Overlapping IOCs, dozens of victims, and a chaotic Telegram spectacle have led Obsidian researchers to conclude that a partnership or merger of UNC6040, UNC6240, and UNC3944 may have occurred.

Over the past few months, two names kept resurfacing in our research: ShinyHunters and Scattered Spider.
ShinyHunters have been tied to a surge in Salesforce-related attacks, including breaches at Google and Workday. Scattered Spider, meanwhile, has carried out highly disruptive intrusions against airlines, retailers, and insurers.
What caught our attention was not just the size of these campaigns but the overlap in tradecraft. Scattered Spider built its reputation on voice phishing and helpdesk social engineering. These tactics are particularly effective because they sidestep traditional security controls. ShinyHunters have taken a quieter path since 2020. They rely on stolen or leaked credentials to access SaaS environments, steal data, and extort victims.
Until recently, the two groups were considered separate, but the Salesforce attacks changed that.
The Salesforce Attacks
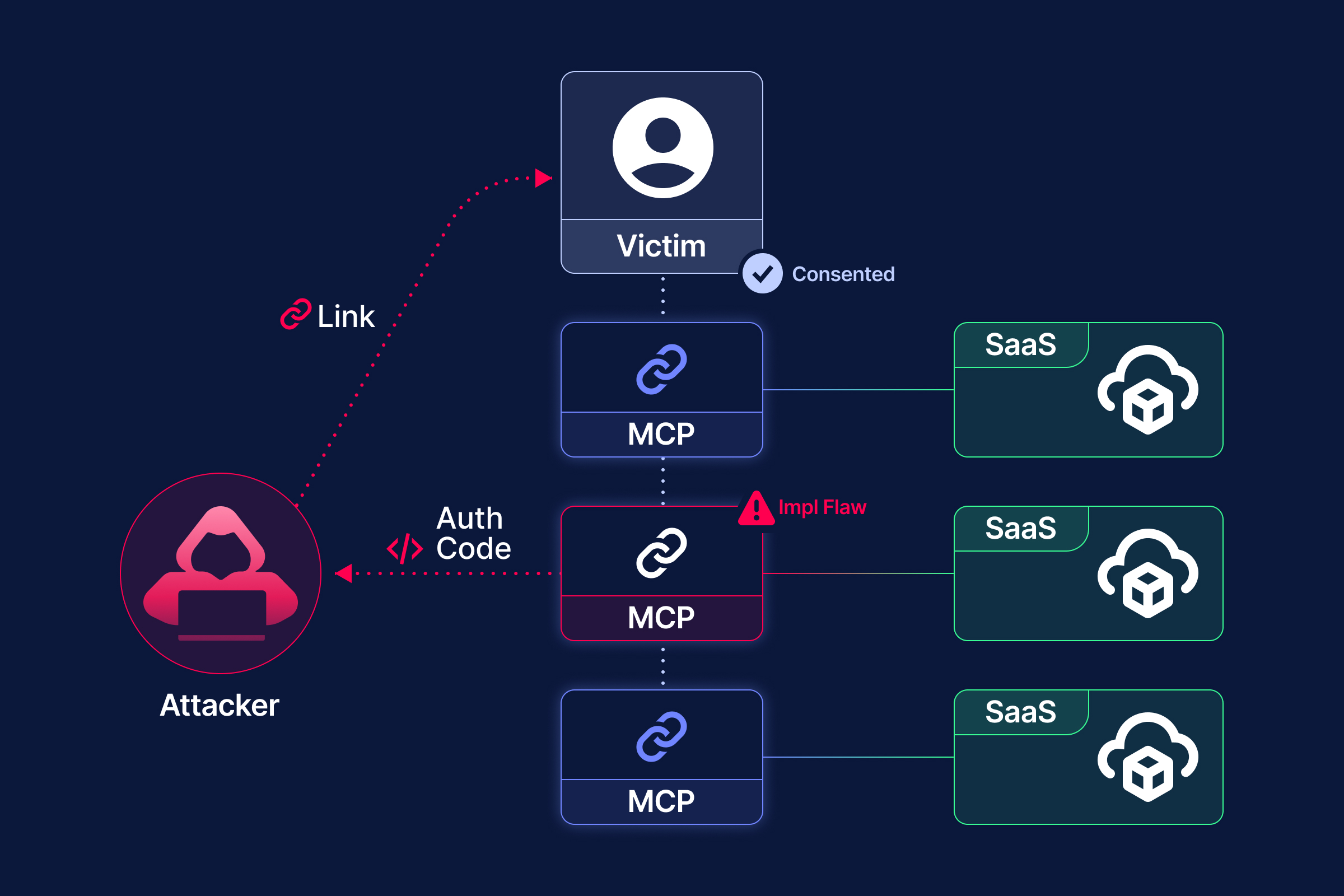
In June and July 2025, we observed a wave of Salesforce CRM data thefts notable for both their scale and the simplicity of the attack chain. The attackers did not exploit any Salesforce platform vulnerabilities. Instead, they used traditional voice phishing combined with malicious OAuth ‘Connected Apps’ to obtain tokens, granting API access and enabling bulk exports of CRM data.
