How do you get a handle on identity sprawl and account bloat when over 20% of your users churn every year? This is the story of one law firm that found an effective way to bring order to its account population with continuous visibility and monitoring from Obsidian.
Situation
A highly-ranked mid-sized law firm in the US specializing in corporate and commercial law runs a rigorous year-round associate program. Every Fall, 80 new associates join the firm’s 300 full-time employees, and associates already in the program either continue or leave.
The law firm adopts a cloud-first approach to IT, using SaaS applications for email, document sharing and collaboration. During their tenure, associates are given access to sensitive information to conduct due diligence and research, and prepare court memos.
Without a systematic approach to onboarding and offboarding associates, the firm faced an ever-growing number of digital accounts that not only added to operating expenses but, more importantly, expanded their security perimeter.
An annual access review found unused accounts with access to sensitive information, belonging to 120 associates who left the program in the last two years. This was a growing concern for the IT team and the firm’s leadership.
The IT operations team was tasked with creating a formal identity lifecycle management process to onboard and offboard employees and perform regular access reviews to catch identity sprawl. The team also needed to implement the principle of least privilege by ensuring that every employee and associate was given just the privileges required to do their work, and that privileges were revoked when no longer needed.
Hand in hand, the security team was looking for a solution that would offer:
- Full visibility into user accounts, access, and privileges in the cloud services
- Ability to identify stale accounts and unused privileges, and clean them up with confidence
- Consolidated view of activity that could be used to investigate incidents or check compliance with policy
Hello, Full Visibility
To solve their ongoing visibility and posture management challenges, the firm brought on Obsidian. The security and IT teams were able to onboard their G Suite, Office 365, Salesforce, Slack and Duo accounts in under half an hour. The security team was surprised to discover that a quarter of their associate population was inactive. Worse, they saw that more than 50 associates had been granted access they didn’t need. The security team got to work.
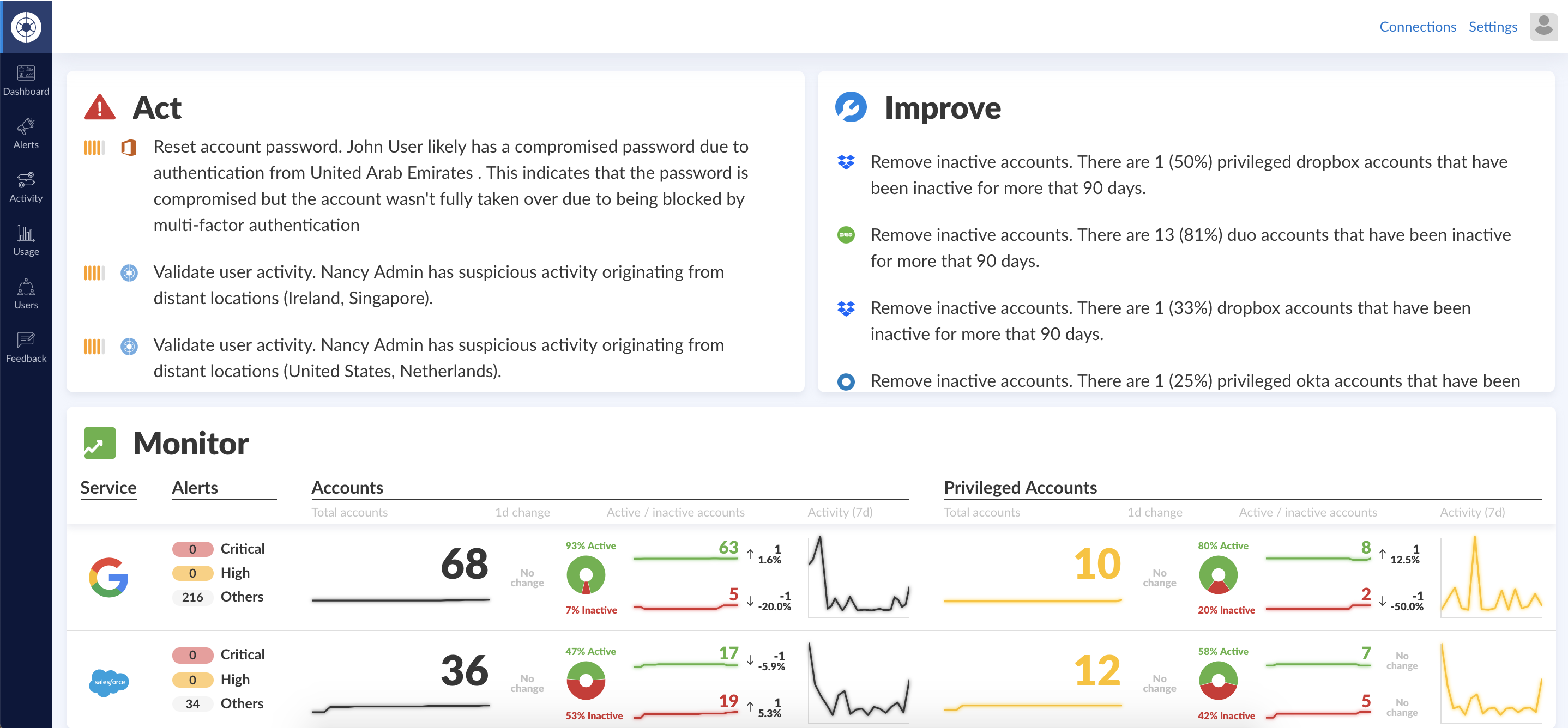
Access Reviews
Using Obsidian, the security team was able to systematically review user accounts and privileges across all the cloud services in one place. By establishing a period access review process, security was able ensure identity hygiene.
