SaaS security is messy. Any analyst, architect, or SOC team knows it. When you break down the problem, it’s almost chaos by design.
Start with a single SaaS app. It has hundreds of security settings and controls. With enough time, you can probably get your arms around it. But now multiply that by a thousand – the average number of SaaS apps in the modern enterprise, and you start to see the problem. Every app is different, each with its own security settings, permission structures, naming conventions, and quality of telemetry. Very quickly, the situation becomes infeasible and unsustainable.
Now, layer on thousands of SaaS-to-SaaS integrations, each custom to your specific organizational needs. Add in GenAI tools and AI agents that move data between systems faster than any human can track. Suddenly, what was ‘manageable’ becomes impossible to control and secure.
.png)
It’s not just complexity, it’s connected chaos. These apps don’t sit quietly in isolation. They’re constantly talking to each other. Every integration introduces a new link in the chain, and every link is a potential attack path. AI agents only amplify the problem, creating invisible connections and access patterns that expand the attack surface.
Meanwhile, security teams are being told to do more with less. Protect every new app, every user, every integration, every threat with fewer people and smaller budgets. It’s no wonder burnout, alert fatigue, and blind spots are everywhere.
The path forward begins with tackling three chained problems.
- Closing coverage gaps across an increasingly fractured SaaS ecosystem.
- Turning overwhelming data into context and intelligence.
- Empowering security teams to take action faster than the threats evolve.
This is exactly what our latest platform enhancements are designed to address. Here’s how we’re tackling each one.
The Fragmentation Problem: Too Many Apps, Not Enough Coverage
Most security tools promise coverage for the crown jewels like Salesforce, Workday, ServiceNow, Google Workspace and a handful of others. And yet, these are the very apps that some of the most sophisticated attackers continue to breach.
Now, think about the long tail of SaaS. Thousands of lesser-known applications that don’t have prebuilt connectors, or weren’t designed with security telemetry in mind. Each one integrates with others, forming complex SaaS-to-SaaS chains across the enterprise. It only takes one weak link in that chain – one poorly secured app, one over-permissioned token – to turn into a full-blown breach path.
Your SaaS estate is only as strong as its weakest link.
[[ai-era-cta1]]
When it comes to coverage, there are two problems holding the industry back:
- Not enough connectors: With over 30,000 SaaS applications in the market, there is no single security vendor that can realistically close that gap alone.
- No security telemetry: Many SaaS vendors themselves don’t expose the telemetry, posture data, or security controls needed to properly monitor or defend their platforms. Even if every app had an API, most of them weren’t built with security visibility in mind. That means even the best security teams are left blind in key areas.
The fix isn’t for one company to build everything, it’s for the community - customers, partners and SaaS vendors - to build together.
At Obsidian, we’re tackling this head-on with a two-pronged approach.
First, we’re launching the Community SDK and Connectors, a framework that democratizes integration development. This empowers customers, partners, and SaaS vendors to build and share their own connectors directly into Obsidian. We’ll support this community every step of the way, with tools to build, test, and verify integrations following industry best practices, so teams can achieve full coverage, faster.
Second, we’re pulling together a working group of security leaders to drive vendor alignment and raise the bar for shared SaaS security standards. Frameworks like the SSCF are a great start but lasting change will take collective action from customers, partners, and vendors alike. Our goal is to create a baseline expectation for every SaaS provider, so consistent, reliable security becomes the norm, not the exception.
[[ai-era-cta2]]
Once we’ve built a foundation that truly spans the breadth of SaaS deployment, the next step is turning the data into context and intelligence.
