CLOUD THREAT DETECTION
Detect Account TAKEOVER and INSIDER THREAT Early
Obsidian enables early detection of account compromise and insider threat in cloud applications and services by continuously monitoring and analyzing activity. Security teams get alerts about inappropriate access and risky user behavior, allowing them to respond quickly. By automatically prioritizing alerts, Obsidian helps security teams mitigate alert fatigue by focusing on biggest risks and threats to the organization’s security. Alerts inform security teams and managers in the organization about suspicious activity and abnormal behavior.
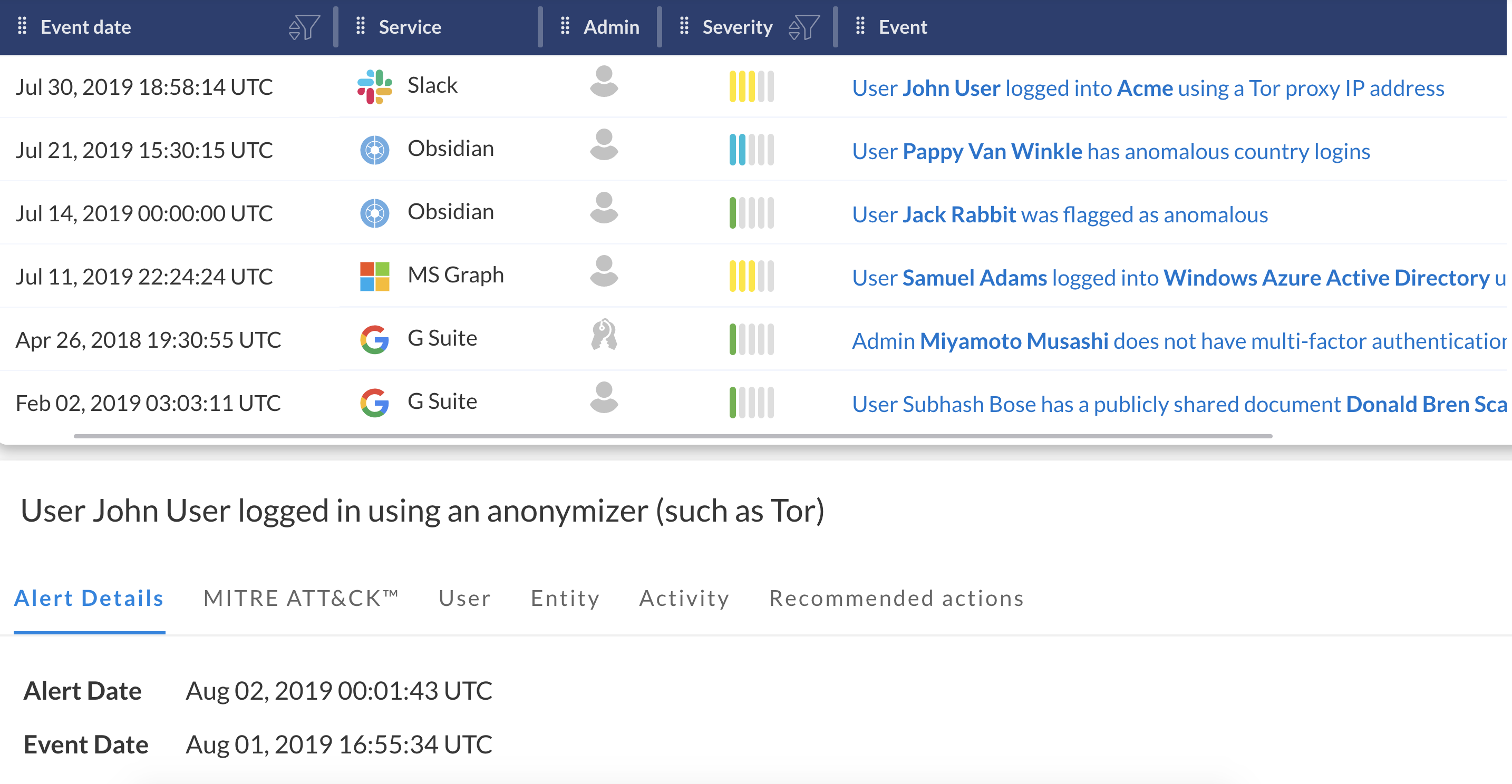
CONSOLIDATED AND PRIORITIZED ALERTS FROM ALL MONITORED APPLICATIONS
Obsidian analyzes and prioritizes alerts to allow administrators to focus on biggest security risks and threats.