The social engineering was straightforward. Attackers called employees, posing as IT support, and directed them to Salesforce’s “Connect an App / enter code” screen. When victims entered the attacker-provided code, a trojanized Data Loader-style app captured OAuth tokens. These tokens bypassed MFA controls, allowing attackers to extract large volumes of CRM records via the Salesforce API.
The campaign was broad, impacting dozens of organizations across technology, retail and luxury goods, aviation, and insurance. Stolen data primarily included CRM records such as names, emails, phone numbers, account notes, and loyalty program details. Core systems were not directly affected, but the exposure of customer and business data at this scale is significant.
Prominent disclosed victims include Google’s corporate Salesforce instance, Qantas, Allianz Life, LVMH/Chanel, and Workday. Attribution varies across sources: Google tracks the intrusion as UNC6040 and the subsequent extortion as UNC6240, while the actors claim affiliation with ShinyHunters. Open-source reporting, including DataBreaches.net, supports this connection, highlighting extortion emails sent to Google during the campaign.
The overlap in tactics drew particular attention. Multiple intelligence reports noted that the voice-phishing and helpdesk social engineering resembled Scattered Spider operations. Combined with reports of potential collaboration, this raises questions about whether ShinyHunters and Scattered Spider are now working together.
The campaign extended beyond theft. After the data exports, victims received pay-or-leak extortion demands, with some attackers posting sample data to pressure companies into paying.
For defenders, some quick recommendations:
- Enforce strict control over Connected Apps and OAuth scopes
- Regularly revoke suspicious or unused tokens
- Monitor Salesforce API usage for anomalous bulk exports
- Train helpdesk staff and end users to recognize voice phishing tactics
This campaign illustrates how simple social engineering combined with token abuse can bypass technical controls, emphasizing the need for both user awareness and proactive platform monitoring.
Attribution
The 2025 Salesforce attacks have been confidently attributed to ShinyHunters (UNC6040 and UNC6240). This attribution was straightforward and widely accepted as fact.
That changed on August 3, when Dissent Doe, the author of databreaches.net, reported that the alleged leader of ShinyHunters claimed the Salesforce attacks were carried out in partnership with Scattered Spider.
Dissent had previously spoken with ‘Shiny,’ which enabled her to reference details from past conversations to verify she was speaking with the correct person.
“One of the first questions I asked him was to name someone we both hated. Without hesitation, he correctly named the person and added three aliases the individual used. I’ve redacted his answer in the screengrab, but it was correct. During the chat, Shiny also showed me several screen grabs of our past chats. At one point, he spontaneously inquired about someone he had asked me about several times in the past — someone he cares about. He asked how that person was doing now, which is a question he had often asked me.” —Dissent via Databreaches.net
In a separate conversation, Dissent spoke with Shiny, during which ShinyHunters once again explicitly claimed a partnership with Scattered Spider. Dissent asked whether Scattered Spider members had remained active since the arrest of four of their members, whether they were targeting new victims, and if Shiny could provide any insight into who those victims might be. Shiny responded:
“They’ve been working with us. Despite everyone’s efforts to halt the Salesforce-related attacks, we continue to attack multi-billion- to multi-hundred-billion-dollar companies daily and successfully dump them. We urge law enforcement and Google Threat Intelligence to collaborate closely with CrowdStrike and Unit221b to effectively counter and put an end to this threat. Google Threat Intelligence and law enforcement have shown nothing but incompetence and inaccuracy.”
