ServiceNow contains complex customizations, granular permissions, and broad integrations, making it a significant challenge to secure.
Obsidian secures your ServiceNow environment by identifying every threat and posture gap.

Manually reviewing ticketing, communications, reporting, third-party apps, custom integrations, and external data leaves serious risks undetected.
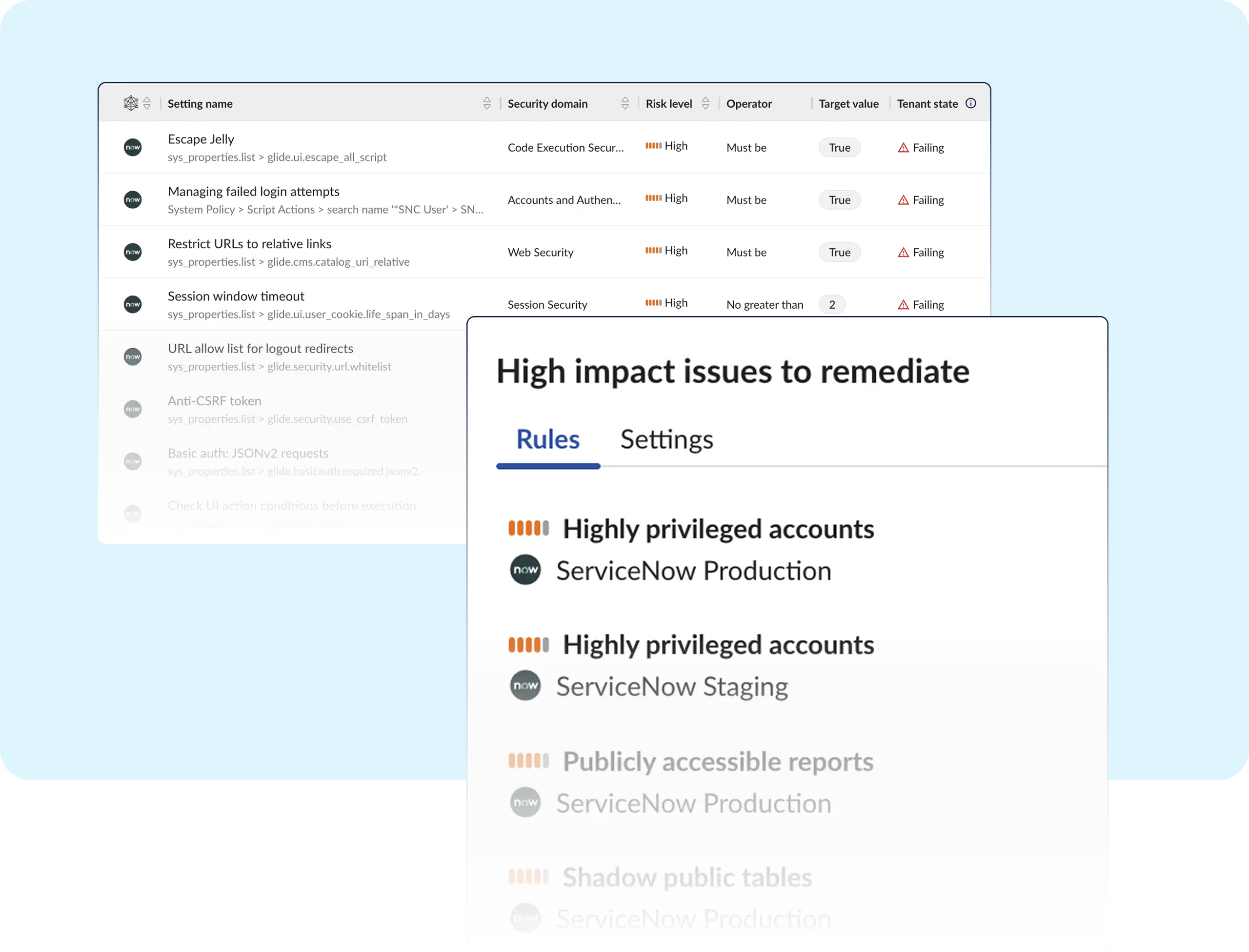
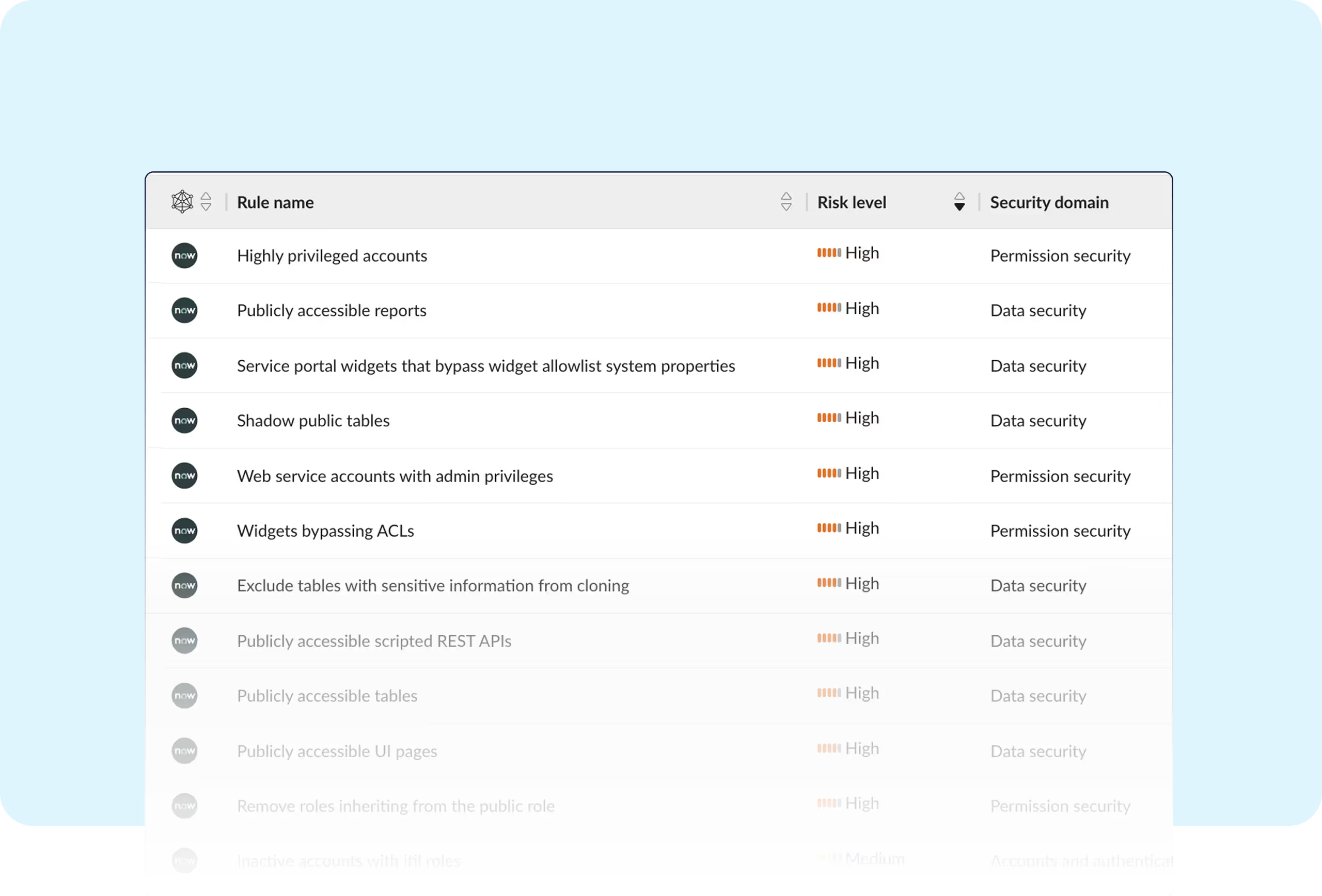
ServiceNow empowers data innovation, but also introduces risks from excessive access and third-party code. Obsidian’s SaaS-native security stack continuously monitors token usage, enforces secure configurations, and delivers identity-aware detection to help organizations mitigate modern SaaS threats.