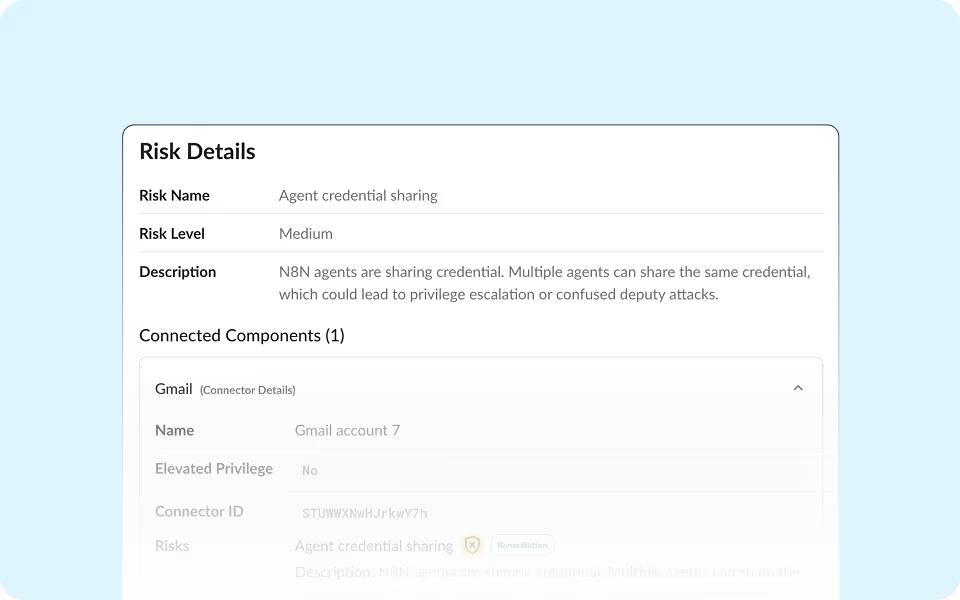
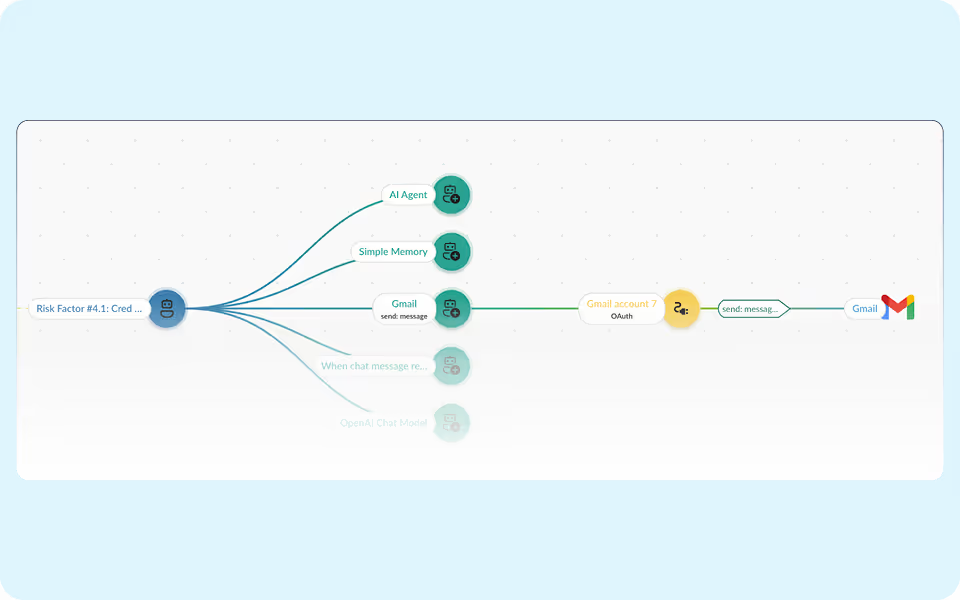
Detect vulnerable or malicious community nodes and plugins before they reach production.