The Intelligence Problem: Too Much Data, Not Enough Insight
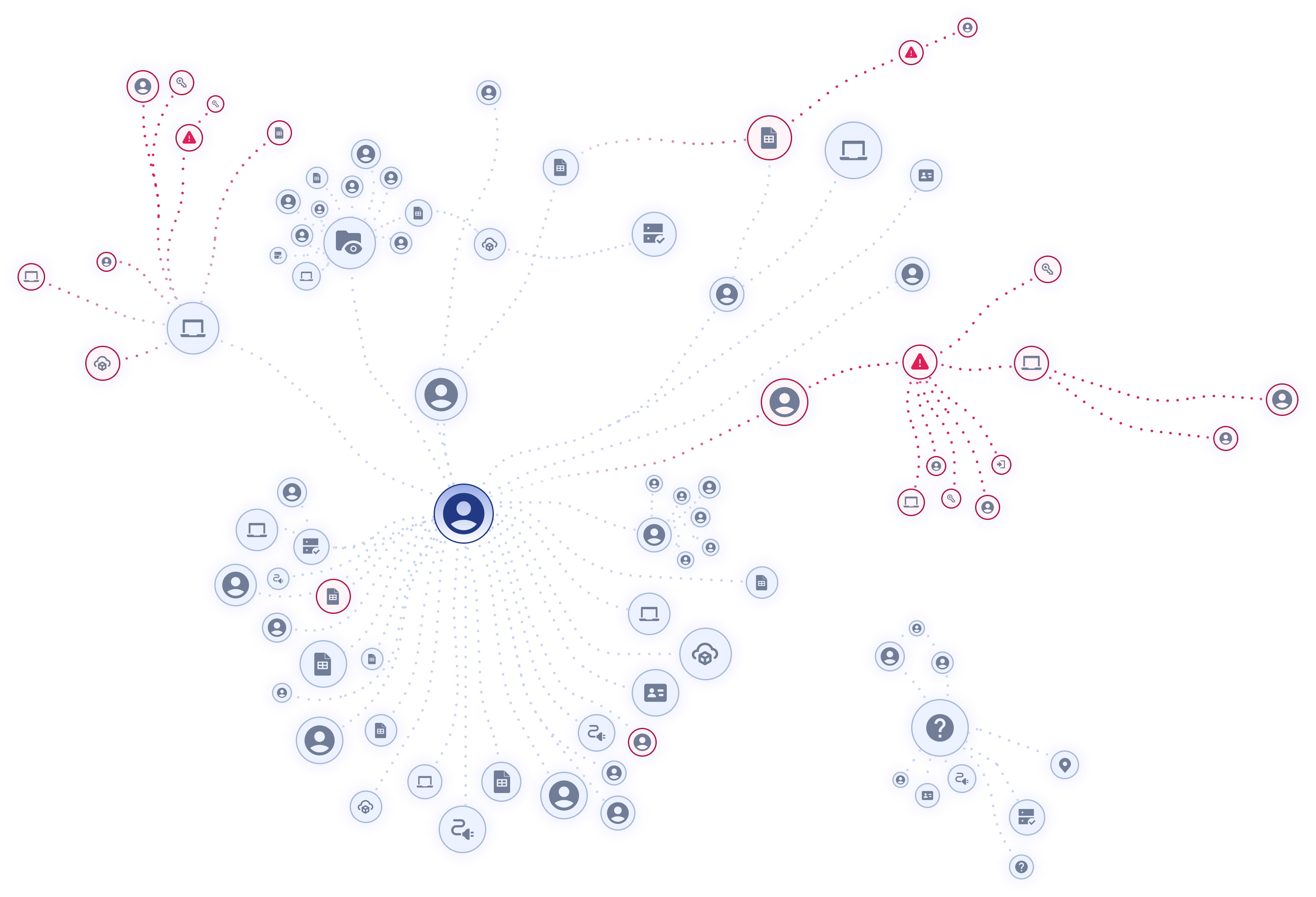
Once you have coverage across your SaaS environment, the next challenge is making sense of it all. Answering the tough questions on who has access to what, how it was granted, where the access spreads. These can’t be answered by simply looking at logs or spreadsheets, as SaaS ecosystems are built around people, permissions and connections that cross products, tenants and identity systems.
That’s why we built the Obsidian Knowledge Graph, purpose-built for SaaS from day one.
Our Knowledge Graph models people, human and non-human accounts, entitlements, tokens, and the relationships between them. We start with identity and activity – two essentials of any security story: who someone (or something) is and what they did inside the app. This is enriched with behavioral baselines learned from real SaaS incidents to teach the system what ‘normal’ looks like across users, roles and applications. Add SaaS state, i.e. configuration data, permissions and ownership, to uncover hidden overlaps and privilege creep and for clear evidence paths to fix them. Non-human identities like service accounts, API keys, OAuth clients, and AI agents are tracked just like people, linking them to their origin, scope and actions, revealing when automation drifts off course. And when APIs fall short, client-side browser telemetry fills the gap, exposing authentication shifts, shadow SaaS and rogue AI use.
A built-in feedback loop lets users mark alerts as true or false positives, making the graph smarter over time.

The result: a unified, time-aware model that connects SaaS identities, accounts, permissions, tokens, integrations, and activity into one living, intelligent system of record that turns fragmented SaaS data into context that’s instantly understandable. This depth lets security teams move from static visibility to true understanding, from tracing exposure paths, uncovering risky access patterns, and accelerating investigations with confidence.
[[ai-era-cta3]]
The Resource Problem: Too Many Threats, Not Enough Hands
Security teams are stretched thin: the global cybersecurity workforce gap reaches almost five million people, and the majority of orgs report a staffing shortage. At the same time, many teams face budget cuts, layoffs, and even hiring freezes. That scarcity compounds another reality: over half of practitioners say they don’t have time to learn new skills, so the barrier to upskilling stays high while the SaaS attack surface keeps growing.
We’ve spoken to countless security professionals who can count their team members on two hands. Yet they’re outnumbered across their own organization by employees in every department deploying new SaaS apps daily, approving new integrations, and granting risky permissions in the name of business productivity. The environment changes faster than security can keep up. Alert volume spikes, attack surfaces multiply, and teams are pushed deeper into reactive mode.