Google Threat Intelligence has been actively monitoring the situation, particularly tracking the activity and TTPs of the four alleged Scattered Spider members arrested in the U.K. These four individuals, however, do not represent the full scope of Scattered Spider.
Meanwhile, threat intelligence from Mandiant and other firms has largely adhered to strict group-based attribution, assigning UNC6040 to social engineering and data exfiltration activity, and UNC6240 to extortion.
Dissent recommends treating ShinyHunters and Scattered Spider as a single entity, arguing that rigid labeling only adds confusion—a view shared by Obsidian researchers.
Strict labeling of threat actors, especially groups originating from ‘The Com,’ can be problematic due to the fluid and overlapping nature of their ecosystem. Overly rigid labels can fragment intelligence, obscure techniques, and lead to inaccurate guidance, such as when Mandiant reported that Scattered Spider had ceased operations. Obsidian believes this claim was incorrect.
The bottom line: Scattered Spider has not stopped—they have evolved.
Telegram Chaos Suggests Threat Groups Have Combined Forces

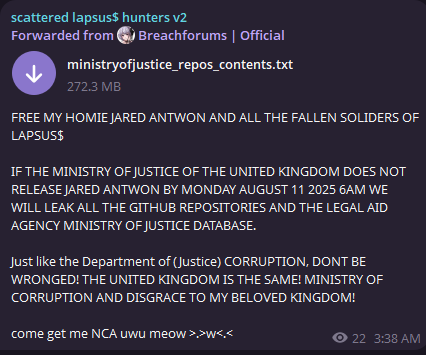
A Telegram channel appeared on August 8th, conflating three groups: ShinyHunters, Scattered Spider, and Lapsus$. Since the first channel emerged and was subsequently banned, several others have surfaced. These channels have been highly unpredictable.
While Obsidian researchers could not verify all the content, if the claims are taken at face value, the channels have shared a wide range of material, including exploits, partial data leaks, advertisements for stolen data, doxxing claims, initial access requests, memes, taunts, and threats.

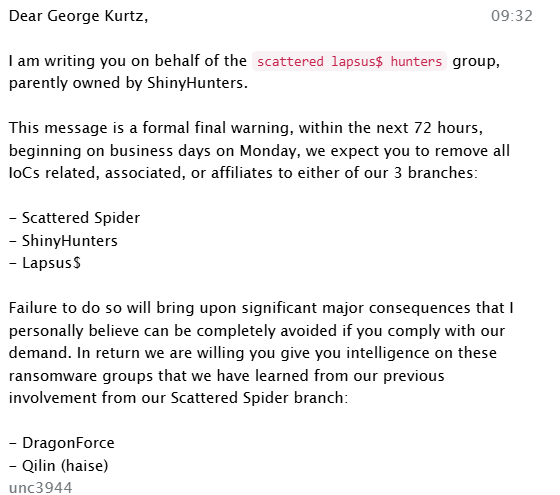
This represents only a small selection of the messages. Between threats and data leaks, channel admins frequently post unrelated or inflammatory content. The chaos is amplified by companion chats linked to the main channel, which allow anyone to post. In the past few days, channel admins have also initiated video chats on three occasions. Obsidian researchers observed these sessions but have no insights to report at this time.
At the time of writing, the most active channel has been cleared of messages and renamed “Deleted Channel.” Other channels under the name “Scattered Lapsus$ Hunters” have since appeared, but their authenticity remains uncertain.
A Note on Lapsus’ Inclusion
Lapsus$ was first observed in 2021 with an attack on Brazil’s Ministry of Health. In early 2022, the group targeted Okta, Nvidia, Samsung, Ubisoft, T-Mobile, Microsoft, Globant, and other organizations. After a period of dormancy, Lapsus$ resurfaced with an attack on Uber in late 2022.
