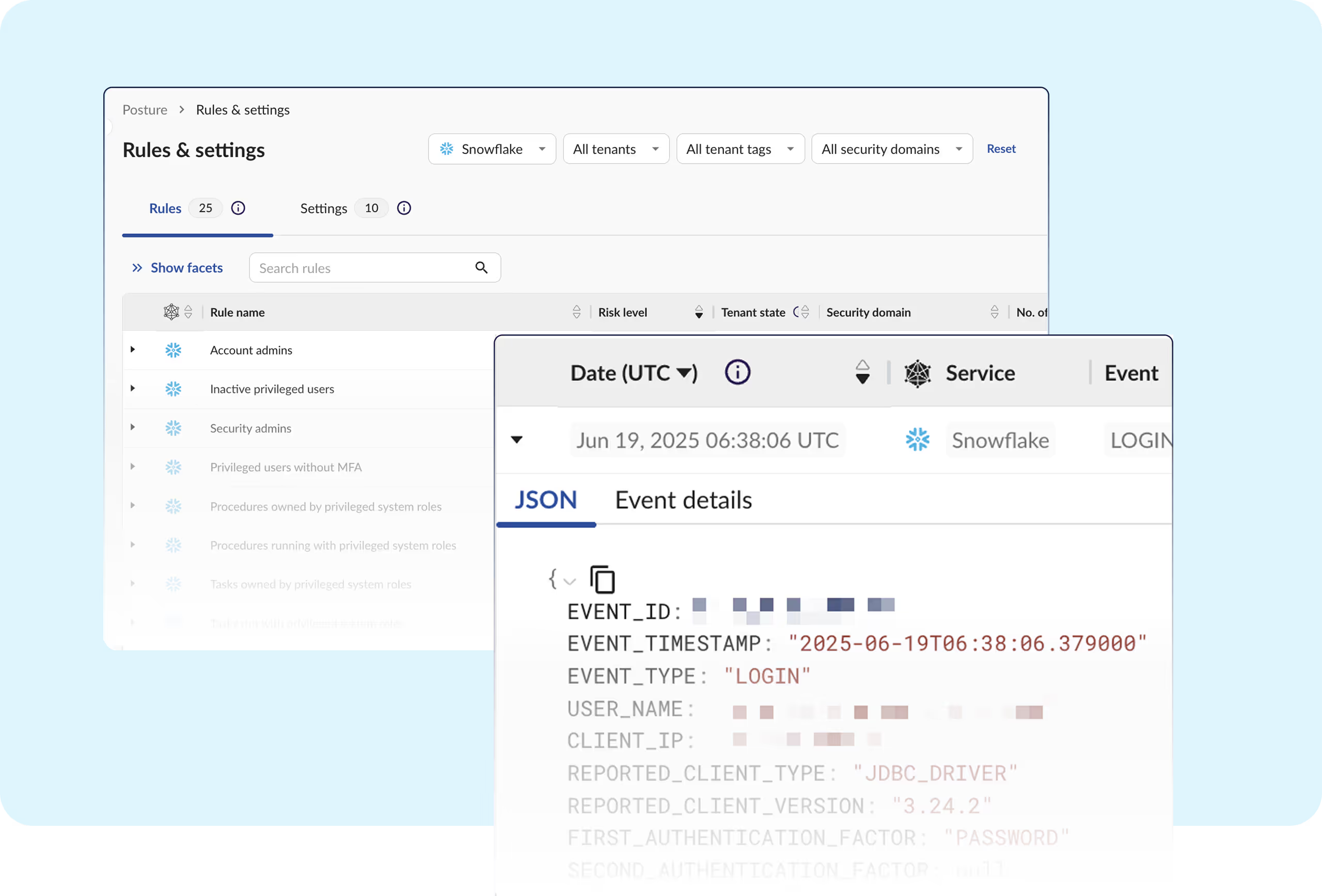
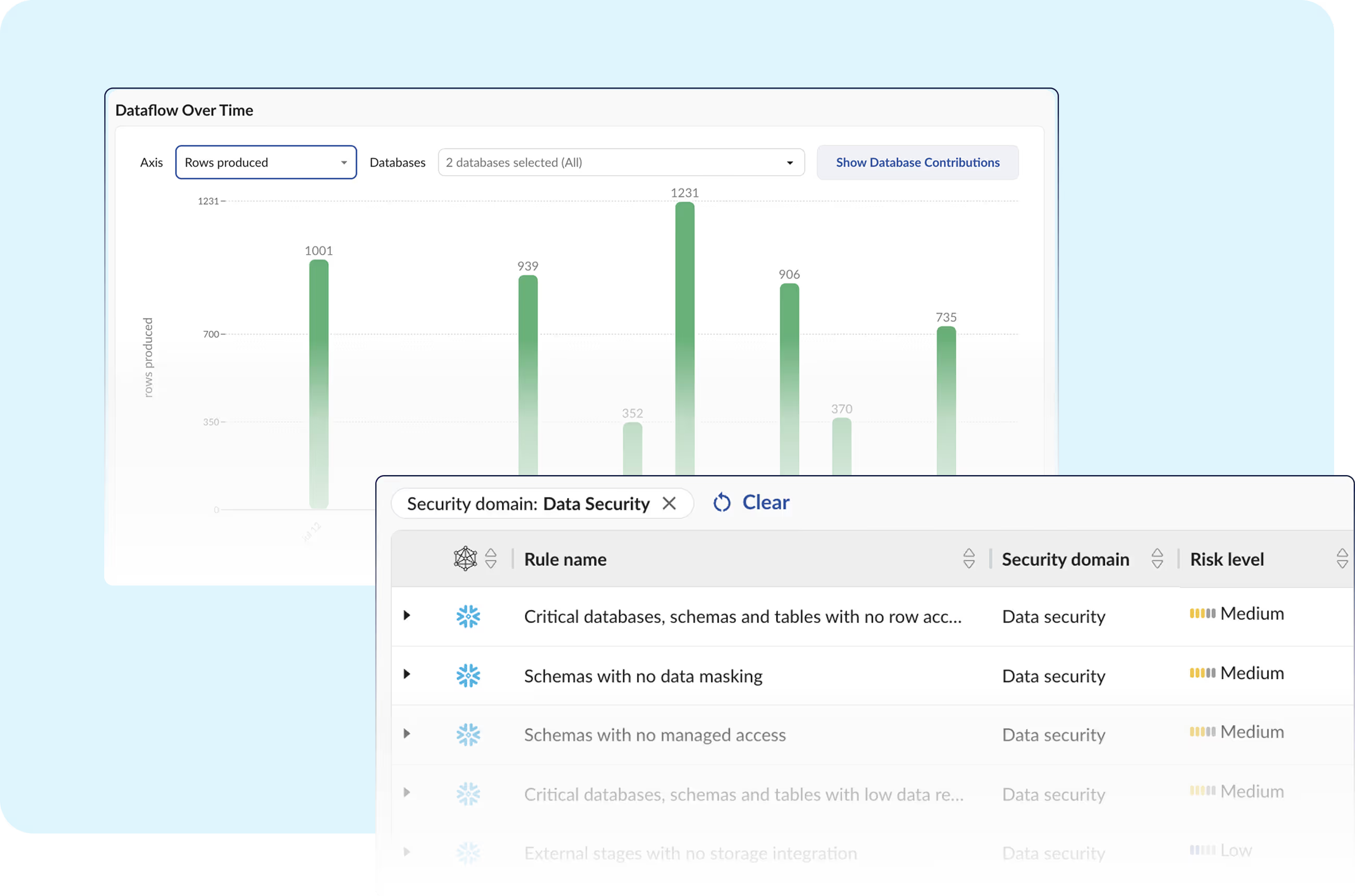
Attackers used stolen customer credentials without MFA to breach hundreds of businesses.
Obsidian makes it easy for organizations to automate workflows and ensure security of their Snowflake environments are in line with best practices.
companies breached via unsecured Snowflake accounts
BleepingComputer
successfully extorted from hacked businesses
CyberScoop
of organizations have sensitive SaaS data exposed
Obsidian Network Data
Without guidance, security teams can’t keep pace with fast-changing permissions and integrations within Snowflake.