Highlights:
- File picker OAuth flaw in OneDrive leads to over-permissive app access, causing significant OneDrive data exposure via third-party apps.
- Third-party app permissions, particularly the files.read.all scope, grant excessive access, increasing organizational risk.
- "One-click" integrations quickly result in widespread OneDrive data exposure due to readily granted over-permissive app access.
- Obsidian Security helps identify and mitigate risks from over-permissive app access and manage third-party app permissions to prevent OneDrive data exposure stemming from the file picker OAuth flaw.
How One Click Leads to OneDrive Data Exposure
Security concerns surrounding Microsoft OneDrive have recently surfaced. Researchers found that numerous third-party app permissions, including for popular services like Slack, ClickUp, Trello, and ChatGPT, are overly broad and grant them full access to users' OneDrive files.
This issue stems from the OneDrive File Picker's OAuth permissions, which allow these applications to access all content in a user's OneDrive account, even when only a single file is uploaded. So hey, technically it’s not entirely your fault.
The urgency here is that employees can connect these tools with just a click, and rarely are thinking of the repercussions or security impact. So the overpermissions can quickly spiral.
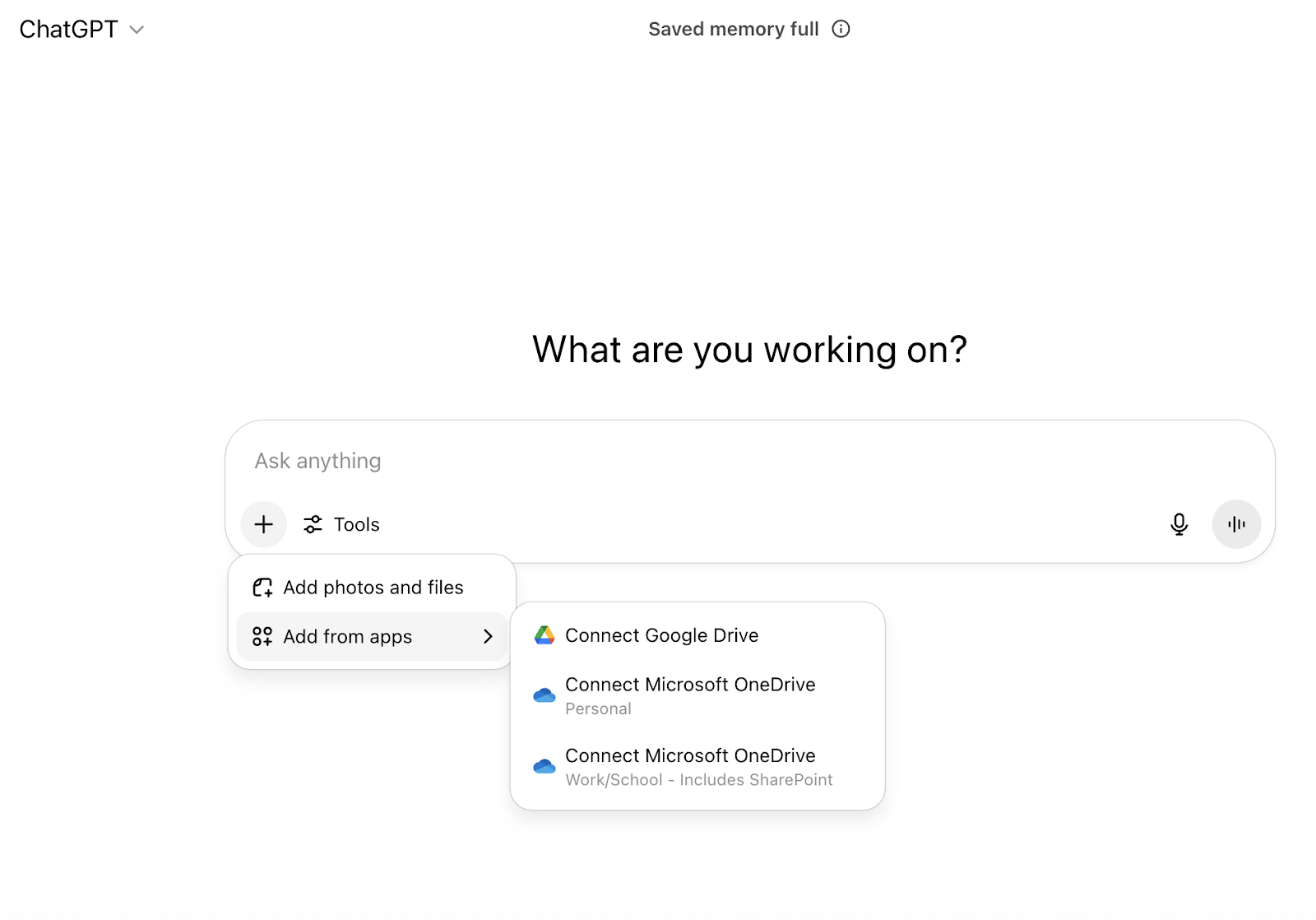
Understanding File Picker OAuth Scopes
OneDrive File Picker simplifies the process of connecting your web apps to documents stored in OneDrive. It speeds up file access and sharing, but this convenience can come with security trade-offs.
The OneDrive File Picker requests read access (Files.Read for your own files or Files.Read.All for files shared with you) to the entire drive, due to the lack of granular OAuth scopes. As shown in the example below, an action like this could grant ChatGPT access to all your files (including PII, financial records, and intellectual property).

