Highlights
- The wrong setting in Salesforce could expose sensitive data to individuals or groups outside your organization
- Obsidian Security helps affected organizations immediately remediate this vulnerability and better harden Salesforce posture
- Read below for simple steps to ensure your Salesforce links are not public
A Salesforce Misconfiguration May Expose Sensitive Data and Files
Security teams are often blind to the scale of public sharing that occurs at their organization, mostly across SaaS applications like Google Workspace. Now, add Salesforce to the mix.
A risky outcome from a misconfigured Salesforce setting can expose sensitive files via a shareable link. A majority of organizations have this setting misconfigured in Salesforce despite this risk being highlighted in 2024.
Abuse of this setting by Salesforce users, combined with a lack of visibility or expertise into the security and posture of the application, creates gaps in coverage. Without the right tools or knowledge, discovering—and remediating—every SaaS misconfiguration is near impossible.
Let’s dive deeper into this Salesforce security finding.
What Are Public Links?
The ability for SaaS owners and users to quickly deploy, integrate, and share data across applications—commonly without proper security settings and controls in place—creates opportunities for files to be accessible to anyone outside the organization. In the case of Salesforce, users have the option to create public links that may unintentionally expose confidential data online, often without admins or security teams realizing it.
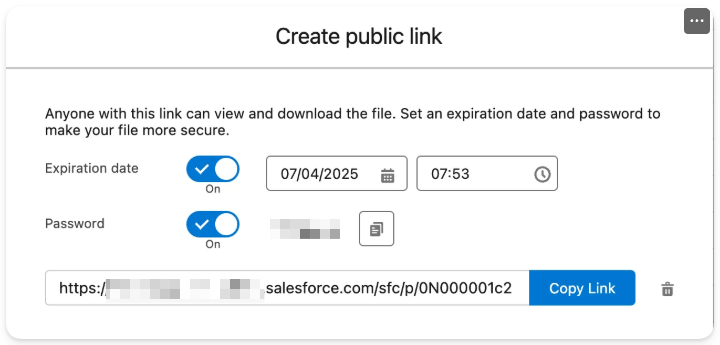
It is clear that there are legitimate business cases where sharing data via public links is not only helpful, but necessary. However, doing so securely and purposefully is just as important.
Let’s look at how you can better secure your Salesforce instances to protect your organization against sensitive data leaking out via publicly shareable links.
How to Secure Salesforce Data From Public Links
Here are immediate steps you can take to minimize any potential current, or future, exposure of your data.
Audit your Salesforce configuration to enforce granular access
Before making any changes, we strongly recommend carefully reviewing with your Salesforce team as changes might have implications on your business processes and functions.
Obsidian recommends you revisit your current content sharing policies and practices within your Salesforce environments to ensure that:
- Only the required users inherit the Public Link sharing feature
- Validate with your Business team(s) if the ‘Content Deliveries and Public Link’ features need to be globally enabled for external content/file sharing
- If so, review your current user Profiles and associated permission sets to allow Public Link sharing privileges to specific users only that require this functionality
- For Obsidian customers: we have published a High severity rule titled ‘Users that can share files via public links’ that can assist you in this review
- Files shared externally require a password applied to them
- Under the ‘Content Deliveries and Public Links’ section, consider enabling ‘Password Protection is required’ feature
- Please note that even if this option is enabled, the users still can disable password protection when generating the Public Link
- Public Links generated have an expiration set on them
- Educate your users to always set an expiration whenever there is a need to generate a Public Link for external sharing
Review the existing files publicly shared and restrict access as needed
In order to remediate current files that are publicly shared that should not have that setting enabled:
- Implement password security on shared files - There may be valid business use cases that require files to be shared outside your organization, enforcing a password on the public sharing link will reduce the risk of unauthorized access:
- In the Salesforce Sales Console, search for the publicly shared file.
- Click the Public Link section.
- Enable the Password toggle.
- Remove public sharing links - Follow the below instructions to delete the public sharing link:
- In the Salesforce Sales Console, search for the publicly shared file.
- Click the Public Link section.
- Click the trash icon next to the link to delete the link.