We’ve reached an inflection point. Security teams need the automation and productivity boost AI can provide, but it has to come with trust, governance, and explainability. Without those guardrails, automation can add risk instead of reducing it. With them, it can finally help teams scale their impact, amplifying human judgment, speeding investigations, and freeing talent to focus where it matters most.
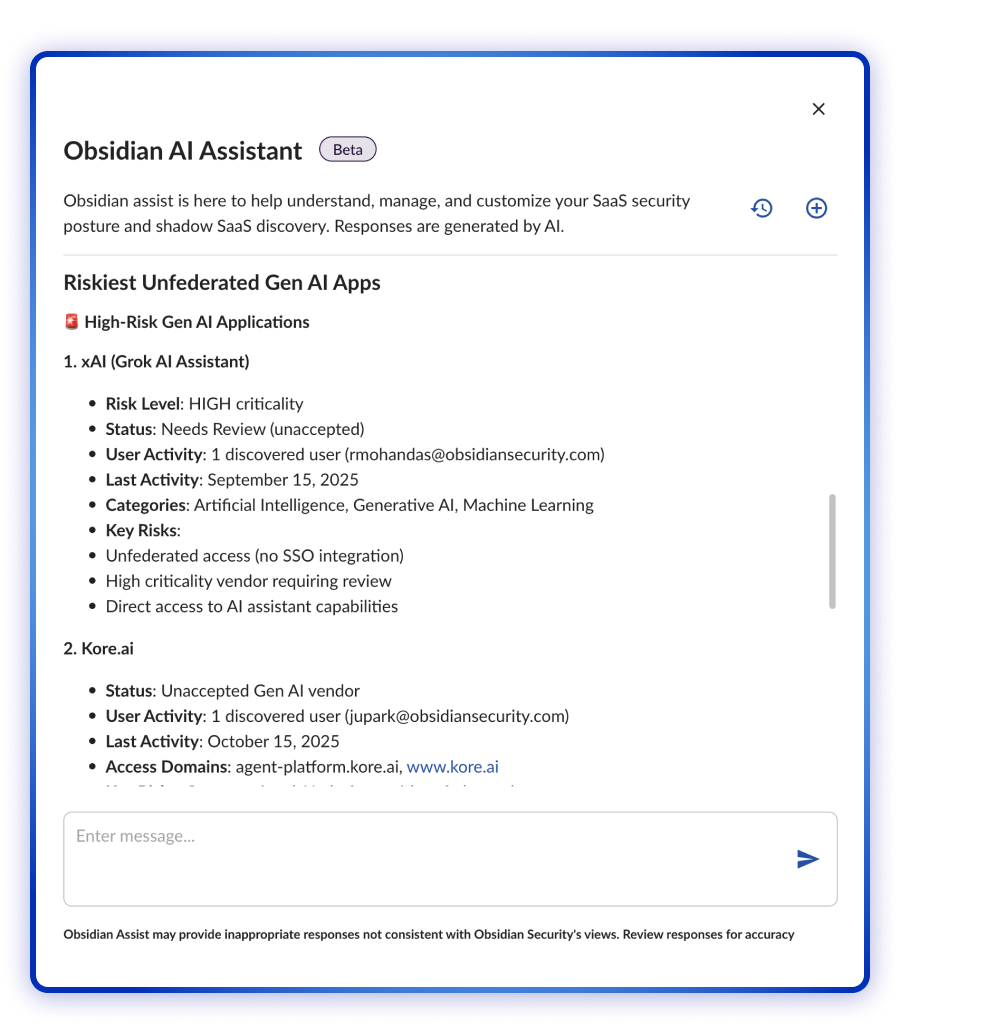
That’s where Obsidian AI Assistant comes in. Imagine an AI-powered partner built specifically for SaaS security, one that understands context, prioritizes intelligently, and takes on the repetitive, time-consuming investigation analysts shouldn’t be spending time on. It not only flags issues, but helps interpret, explain, and act on them.
AI Assistant isn’t about replacing people. It’s about amplifying what they can do and giving every security, no matter the size, the reach and speed to match the scale of modern SaaS. And while there’s much more to say about what that looks like in practice, one thing is clear: this is the next chapter of SaaS security, where human expertise meets intelligent automation to do more, with less.
[[ai-era-cta4]]
What’s Next?
Security has always been a discipline of reinvention and adaptation. Every few years, familiar principles, like least privilege or complete visibility, return in new forms, reshaped by the technology and threats of the moment. SaaS changed the surface area. AI is super-charging the speed. Together, we need to redefine what it means to protect the enterprise.
At Obsidian, we see this moment as a reset. It’s the point where security moves beyond point solutions and manual effort, toward something faster, smarter, and more connected. Where coverage grows as fast as the ecosystem, context turns raw data into understanding, and intelligent assistance gives every team the reach to match the scale of modern SaaS.
We’re building a future where SaaS security scales naturally alongside the technology it protects, and we’re doing it in partnership with the border security and SaaS community. And we’ve engineered a platform from the ground up to advance SaaS defense and tackle the AI-driven threat landscape.
[[ai-era-cta5]]