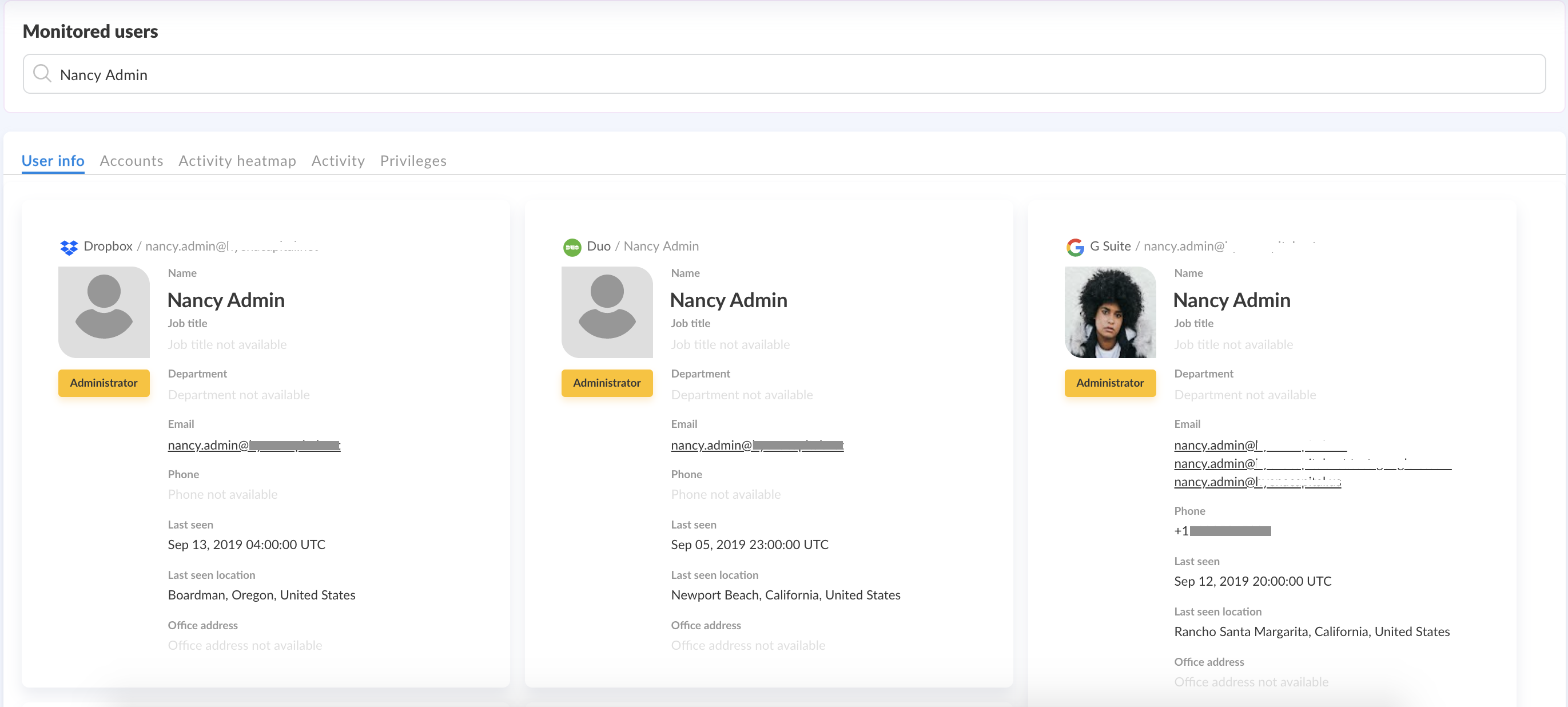
In one access review, the security team found out that 5 current associates were accidentally granted privileged access to data that they didn’t need to perform their tasks. In another instance, an HR law associate inappropriately accessed criminal law cases after-hours using excessive privileges, so security restricted her access rights to folders pertinent to her job.