Please refer to the following Salesforce Help Articles that detail how ‘Content Deliveries and Public Links’ feature is configured as well as how users can add Passwords and Link Expiration at the time of sharing content externally:
- Enable Content Deliveries and Public Links
- Set a Password or Expiration on a Public Link to a Salesforce File
Reviewing and Remediating Salesforce Misconfigurations on Obsidian
Earlier this year, Obsidian notified affected customers about this potential risk and deployed a new product update to streamline remediation. This associated Posture rule detects at-risk files and provides corresponding context to quickly control file sharing via Salesforce. With this guidance, one enterprise customer reduced their number of shareable files from nearly 18,000 to less than 20. This impact was shared by dozens of other Obsidian customers similarly able to reduce the amount of publicly available files by more than 90%.
To get started, navigate to the Obsidian Admin portal > Posture > Rules and Settings > Filter on Salesforce. The exact rule name is the following:
- Files with publicly accessible sharing links and no password requirement
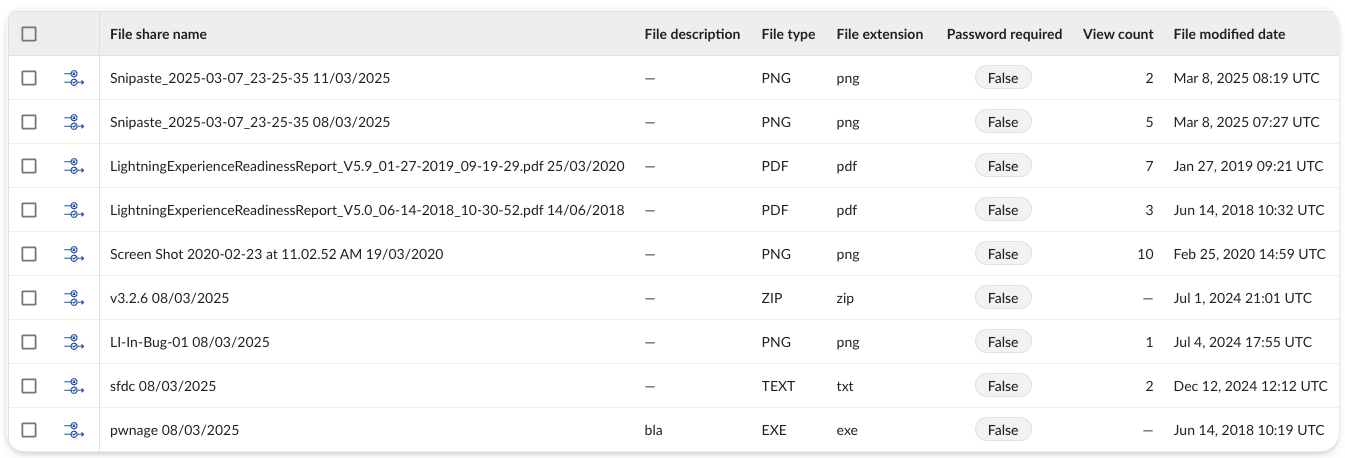
Beneath the violation table for this control, you’ll find helpful ‘Supporting evidence’ summaries:
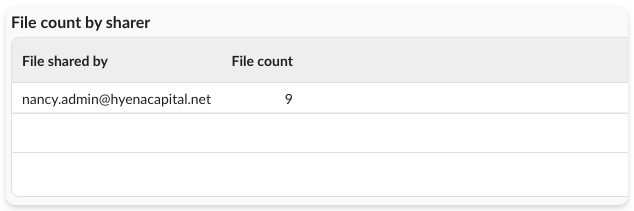
- File count by sharer: Helps identify users based on the files that they have shared
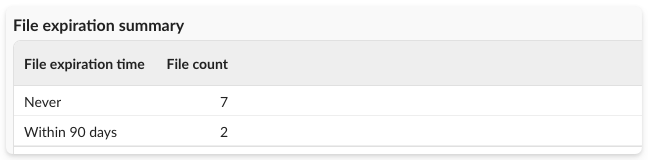
- File expiration summary: Shows when files will no longer be publicly accessible, often “never.”
You can also clone/edit this rule to apply additional filtering criteria that might help you in navigating large data sets (e.g. you might want to edit the rule to only show files that have a last view date).
Better Secure Salesforce and SaaS with Obsidian Security
For help reviewing these findings for your organization, or if you have any questions about our platform and how we can streamline SaaS security for Salesforce and other applications, please request a demo to get in touch.




