Cyber attackers continuously refine their strategies to evade standard security measures. Among the newest and most misleading techniques is the fake CAPTCHA attack. This tactic deceives users by presenting what appears to be a genuine verification challenge, but instead activates harmful code and steals personal information. What distinguishes these attacks from typical phishing attempts is their entry point—they infiltrate through web search engine optimization (SEO) rather than email, allowing them to circumvent traditional phishing detection systems and email security tools.
How fake CAPTCHA unfolds
At a high level, the attack involves the following steps:
- A victim is lured into a compromised/malicious website
- A seemingly legitimate CAPTCHA is presented to the victim, who is asked to follow specific instructions in order to pass the challenge
- Malicious content is inserted into the victim’s clipboard. The victim then follows the instructions provided to open the “Run As” dialog, paste the contents of the clipboard, and press enter
- The malicious code is executed, typically reaching out to a remote location to download a malicious script. The script is executed, install malware, typically info stealers or remote access tools.
Since early this year, Obsidian has been tracking this threat's development and has identified several variations of these attacks.
New techniques
A new attack vector is emerging alongside traditional phishing emails: malicious websites ranking high in Google search results through aggressive SEO techniques. This approach is particularly effective because the entire attack sequence—from search to website interaction—occurs within the user's browser, completely circumventing standard phishing protections like Secure Email Gateways (SEGs).
When victims click on these malicious links, they typically encounter a fake CAPTCHA that appears immediately after a genuine Cloudflare Turnstile verification. This two-step approach serves dual purposes: it makes the fraudulent CAPTCHA appear more legitimate (as if the first verification failed), and it prevents security tools from examining the actual malicious content. The use of Cloudflare Turnstile as an evasion technique is becoming increasingly common, and our previous investigations have consistently found it being used in credential theft campaigns.