Access and Privilege Right Sizing
The security team used the service usage filter to identity accounts that were inactive over the last 90 days in different services. They exported this list and worked with IT to de-provision to inactive accounts with confidence.
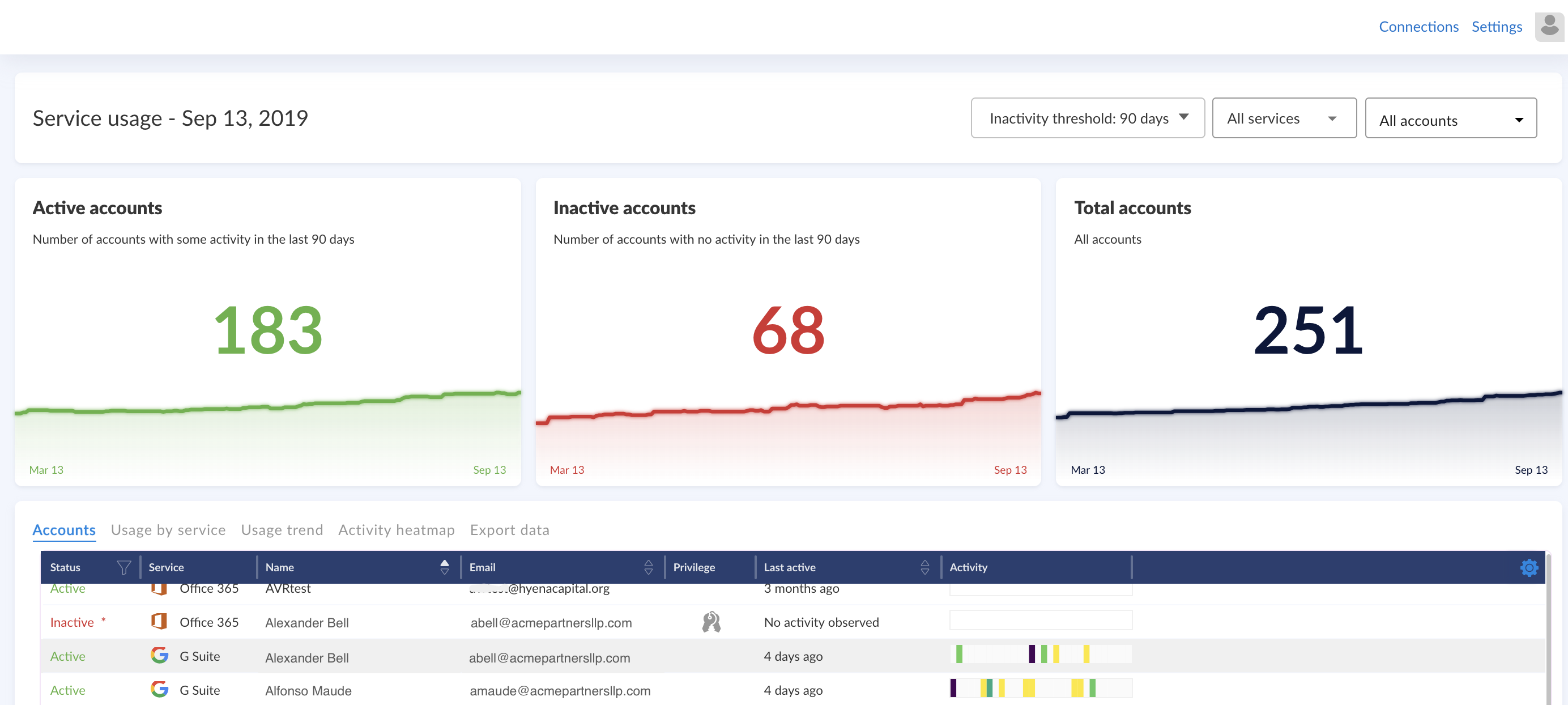
Consolidated Activity Stream
By rewinding and replaying the entire course of the HR law associate’s time at the firm, they identified the manager who gave her elevated privileges, and did a deep dive into the associate’s activity. The HR law associate’s history showed regular logins at odd hours. During these times, she also exercised her elevated privileges to download volumes of criminal law cases unrelated to her daily work.
When the security team followed up with the associate via email, she admitted to being interested in unresolved criminal cases and had downloaded the cases to read after-hours. Though embarrassed by her curiosity as a subject of serious investigation, the associate was grateful for the stern warning against putting the firm’s sensitive documents at risk.
Bye Bye Bloat!
Today, the firm’s security team uses full visibility provided by Obsidian to generate access reviews, ensure excellent identity posture management and conduct activity monitoring.
If you’d like to learn more about how Obsidian can help you get full visibility into what users are doing in your cloud services, you can schedule a demo with the Obsidian team.