Users are prompted for consent during uploads, but the prompt lacks clarity about how much access is actually granted. On top of this, users rarely read all the fine print. Between the two—ease of integration and minimal warning of what is being shared—employees are often agreeing to more than they realize.
This puts organizations that allow third-party applications to access OneDrive at risk of data breaches and compliance violations… because GenAI tools, once authorized, can quickly scan, find, and exfil data in real time. We aren’t talking about weeks or days! We’re talking about seconds. In the wrong hands, that’s all it takes for a smart tool to become a smarter adversary.
In OneDrive, the attackers can exploit this access to steal, alter, or encrypt data that’s stored. Additionally, the latest version of the OneDrive File Picker requires developers to manage user authentication using a tool that stores sensitive credentials insecurely in the browser, increasing the risk of unauthorized access.
How Obsidian Security Flags and Fixes Excessive App Access
Obsidian Security identifies which applications have overly permissive scopes, so you can regain control and rest easy at night.
Obsidian offers several useful tools to help you manage your security posture. One of the key features is the Posture Management Module.
With Obsidian’s SSPM solution, you can define custom rules that flag applications requesting sensitive permissions like Files.Read and Files.Read.All. This helps security teams proactively monitor for excessive access and enforce least privilege principles across integrated tools.
Once saved, Obsidian will generate a list of all applications requesting those scopes, giving you clear visibility into potential access risks.