Rich built-in alerts
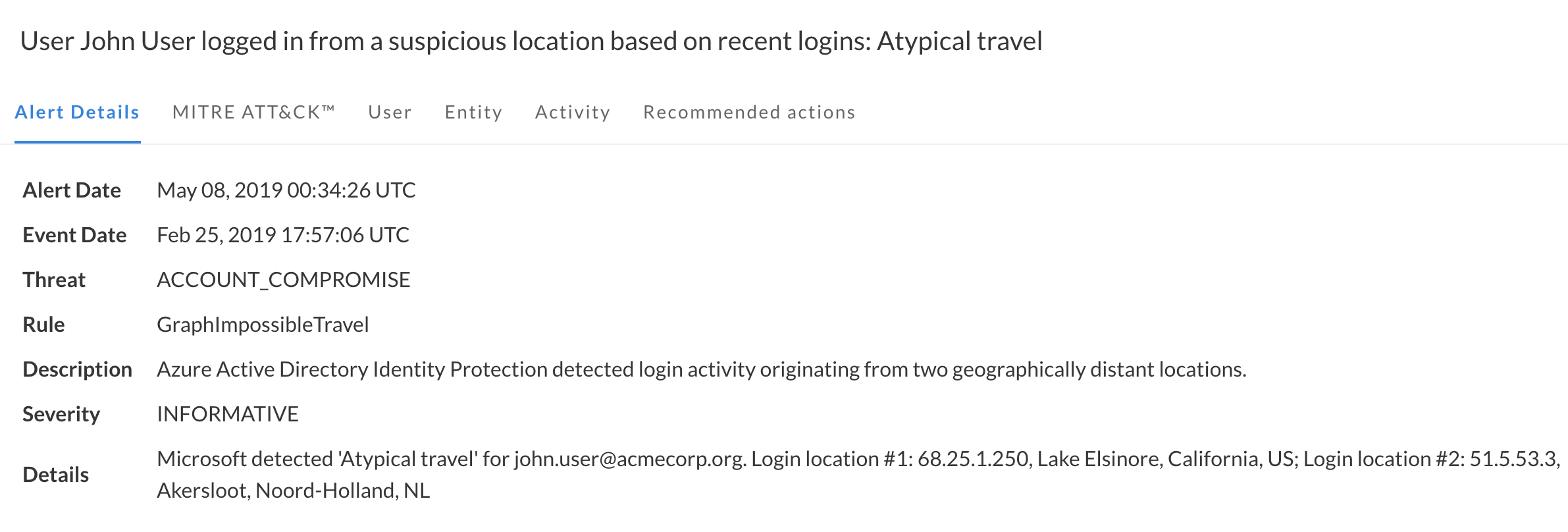
Get alerts on a wide range of threats out of the box without any required configuration. Are employees downloading an unusual amount of data from Salesforce? Sharing key documents with the entire internet? Logging in using a Tor browser? Are you seeing an alarming number of unsuccessful logins on a particular account? How about logins from an unfamiliar geo? Obsidian alerts cover well known malicious posturing and attempted attacks, and are sorted by severity level.
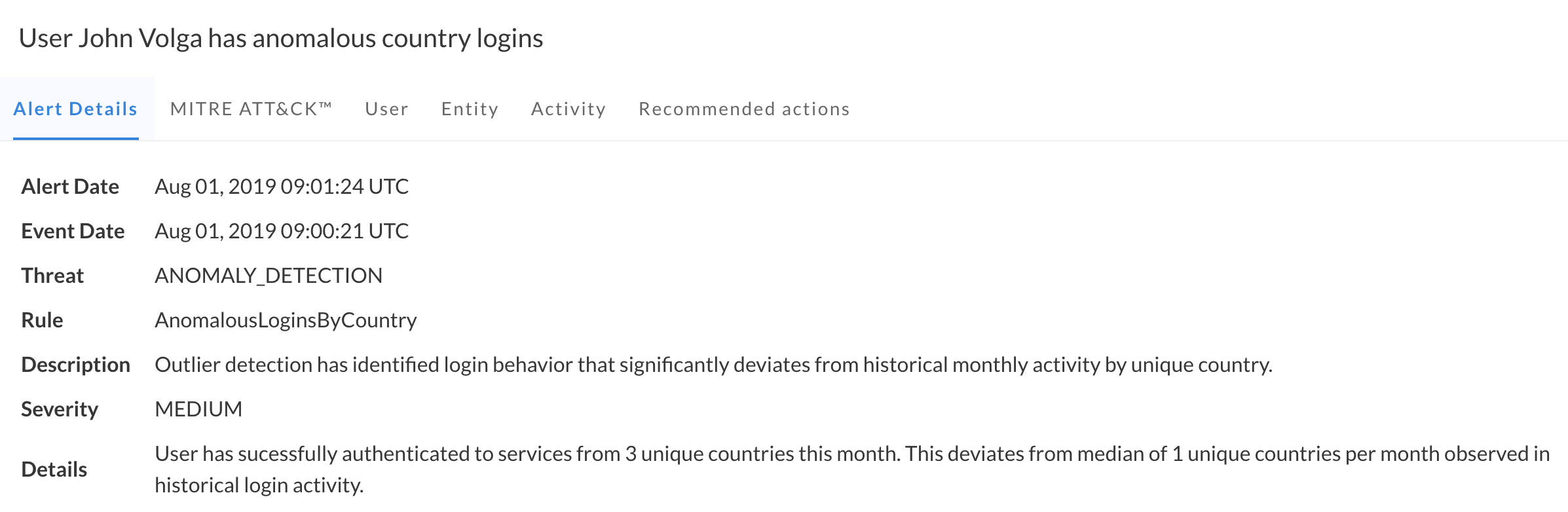
Powerful machine learning and user behavior analytics
In addition to rule-based alerts that check for violations of policies and security best practices, Obsidian implements user behavior analytics at the individual, peer group and organizational level to detect anomalies and flag emerging categories of risky activity. The platform updates its awareness of typical behavior within the organization to offer continuously improving alerts.
