Frequently observed Okta misconfigurations inadvertently diminish your security and risk unauthorized access.
Obsidian constantly monitors for anomalous login activity and misconfigurations that may weaken security effectiveness.

With complex identity flows, long access tokens, and cross-app connections, securing Okta by hand is error-prone and slow.

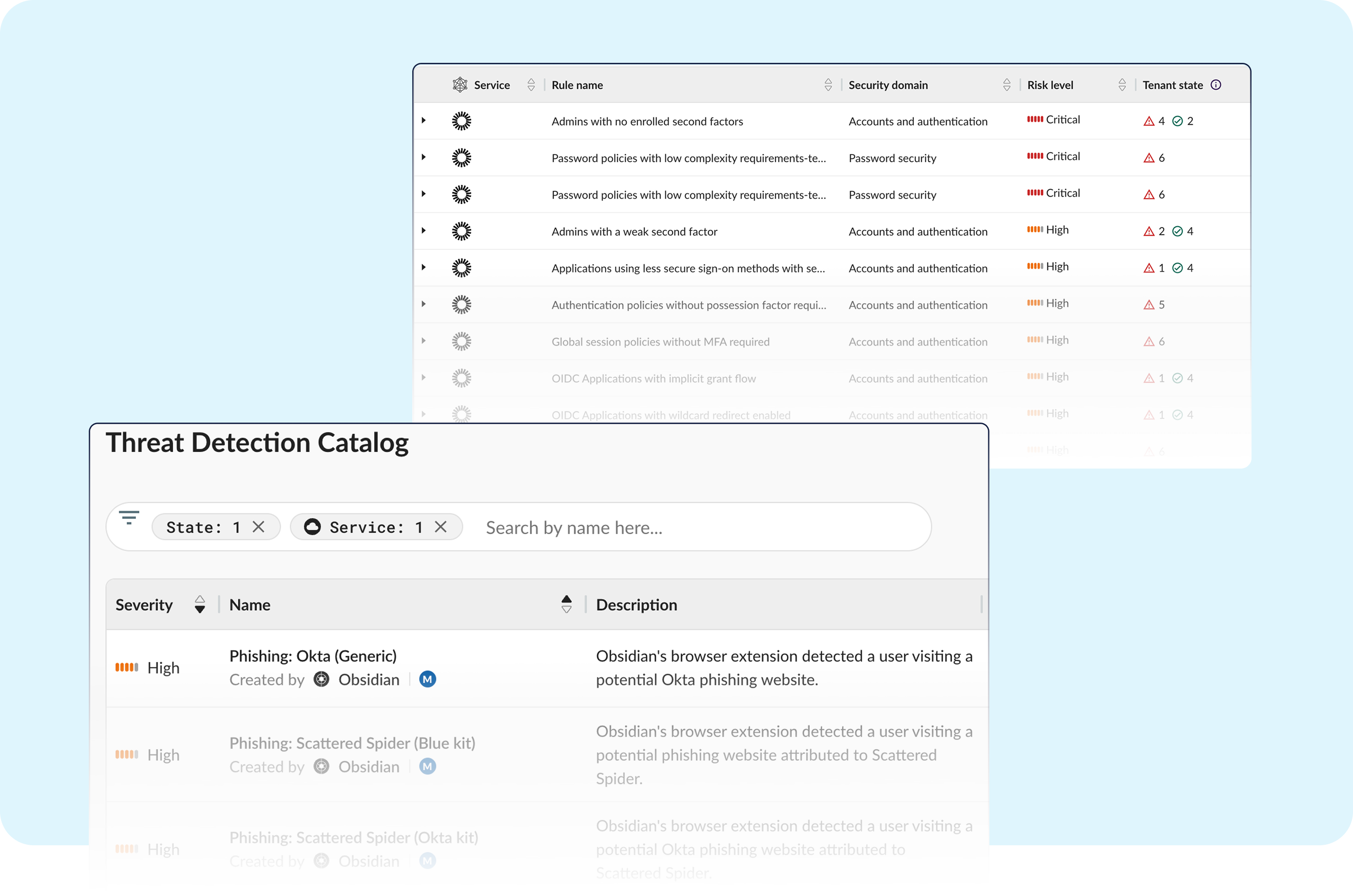
Okta empowers data innovation, but also introduces risks from excessive access and third-party code. Obsidian’s SaaS-native security stack continuously monitors token usage, enforces secure configurations, and delivers identity-aware detection to help organizations mitigate modern SaaS threats.