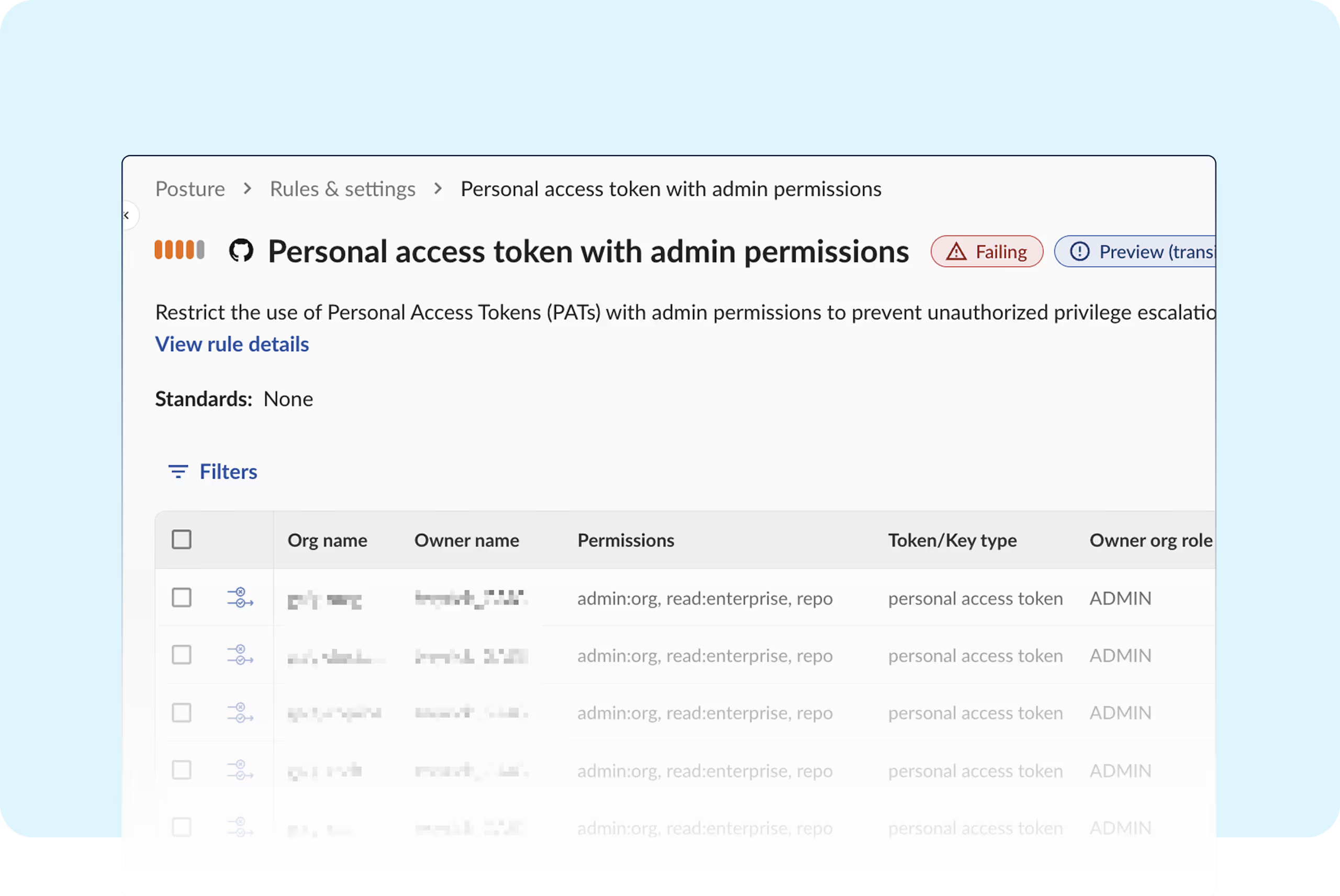
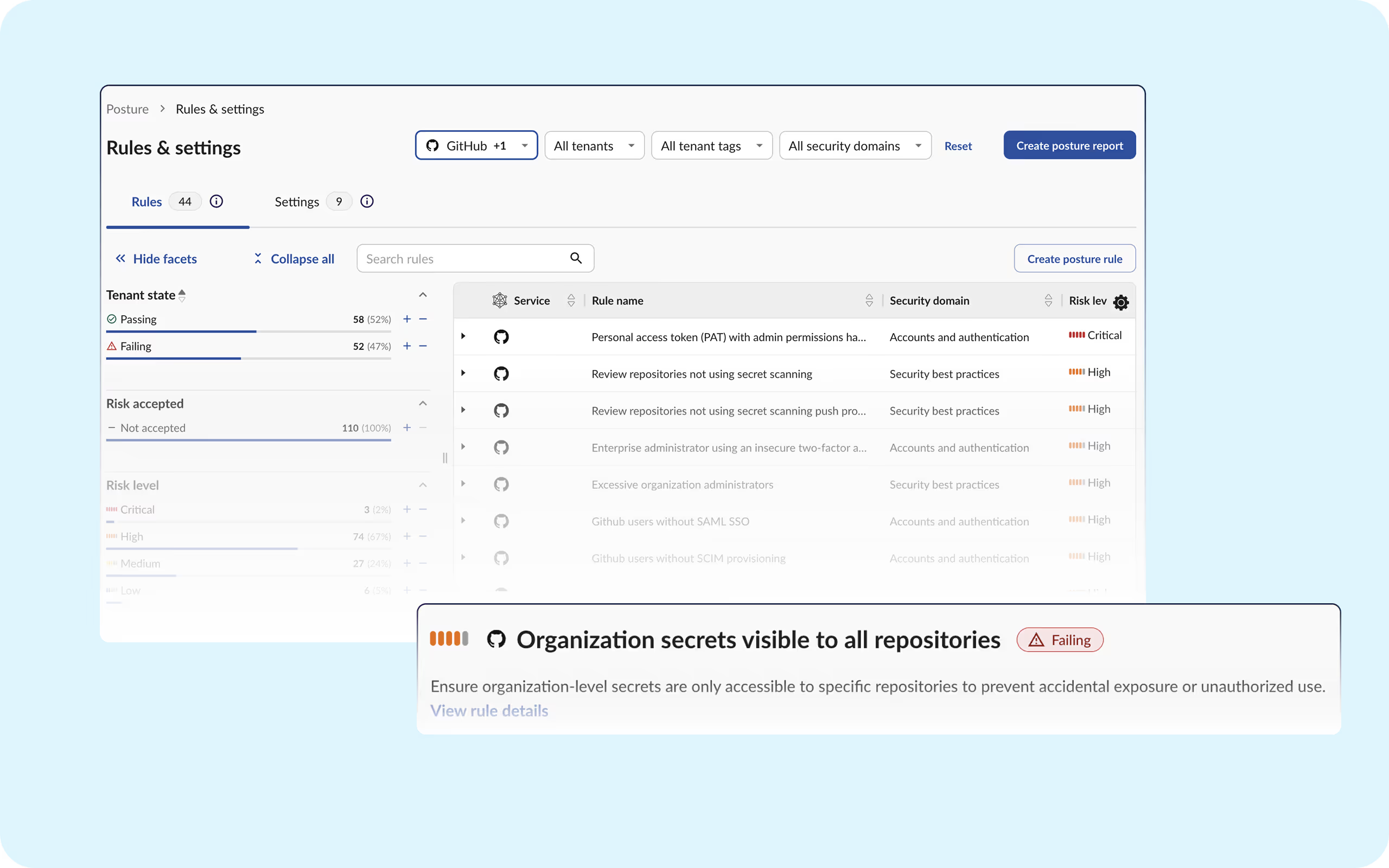
In 2024, an overprivileged and poorly managed GitHub token gave attackers wide access to private repositories and source code belonging to the New York Times.
Obsidian delivers defense in depth for GitHub, removing posture-related risk to your organization.
of organizations have sensitive SaaS data exposed
Obsidian Network Data
of breaches are caused by cloud misconfigurations
IBM
NYT repositories exposed from stolen GitHub tokens
NYT
Zero Trust wasn’t built to manage third-party SaaS risks like GitHub access, token sprawl, or app-level security controls.