The downloaded malware typically belongs to well-known families of info stealers, designed to extract sensitive data—typically browser cookies and stored passwords. By harvesting and replaying web session cookies, threat actors can hijack a victim’s corporate identity. While these malware variants are well-documented by EDR vendors and won’t be the focus here, it is worth noting that Ukraine’s CERT has specifically warned about APT groups using this technique to compromise Office 365 accounts.

Stop the attack from the source
When attackers use Google search to lure users to malicious sites, the browser becomes the first—and most effective—line of defense. With the Obsidian secure browser extension, we see exactly what the user sees and can proactively block threats before they take the bait.
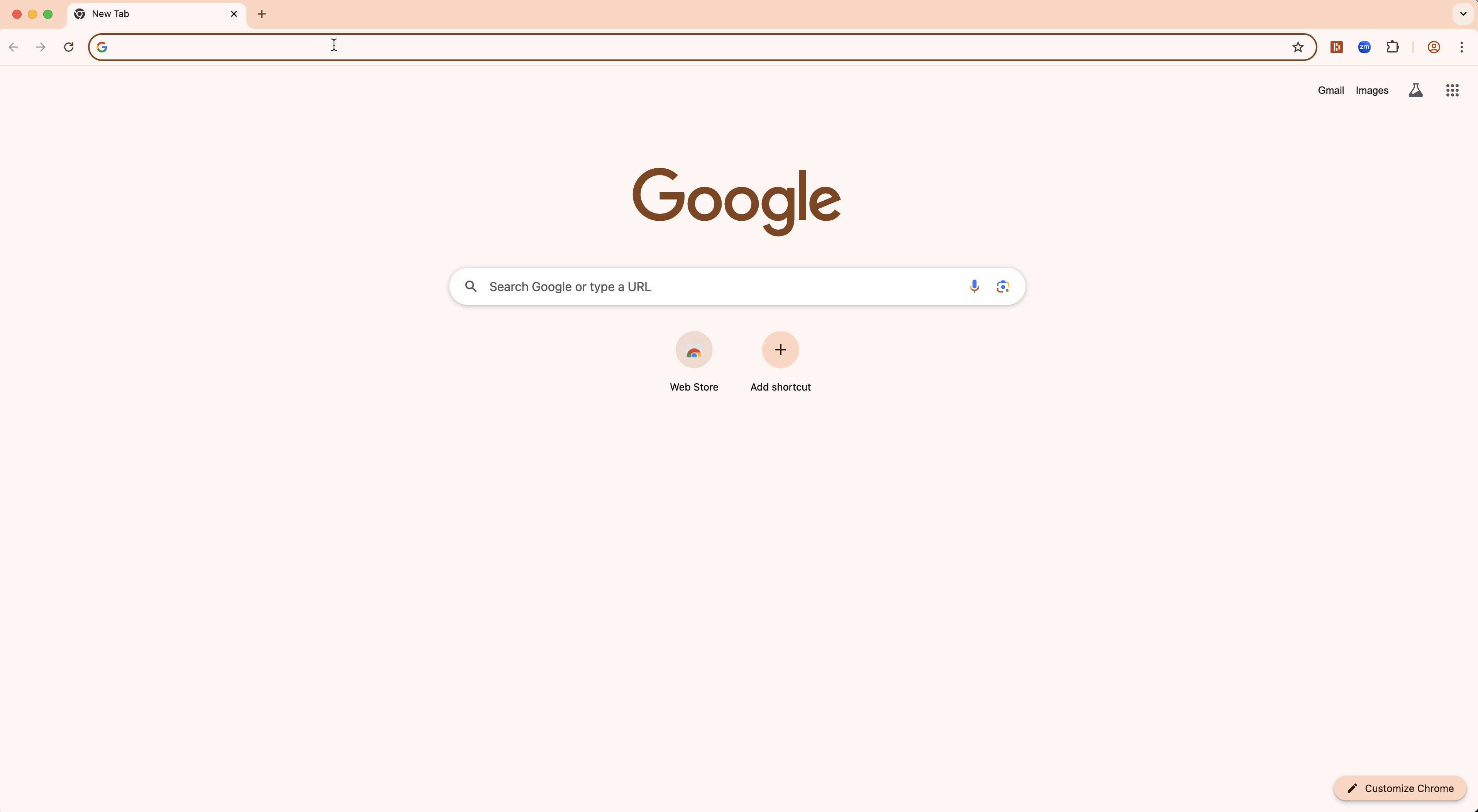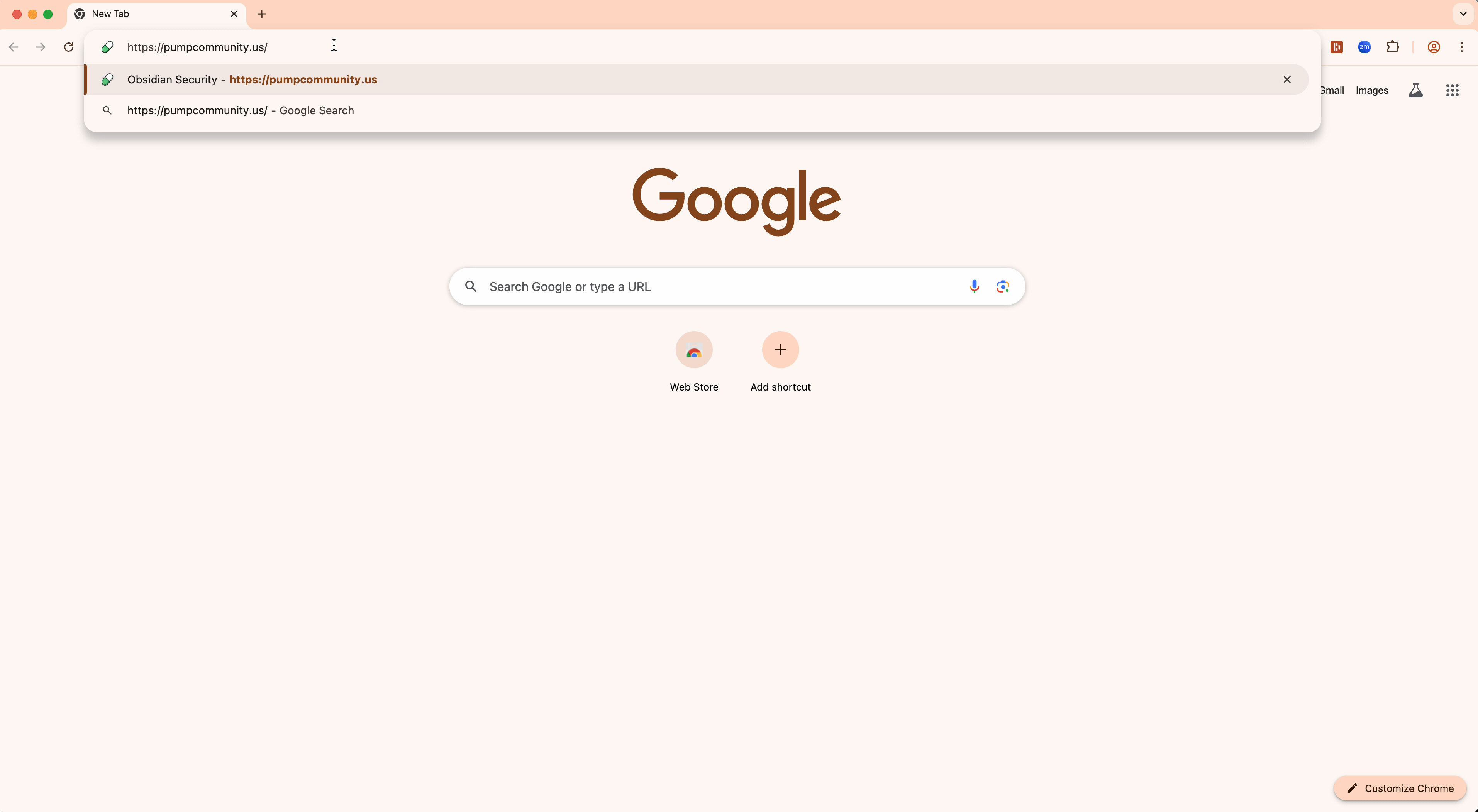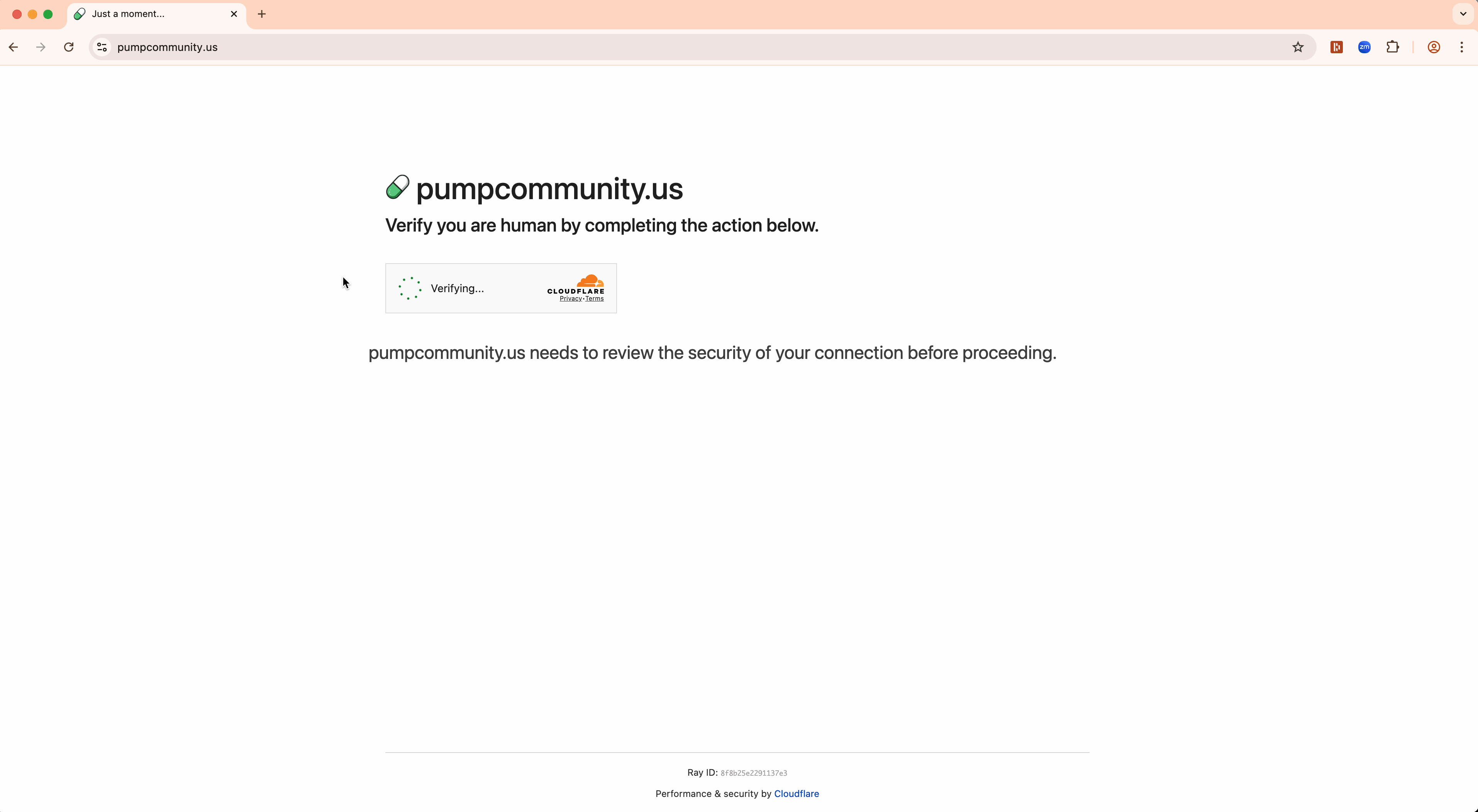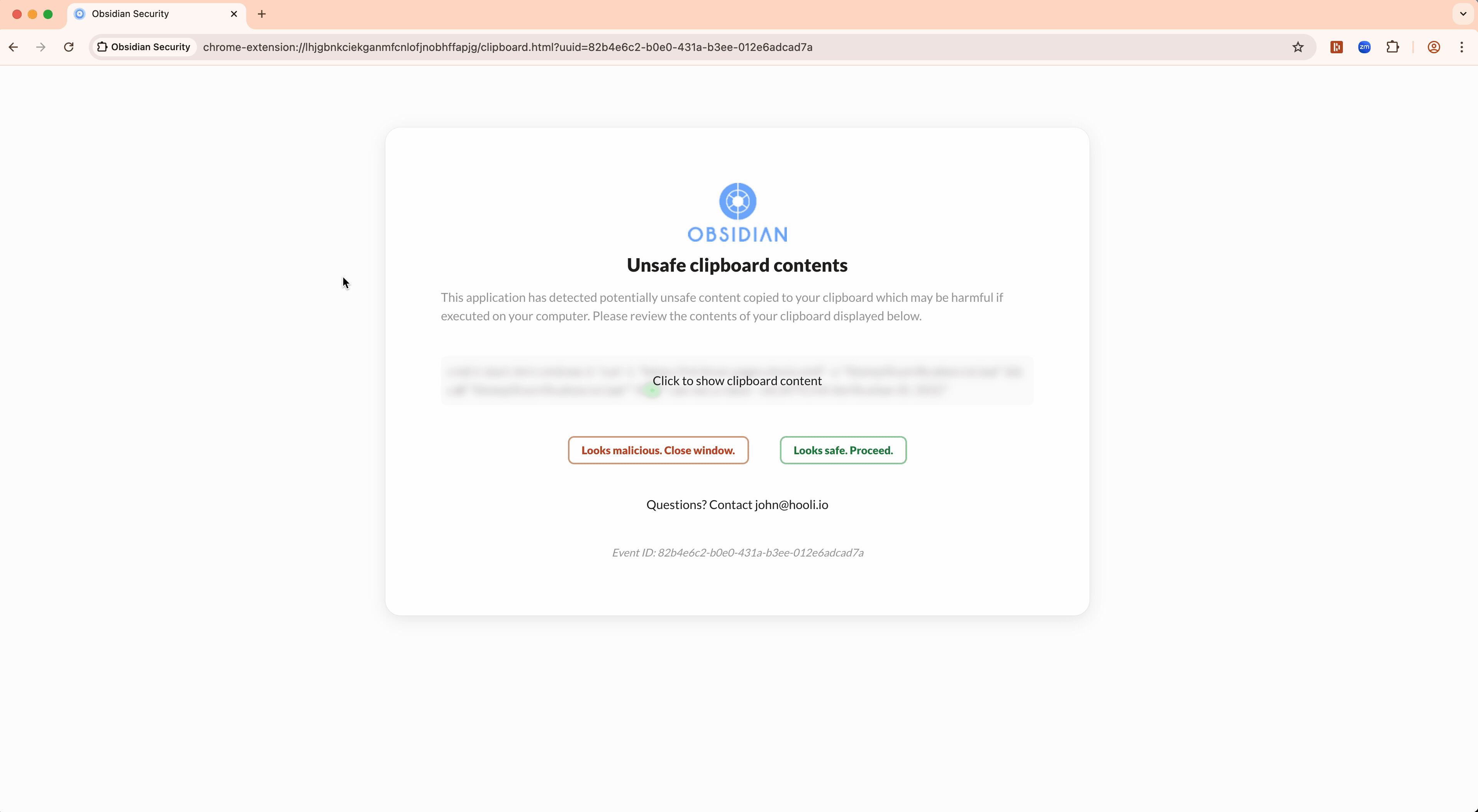
