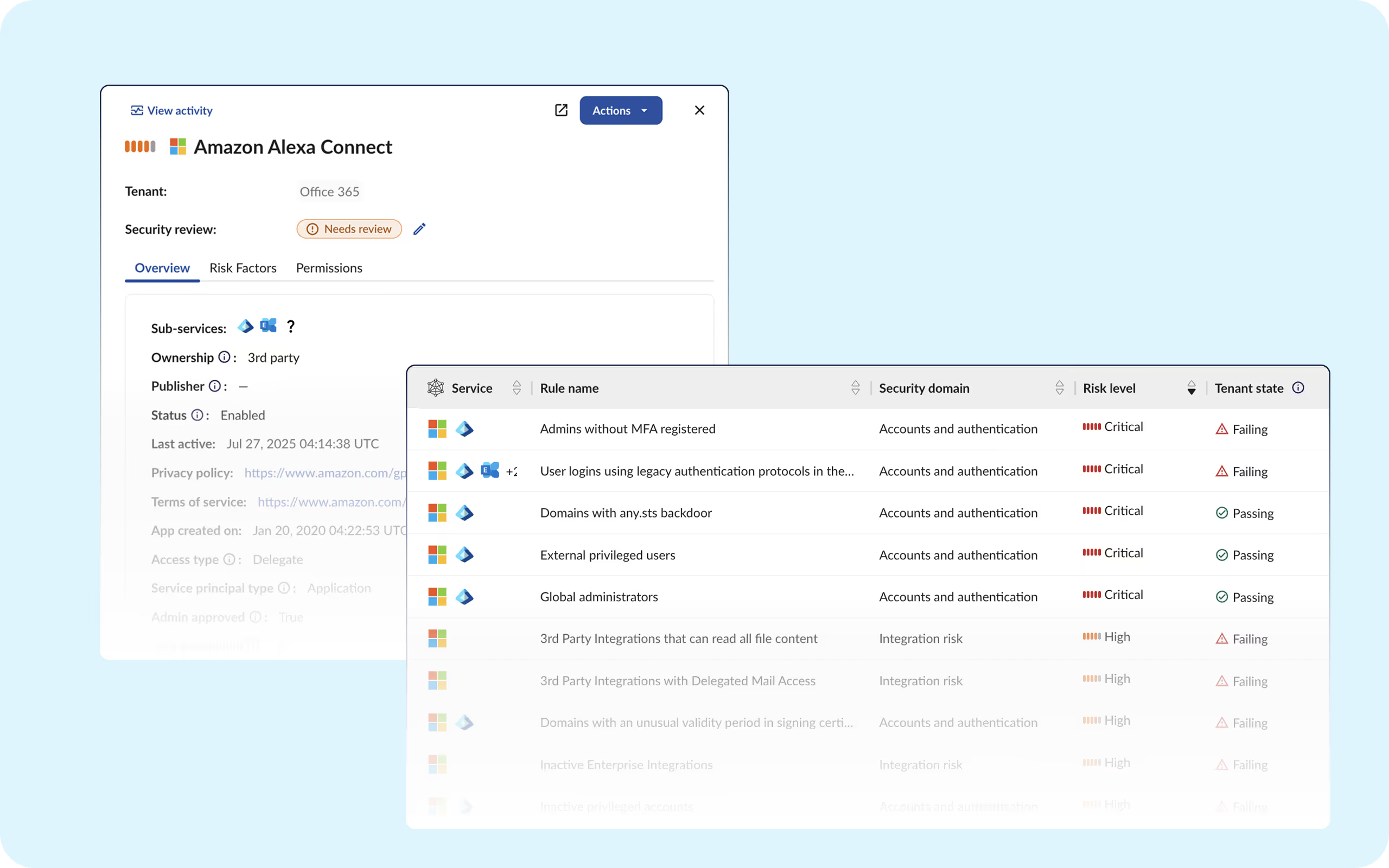
Microsoft OneDrive grants overly broad permissions to third-party apps, which allows them to access all content in a user's account.
Obsidian Security identifies which applications have overly permissive scopes to mitigate risks and manage third-party app permissions.

Although Microsoft 365 apps share a common login, differences in application usage, access, and settings complicate their security.