Following this series of high-profile attacks, several members of Lapsus$ were arrested throughout 2022.
Since then, the group has remained largely inactive, though individuals continue to claim affiliation. A post in the Scattered Lapsus$ Hunters Telegram channel suggests that Lapsus$’s inclusion may be more of a homage to “all the fallen soldiers of Lapsus$,” referencing a message demanding their release from prison.
Technique Comparison
Below, we have mapped the MITRE ATT&CK techniques observed in the Salesforce incidents against the known tactics and techniques of Scattered Spider:
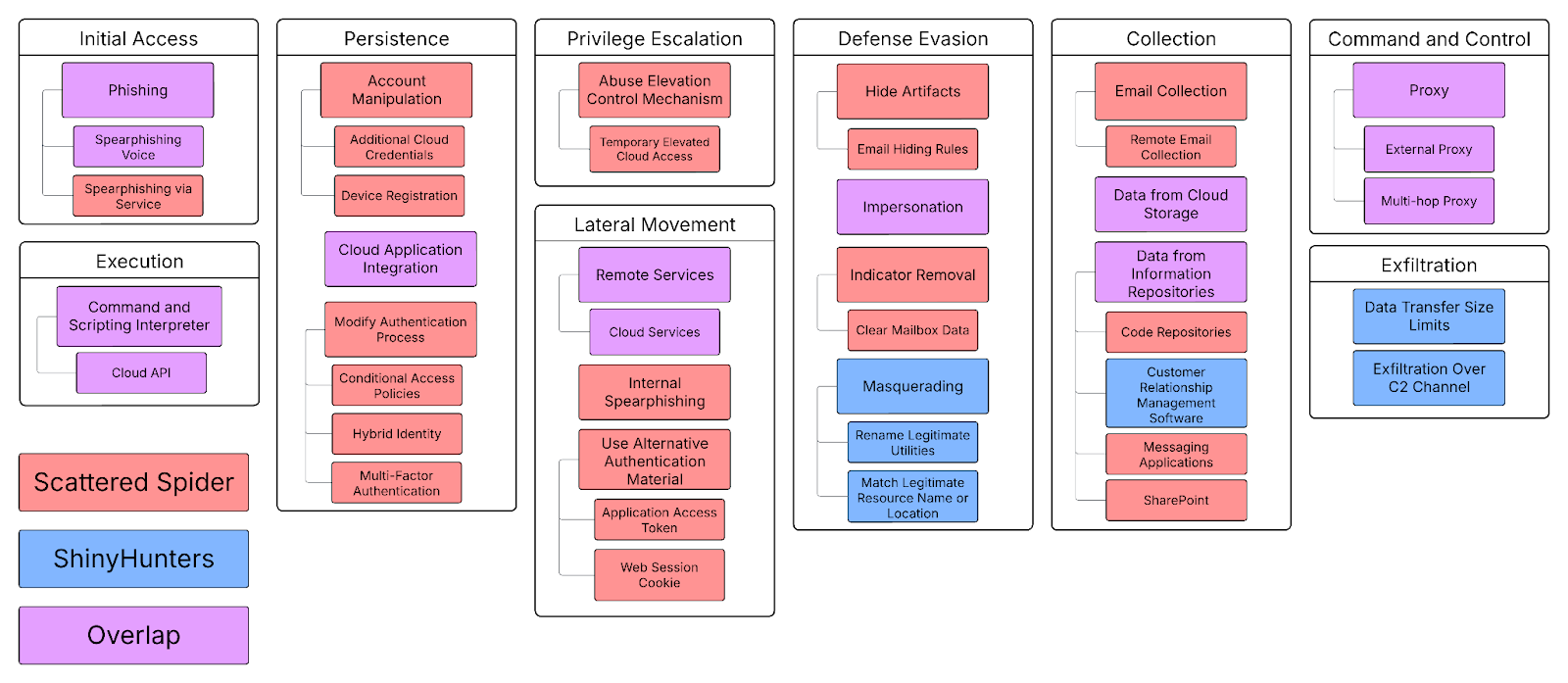
Scattered Spider techniques are shown in red, ShinyHunters (Salesforce-specific) in blue, and overlapping techniques in purple.
