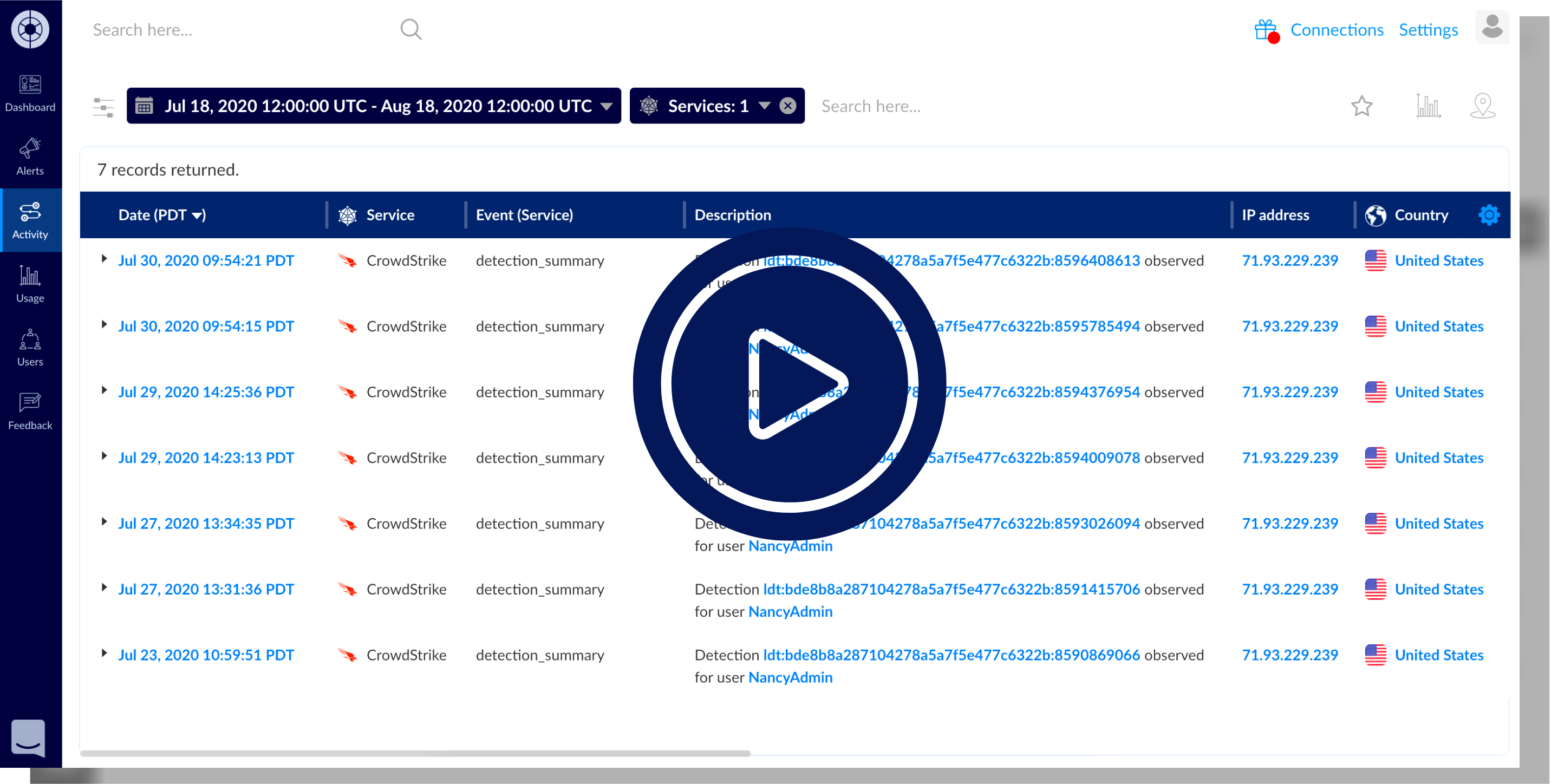
The Last Mile Challenge
With the growing use of SaaS applications for critical business processes and the proliferation of endpoint devices, an organization’s users and data sit outside the traditional network perimeter. Business users access SaaS applications directly from their sanctioned and unsanctioned devices, often bypassing the traditional network. This creates challenges for security teams tasked with protecting the distributed workplace.
Security teams lack consolidated closed-loop visibility into what users have access to and what they are doing in SaaS applications and their endpoints. In order to get better at detecting and investigating threats and breaches, they need to be able to correlate telemetry from endpoints with user activity SaaS applications.
The Solution
Obsidian cloud detection and response (CDR) integrates with the CrowdStrike Falcon platform to deliver frictionless security for SaaS applications and endpoints. This integration helps security teams uncover, investigate and respond to breaches and insider threats quickly, without slowing down business operations.

