Why Email Security Tools Miss Modern Phishing Threats
Even with email security and other defenses like MFA, phishing attacks are still prevalent and effective.
With defenses like email security and multi-factor authentication (MFA), phishing seems like it should be a threat of the past. But Obsidian Security’s research has proven that the opposite is true.
Phishing and credential theft are the first and second most common breach vectors. And with Generative AI (GenAI) in the mix, these attacks are only getting increasingly sophisticated.
Traditional email security, whether it’s a native solution (such as Microsoft Defender) or an external one (for example Proofpoint), can fail to catch phishing links for the same reasons. Here are four bizarre and clever ways attackers are getting past email security:
1. Using Cloudflare Turnstiles to Evade Detection
Cloudflare Turnstiles offer a smarter, user-friendly alternative to traditional CAPTCHAs. Instead of forcing users to identify traffic lights or bicycles, they analyze browser behavior, user interactions, and device characteristics to differentiate between human and bot visitors.
However, this design comes at a cost: Turnstiles automatically block scanning from email security solutions like Proofpoint and tools such as urlscan.io. Attackers have caught onto this gap and are taking advantage, hosting phishing sites on Cloudflare infrastructure and leveraging Turnstiles to stay hidden from detection tools. In a three-month period, Obsidian observed that 77% of phishing sites were hosted on Cloudflare, exploiting this visibility gap to evade detection.
2. Chaining URL Redirects and Abusing Link Rewriting
One method that traditional email security uses to detect malicious URLs is by scanning for known malicious URLs. To bypass URL detection, attackers often exploit URL redirects, using a chain of seemingly legitimate URLs that eventually land the user on a malicious site.
Many popular websites like Google or LinkedIn allow open redirects, which attackers abuse to piggyback off their trusted reputations. At Obsidian, we’ve observed phishing campaigns with over 10 redirect hops before reaching the malicious site, making it difficult for static blocklists or signature-based tools to catch the threat.
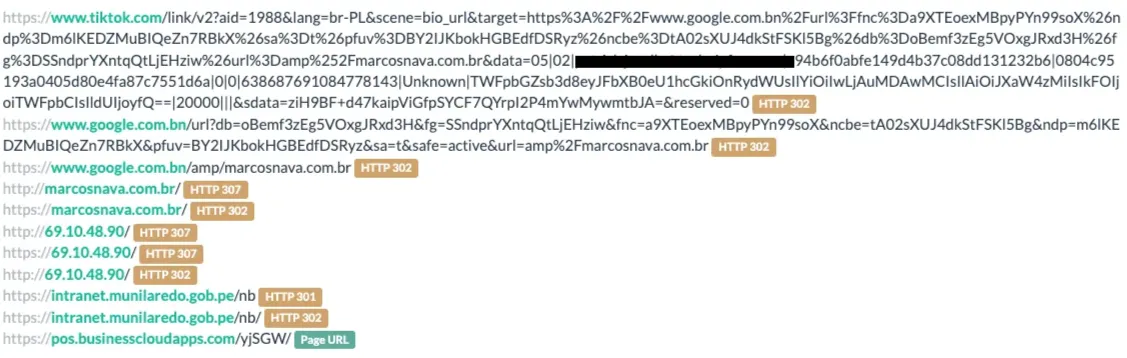
Attackers also exploit a common feature in email security tools called URL rewriting, where links are modified—often into a “safe” format like Microsoft Safe Links—so they can be scanned when clicked. But threat actors have learned to abuse this system by pre-wrapping their malicious links in these rewritten formats themselves.
When these tampered links arrive in a user’s inbox, they appear trusted because they match the rewritten structure security tools usually create, allowing them to bypass traditional link-based defenses and deliver phishing pages undetected.
3. Using Trusted Platforms (Dropbox, SharePoint) to Deliver Phishing Payloads
Attackers frequently abuse well-known services such as Dropbox, OneDrive, and SharePoint to deliver malicious content. Because these services are widely used and implicitly trusted by email security tools, malicious messages sent through them often evade detection.
On the surface, a phishing link disguised as a shared document looks identical to a legitimate file: same sender domain, same branding, and hosted on a known service. URL reputation detection might fail since the harmful links in these emails can be uniquely created for each recipient.
4. Delivering Phishing Links Outside the Inbox
Phishing ultimately doesn’t happen in the inbox—it happens in the browser. That’s where users enter credentials and attackers gain access. And cybercriminals know they don’t have to go through your corporate email to get there.
One growing area of concern is phishing through personal inboxes. More and more employees are signing into their personal accounts on company devices, but email security tools such as Proofpoint, Abnormal, and Mimecast only monitor corporate inboxes. Any malicious link sent to a personal inbox will freely bypass defenses, straight to the user.
And attackers aren’t limiting themselves to emails. Phishing links are now distributed over collaboration platforms like Microsoft Teams or Slack, SaaS-native chats, and community forums. Having in-browser detection and monitoring is needed to catch and stop these phishing attacks.
Building a Comprehensive Security Strategy for Phishing
The primary challenge facing email security solutions is the vast number of phishing URLs generated daily. Most domains exist for only a few days before being shut down. However, user reports can take time to register, and validation may take even longer before a domain is flagged as malicious. At Obsidian, we’ve seen data exfiltrations happen in as fast as nine minutes, proving that proactive solutions must be implemented.
To ensure comprehensive protection against the speed of modern-day phishing attacks, organizations must build a layered defense strategy—one that extends protection from the inbox all the way to the browser. Get started for free to begin detecting AiTM phishing threats.