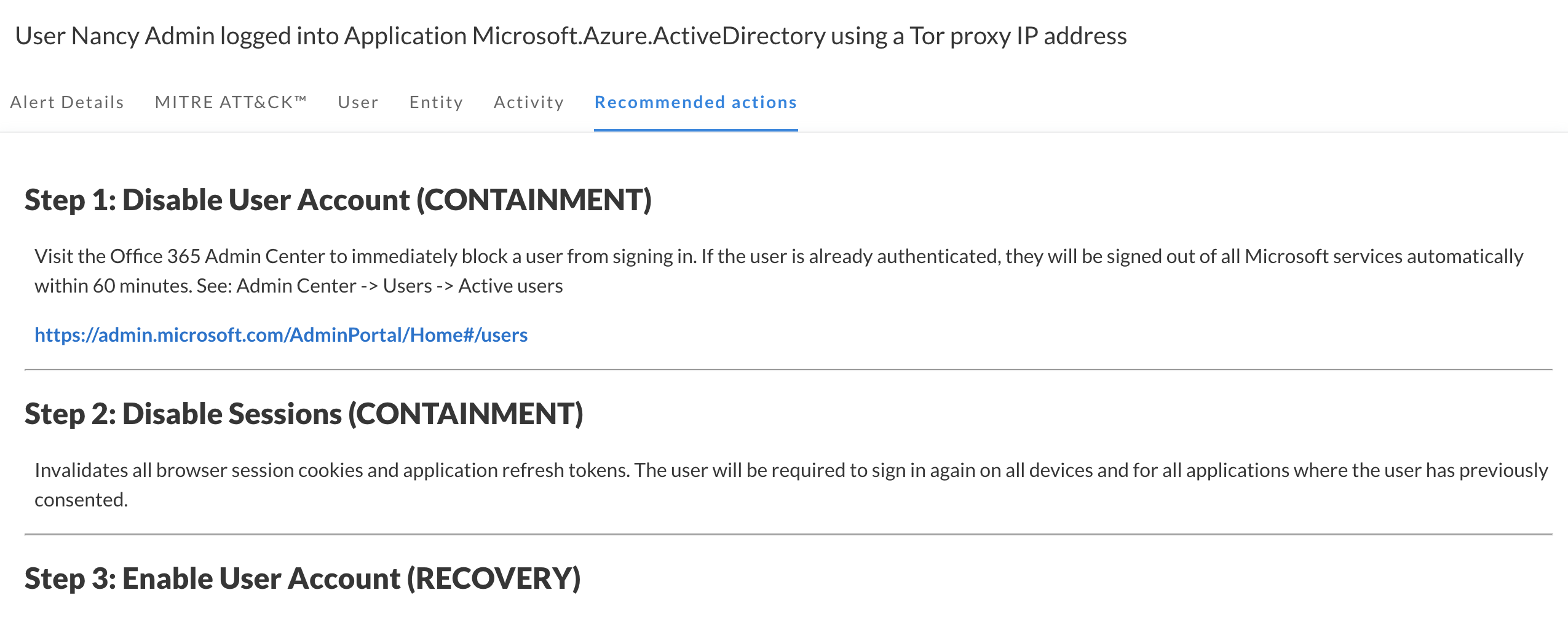
Remediation recommendations
Obsidian offers remediation recommendations in the context of each alert to guide successful response. Security teams can track down the root cause of the issue, understand scope and impact, and export data for further investigation and reporting.