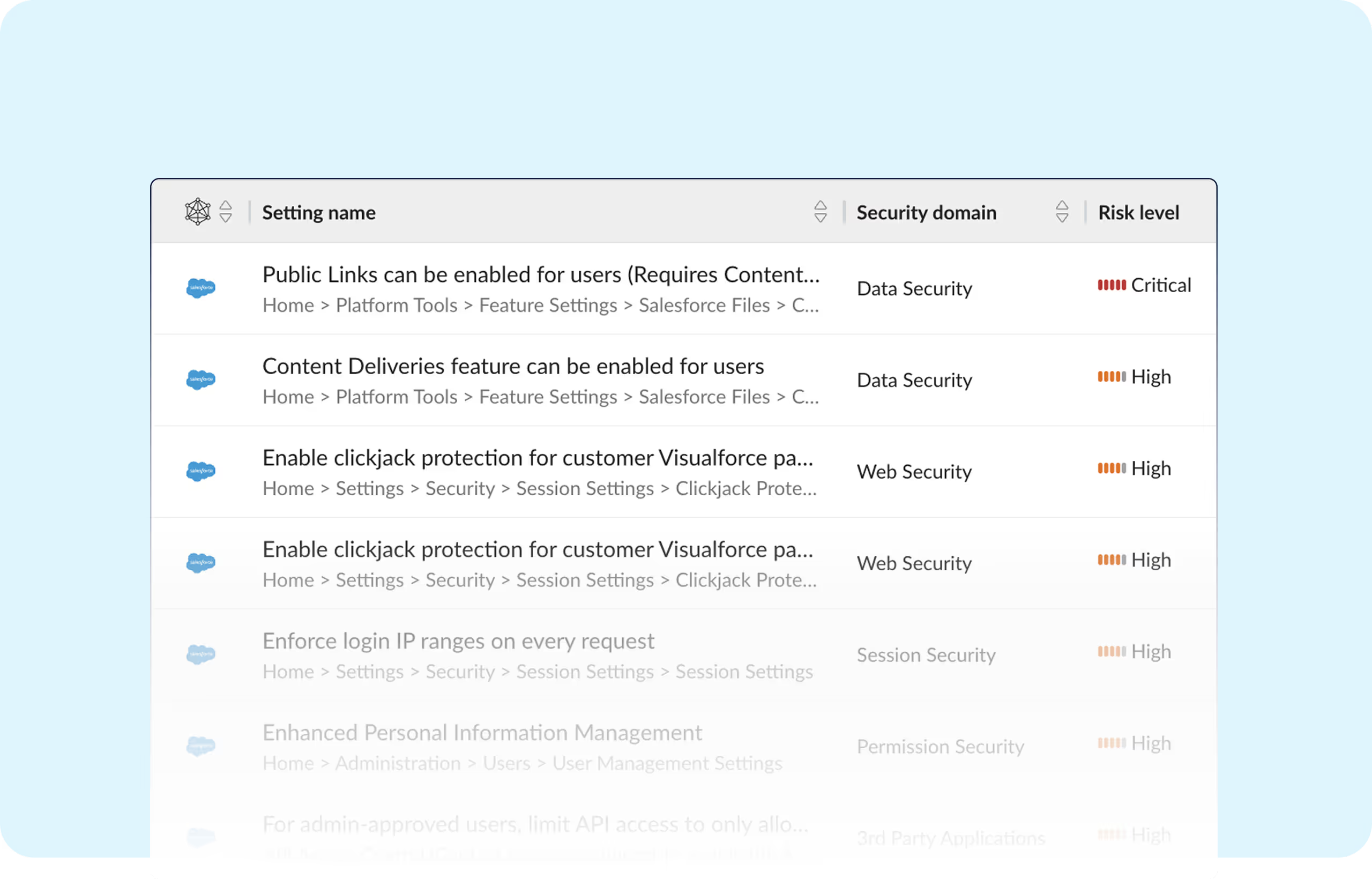
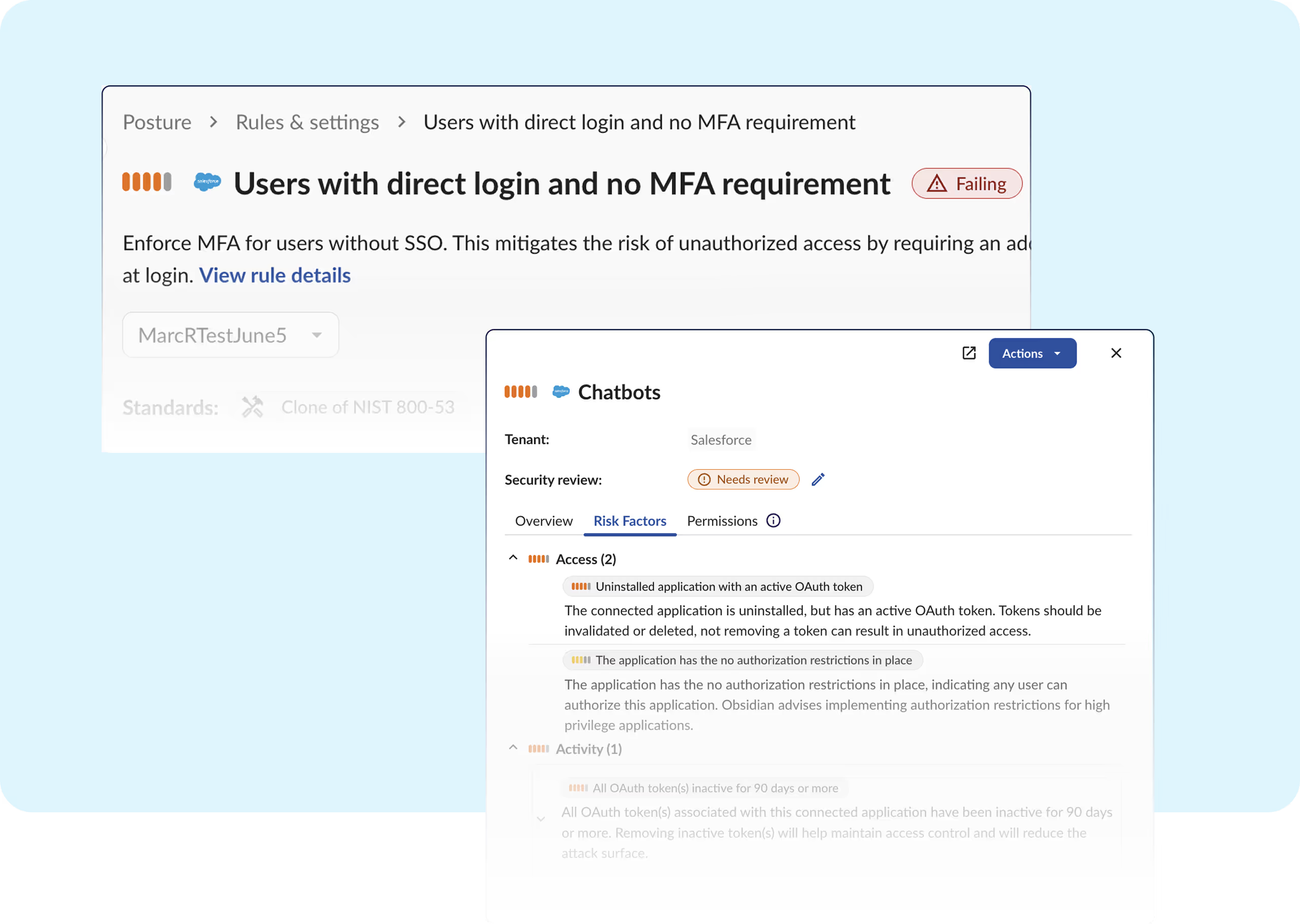
A shocking number of organizations are leaking private and sensitive information due to misconfigurations in Salesforce.
Obsidian Security makes it easy to identify publicly shared files and remediate misconfigurations.
of organizations have local login enabled
Obsidian Network Data
of SFDC tenants have publicly-exposed files
Obsidian Network Data
organizations leaked private data via misconfigured SFDC accounts
KrebsOnSecurity
A ‘do-it-yourself’ approach to Salesforce security creates unmanageable complexity and misses critical gaps.