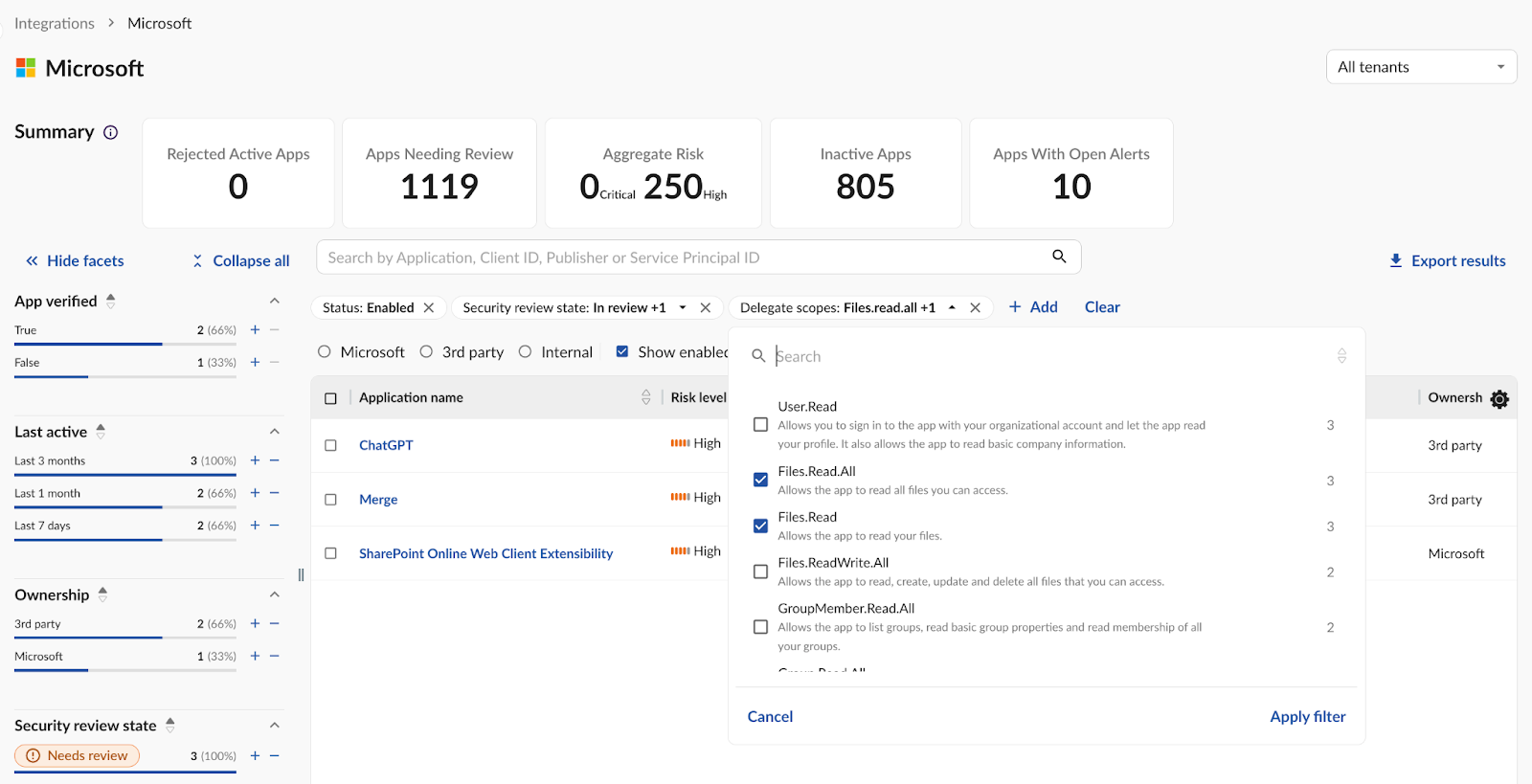
There’s also the Integration Risk Management (IRM) module in Obsidian. IRM gives security teams the option to quickly filter and review applications based on the permissions they’ve been granted—such as Files.Read or Files.Read.All—to identify potential overexposure and take corrective action. As we know, over permissioned apps can pose serious risks.
Once selected, you should see a clear list of all applications requesting those scopes. You can take action where it’s needed and only ensure the right apps have the right level of access.
Strengthen Your SaaS Posture with Obsidian Security
SaaS security is a team sport that requires alignment across IT, security, and all business units. It is important to:
- Educate app owners on how they’re using third party apps.
- Help users understand the potential risks associated with the apps they introduce, not only to themselves but to the organization.
- Enforce controls or use tools such as the Obsidian Browser Extension to prevent unsanctioned or overly permissive app usage before it becomes a problem
Visibility and collaboration are key to staying secure. Obsidian is here to help. Contact us today to learn more.