Even when phishing emails are protected behind Cloudflare Turnstile, browser-layer defense remains effective. Turnstile can blind traditional email security solutions, but Obsidian stays alert—catching threats where others can’t.
While EDR solutions are valuable for detecting and responding to malware, they often kick in after the device has already been compromised—when the damage is done. By detecting and blocking threats at the browser layer, we stop attacks before they reach the device, eliminating the need for costly remediation and response.
The bottom line
Fake CAPTCHA attacks represent a growing blind spot in enterprise security—exploiting user trust, and web-layer blind spots that traditional tools can't catch. Whether the attack is delivered through a phishing email or a poisoned search result, the entry point is always the same: the browser.
EDR and email security solutions have their place, but also their limitations. Real protection starts at the source—before users are tricked into executing malicious code. That’s where browser-native defenses like Obsidian shine.
To stay ahead of evolving threats:
- Focus on preventing attacks at the browser level, not just detecting them after the fact.
- Deploy solutions that see what users see and stop clipboard-based execution chains.
- Educate users on deceptive tactics like fake CAPTCHAs.
In a threat landscape where social engineering is more convincing than ever, proactive browser-layer defense isn’t optional—it’s essential.
Indicators of compromise (IOCs)
x10[.]mxcoinspaceteam[.]com
payhub-secure[.]com
soubtcevent[.]com
cambodiatouristservice[.]com
fu-xu-ry[.]comomniflex-secure[.]com
securedmicrosoft365[.]com
sso-accountservices[.]com
complaintguest2[.]com
komi[.]cam
roomnum-998388[.]world
claim-pamp[.]fun
cfcaptcha[.]com
talentstack[.]icu
roomsvisitor999837[.]worldapril-boking-recapt09993748[.]com
captcha-cf[.]com
94[.]181[.]229[.]250
94[.]156[.]177[.]6
198[.]91[.]81[.]11
198[.]91[.]81[.]13
192[.]185[.]101[.]64
20[.]217[.]17[.]201
207[.]174[.]214[.]13
References
https://www.cisecurity.org/insights/blog/active-lumma-stealer-campaign-impacting-us-sltts
https://cert.gov.ua/article/6281123