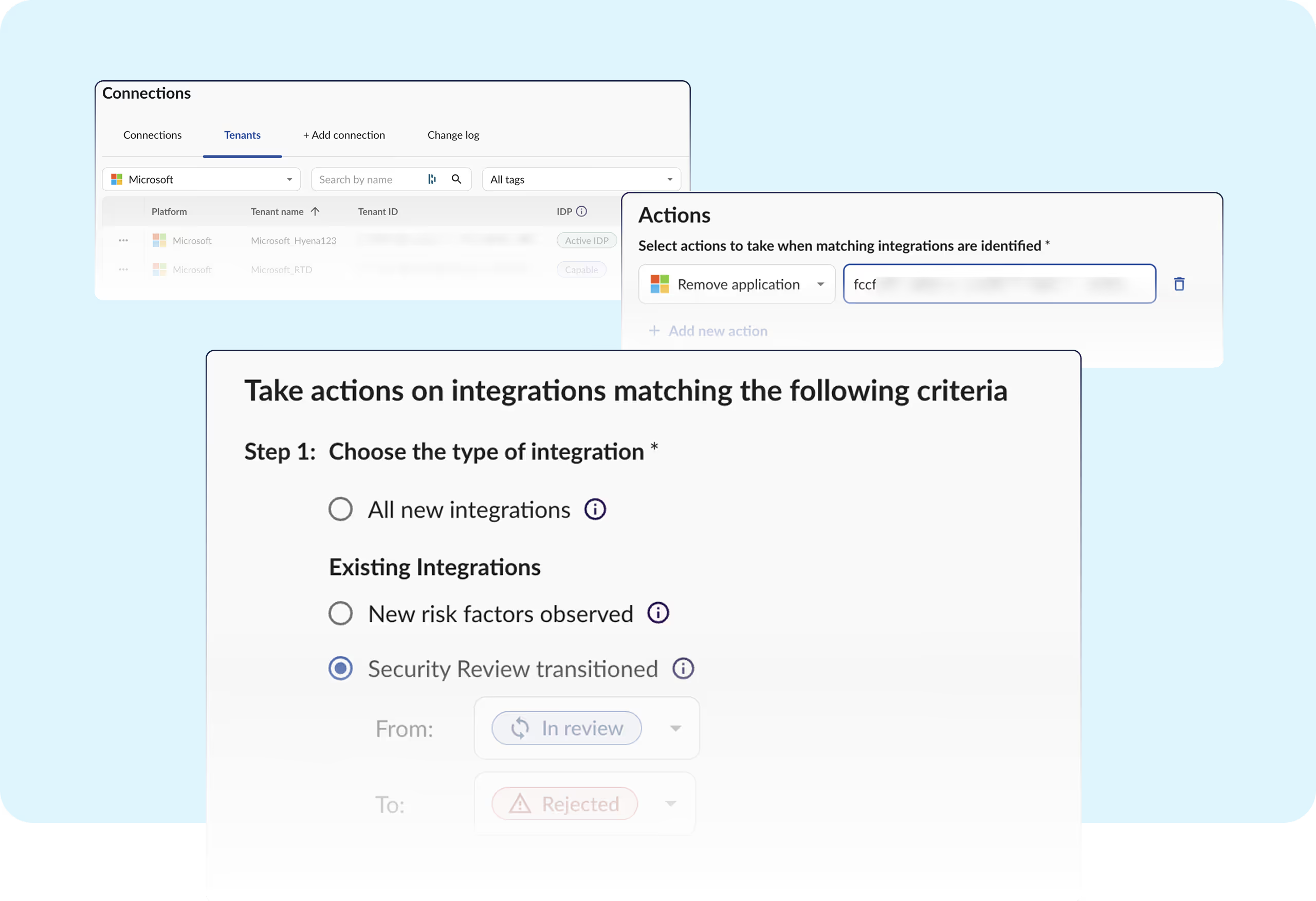
Microsoft 365 empowers data innovation, but also introduces risks from excessive access and third-party code. Obsidian’s SaaS-native security stack continuously monitors token usage, enforces secure configurations, and delivers identity-aware detection to help organizations mitigate modern SaaS threats.