
SaaS Incident Response
Watch to learn how to apply NIST’s four principles of security incident handling to your own SaaS incident response program. This will help your organization detect and respond to SaaS attacks faster and harden its security posture.
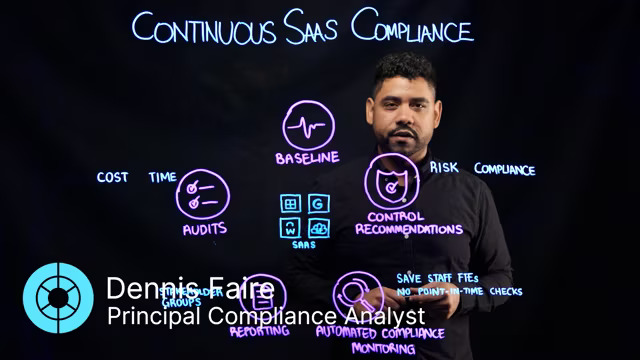
Achieve Continuous SaaS Compliance
Automated SaaS compliance monitoring offers more benefits than the manual kind. It continuously validates whether your SaaS technical controls and settings match your expectations about what they should be without blindspots associated with manual monitoring. On this video, Dennis Faire gives you the details on additional benefits including reduced regulatory audit time and expenses, and improved stakeholder communications.

The Three Pillars of SaaS Security
This video highlights a new way to think of SaaS security recognizing that interactions are no longer just between users and apps. Apps now talk to each other meaning risks and threats can come from anywhere. This is why it is important to think of SaaS security as a tripod combining posture, integration risks, and threats.
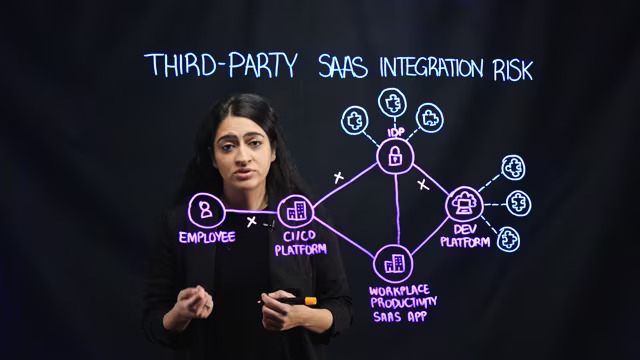
Third-Party SaaS Integration Risk
Do you allow business partners to access your Salesforce or Workday data to deliver services? If so, their security practices could impact your security and regulation compliance status. Risks created via integrations are some of the most virulent security threats to organizations today. Watch to lean more about these risks and an analysis of a high-profile incident.
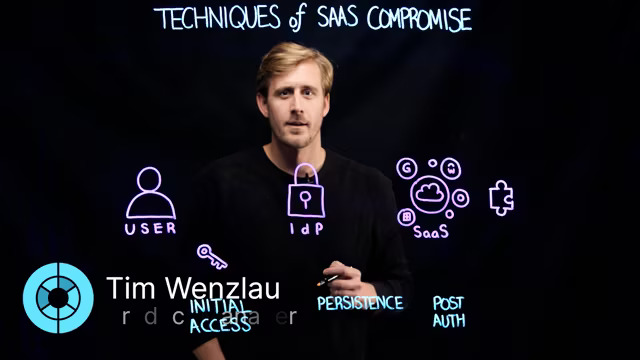
Techniques of SaaS Compromise
Identity providers and common measures like single sign-on and multi-factor authentication have driven attackers to develop and rely on new techniques for SaaS compromise. Learn some of the techniques they’re using to get into your SaaS environment and the persistence measures they’re using to stay there.

The Elements of Comprehensive SaaS Security
To better understand SaaS security today, it is important to recognize why solutions were developed to protect endpoints and cloud infrastructure in the past. Discover how EDR and CSPM emerged to protect against threats to devices and vulnerabilities in cloud infrastructure. Then, hear how Obsidian’s comprehensive approach addresses these components for SaaS.

Breaking Down SaaS Security Posture Management (SSPM)
Security leaders recognize that most of the applications that are critical to their organizations have already transitioned to SaaS. And yet, many security teams struggle to understand the posture of their SaaS environment—and the vulnerabilities that may exist. Learn how SSPM solutions help protect the various components that comprise application posture.

Zero Trust Security for SaaS Applications
Zero trust is the standard for security leaders who recognize the benefits of “never trusting, always verifying” every piece of their environment. While the implementation of this framework around physical and cloud infrastructure is generally understood, zero trust for SaaS stops at the identity provider for most companies. Learn how to extend the tenets of zero trust all the way to the applications that your business relies on most.

Identify and Mitigate SaaS Session Hijacking
The prevalence of multi-factor authentication and single sign-on has caused attackers to forgo targeting credentials in favor of capturing session tokens. Learn about some of the methods bad actors are employing to steal tokens, hijack sessions, and establish persistence within SaaS identity providers and business-critical applications.

Prevent OAuth Abuse in the SaaS Environment
The ability for your applications to connect and communicate with one another is one of the greatest productivity benefits of SaaS. At the same time, authorizing OAuth applications to connect to core SaaS platforms creates a new opportunity for attackers to potentially exploit. Learn about some of the various methods of OAuth abuse and find out how Obsidian can help identify and mitigate these threats.

