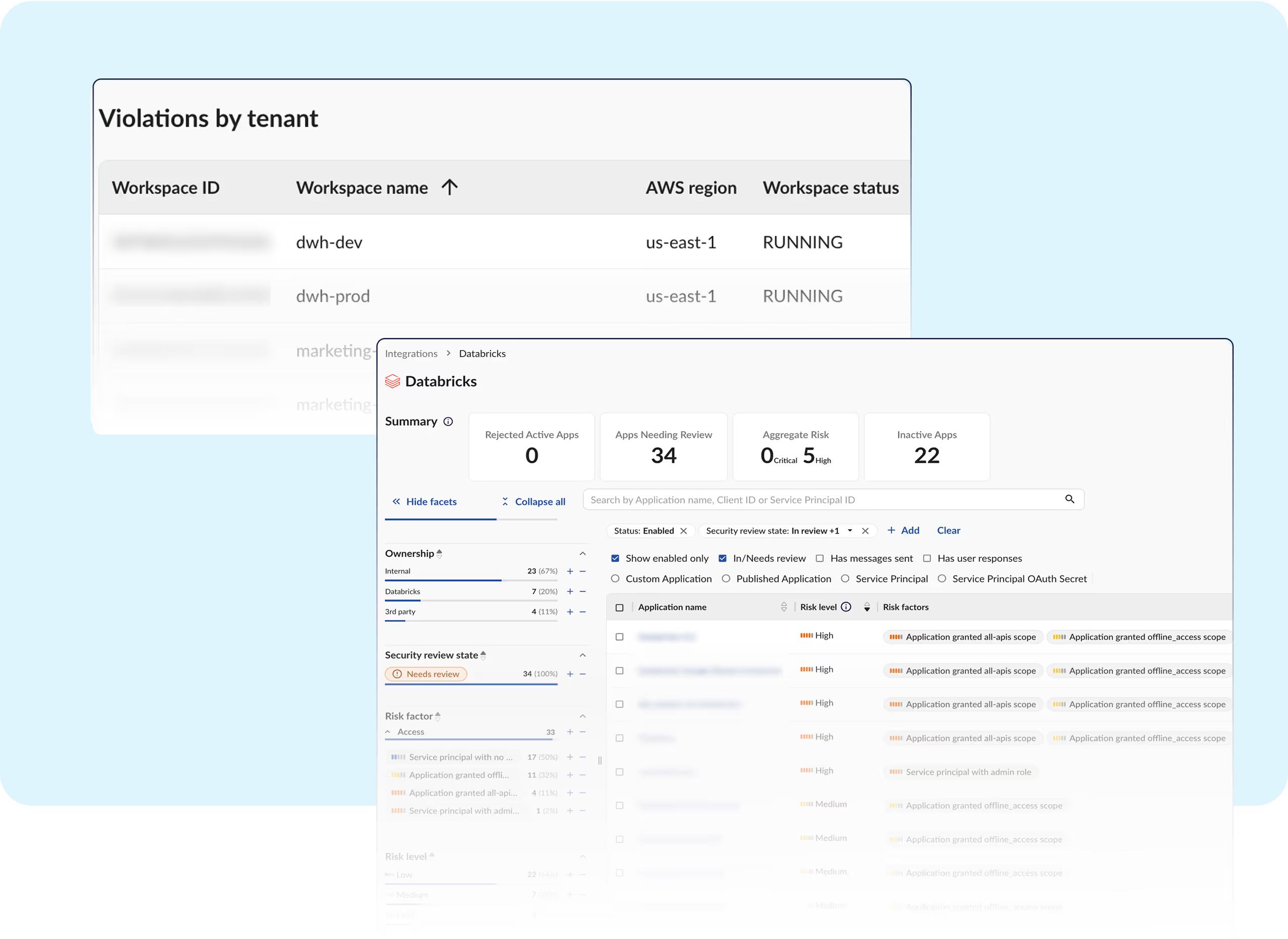
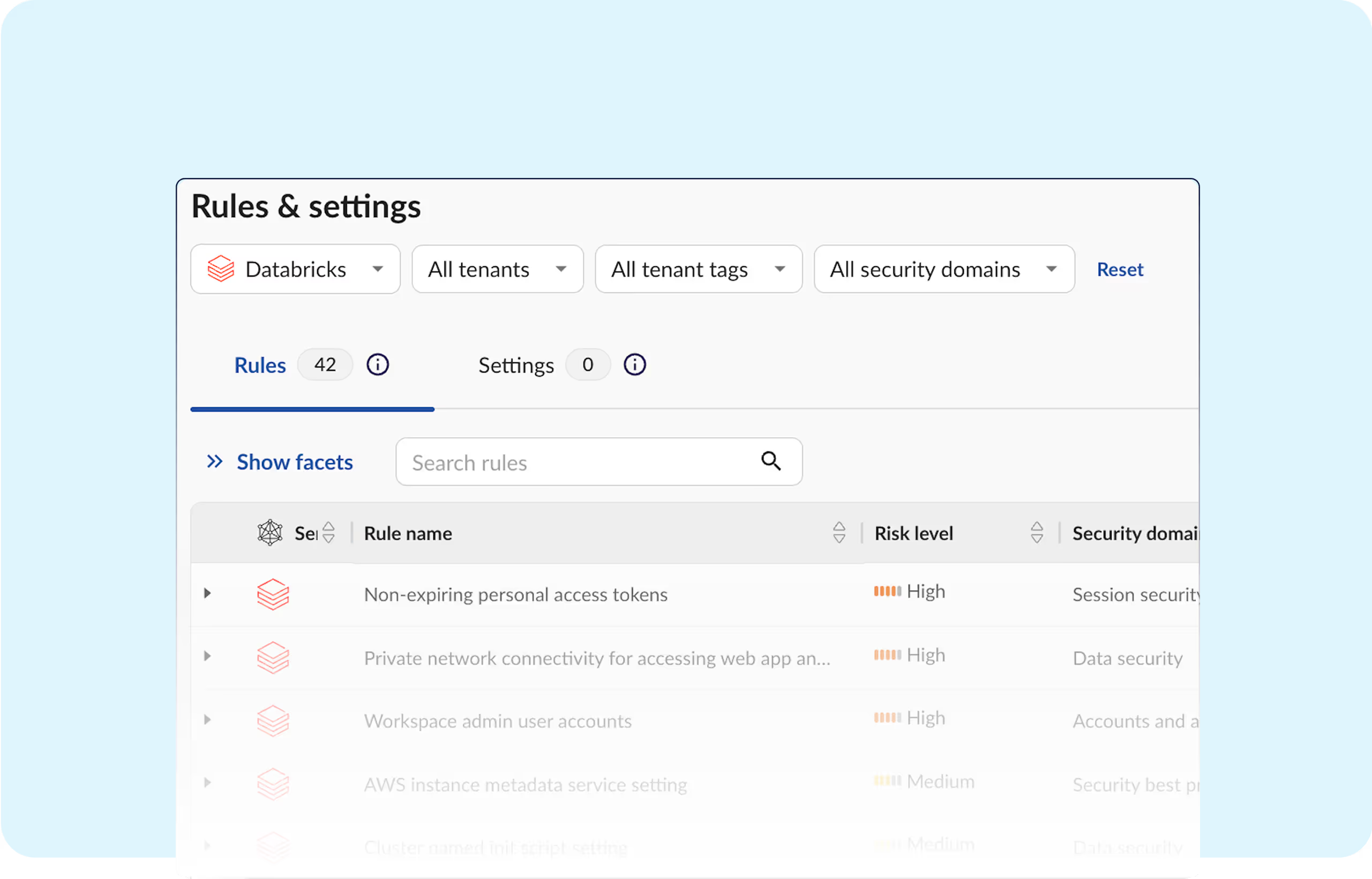
Security teams lack visibility into every third-party integration, excessive permission, and misconfiguration within Databricks.
Obsidian strengthens the security for applications on Databricks with automated controls that align with compliance standards and industry best practices.
of organizations have sensitive SaaS data exposed
Obsidian Network Data
of current GenAI projects don’t have a security component
IBM Data
of shadow SaaS integrate with core apps
Obsidian Network Data
Databricks supports growing data and AI demand, but manual oversight can't keep up.