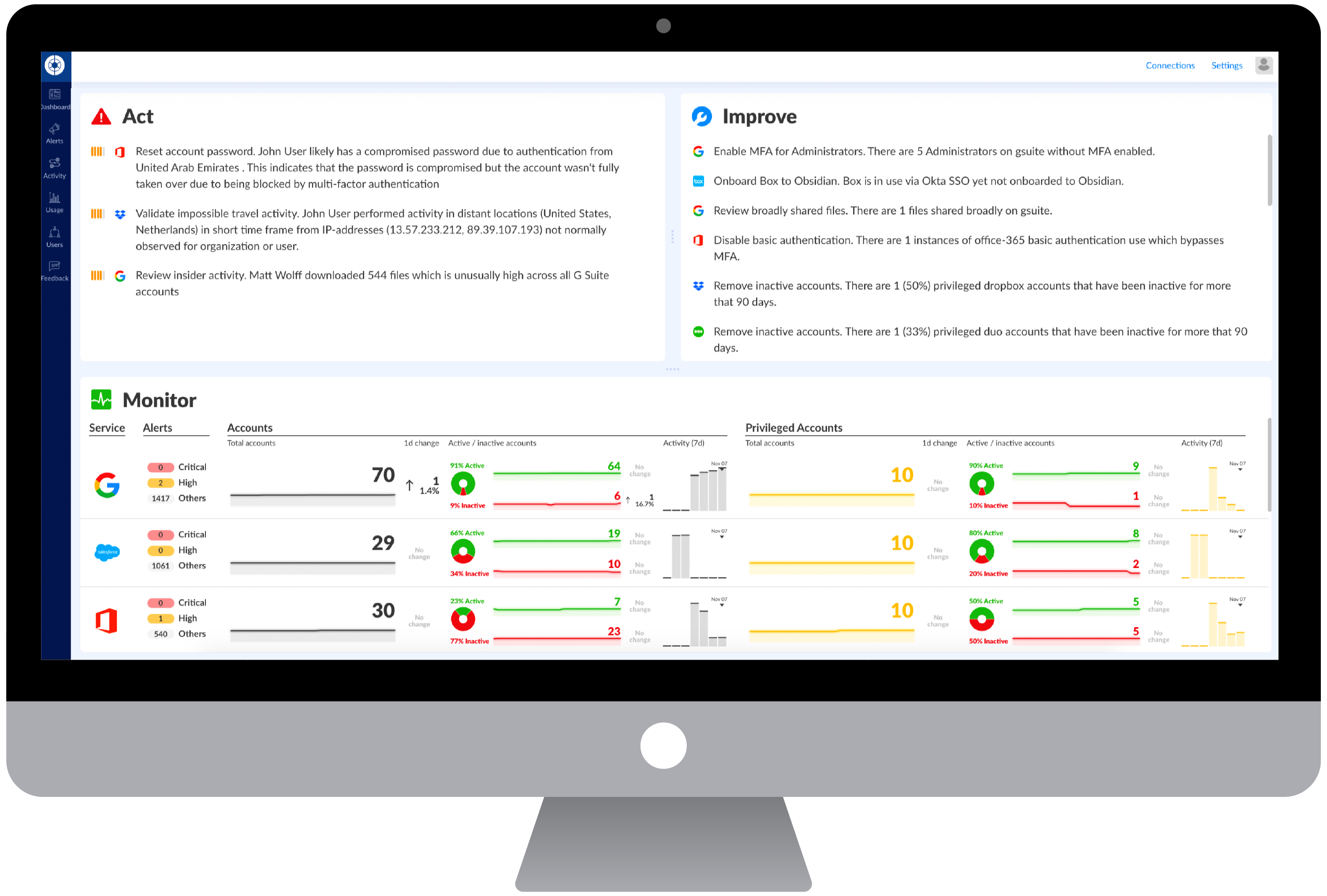
Security teams can seamlessly receive data about user access, privileges and activity in SaaS applications, and correlate that with rich endpoint telemetry from CrowdStrike endpoints for increased visibility and protection.
By combining Obsidian’s SaaS activity data with endpoint telemetry from CrowdStrike Falcon, security teams can answer questions like:
- “This user’s laptop had malware; are her SaaS accounts compromised?”
- “I’m looking at this user’s SaaS accounts during an investigation, what devices does he have?”
- “We see strange logins from a new country for this user, where are the devices for this user?”
Integrating the industry’s first cloud detection and response (CDR) solution from Obsidian with the leading endpoint detection and response (EDR) solution from CrowdStrike delivers seamless visibility across users’ devices and cloud accounts, and enables joint customers to detect, investigate, and remediate attacks.
Benefits

Monitor user activity
Correlate users’ SaaS accounts with their endpoint devices in order to get richer context of user activity.
Harden security with risk monitoring
Identify and mitigate risks and inappropriate activity to improve the organization’s security posture and prevent breaches.

Defend against breaches and threats
Detect and proactively hunt for internal and external threats by discovering suspicious user behavior across SaaS accounts and devices.
Quickly respond to incidents
Investigate and respond to breaches and incidents faster by pivoting to a pre-populated contextual view of user activity and alerts in both systems
Want to learn more?
Dig into these additional resources.
- Check out the blog post about the integration.
- Read the press release from CrowdStrike.
- Schedule a personalized demo with Obsidian to learn more.
- The Obsidian solution is available in the CrowdStrike Store.