While many techniques observed in Scattered Spider operations were not seen in the Salesforce attacks, the overlap is notable and provides further evidence that some form of partnership may have occurred.
Recommendations for Securing Your Organization
Consistent with guidance from Falcon Feeds, we recommend:
- Enforcing SSO-only with phishing-resistant MFA (WebAuthn/FIDO2): Require Single Sign-On (SSO) for all users accessing SaaS applications. Crucially, implement phishing-resistant MFA methods such as FIDO2 security keys or certificate-based authentication. Disable less secure fallback options like SMS, voice calls, or basic push notifications, which are highly vulnerable to social engineering and SIM-swapping attacks.
- Restricting OAuth-connected apps: Apply strict controls and perform regular audits of OAuth-connected applications. Generate alerts for any new grants, unusual token creation, or anomalous SOQL (Salesforce Object Query Language) query patterns.
- Monitoring large exports and atypical user-agent/ASN geographies: Maintain robust logging and alerting for unusually large data exports from SaaS platforms. Use anomaly detection to flag logins or data access attempts from atypical user-agent strings or unexpected Autonomous System Number (ASN) locations.
Aligning with Salesforce Ben, we also recommend:
- Reviewing API keys, integration users, and data export jobs: Regularly audit and rotate API keys. Ensure integration user accounts follow the principle of least privilege. Review and streamline automated data export jobs to reduce unnecessary exposure of sensitive data.
Final Thoughts
The 2025 Salesforce attacks show just how quickly threat actors can adapt and combine forces. ShinyHunters and Scattered Spider may have joined skills, making attacks more powerful and harder to spot. The lesson is clear: even simple social engineering can have a big impact. Organizations need strong user awareness, careful monitoring of OAuth and API activity, and tight controls on access to keep their data safe.
Want to Learn More from the Experts? Obsidian’s Recent Trends in Advanced SaaS TTPs explores how attackers target help desks, MFA, and admin accounts across SaaS environments. Learn actionable steps to detect threats, respond effectively, and reduce dwell time from evolving SaaS and AI-powered attacks.
Sources:
- DataBreaches.net. Are Scattered Spider and ShinyHunters one group or two? And who did France arrest? August 3, 2025. https://databreaches.net/2025/08/03/are-scattered-spider-and-shinyhunters-one-group-or-two-and-who-did-france-arrest/
- DataBreaches.net. Scattered Spider has a new Telegram channel to list its attacks. August 9, 2025. https://databreaches.net/2025/08/09/scattered-spider-has-a-new-telegram-channel-to-list-its-attacks/
- DataBreaches.net. Scattered Spider is NOT quiet. They’re just under another name now. August 5, 2025. https://databreaches.net/2025/08/05/scattered-spider-is-not-quiet-theyre-just-under-another-name-now/
- FalconFeeds. Scattered LAPSUS$ Hunters: Investigative Timeline. Aug 12, 2025. https://falconfeeds.io/blogs/scattered-lapsus-hunters-investigative-timeline
- Google Cloud Blog. The Cost of a Call: From Voice Phishing to Data Extortion. June 4, 2025. https://cloud.google.com/blog/topics/threat-intelligence/voice-phishing-data-extortion
- National Crime Agency. Retail cyber attacks: NCA arrest four for attacks on M&S, Co-op and Harrods. July 10, 2025. https://www.nationalcrimeagency.gov.uk/news/retail-cyber-attacks-nca-arrest-four-for-attacks-on-m-s-co-op-and-harrods
- Salesforce Blog. Protect Your Salesforce Environment from Social Engineering Threats. Updated Mar 14, 2025. https://www.salesforce.com/blog/protect-against-social-engineering/
- SOCRadar. Salesforce-Related Data Breach Affecting Multiple Companies. Aug 12, 2025. https://socradar.io/salesforce-data-breach-affecting-multiple-companies/