

Stop AI agents before they turn your SaaS supply chain into a data exfiltration pipeline with real-time visibility and security controls.
















One compromised integration gives attackers instant lateral movement to sensitive data across countless businesses. Your SaaS supply chain has become the new frontline.
To stay in control, security teams have to know:
The problem? Traditional security tools can’t answer those questions.
The security game has shifted in-app where AI agents operate. But most security platforms are still focused only on controls to-app, stopping at the perimeter instead of protecting what’s happening inside.
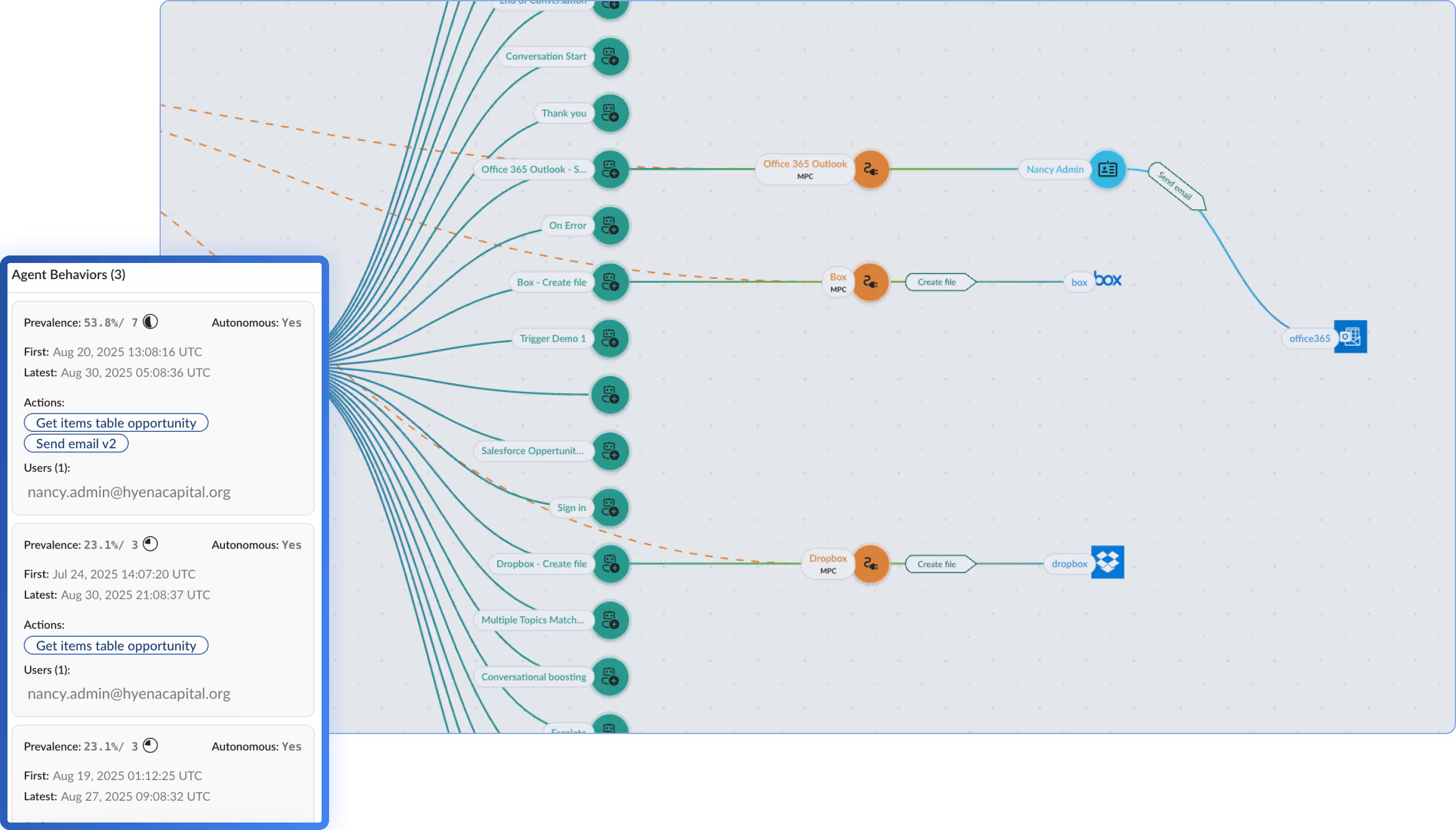

Guide
AI agents often hold excessive privileges, creating major governance and compliance risks. This guide helps security leaders detect shadow agents, enforce guardrails, and prevent privilege sprawl with clear steps and unified visibility.

Blog
Supply chain attacks that exploit unmonitored SaaS-to-SaaS integrations affect ten times more companies than traditional credential-based breaches.

On-Demand Webinar
Explore key insights and strategies from CISO experts on how to take control of AI within your organization—secure GenAI usage, monitor extensions and integrations, and safeguard sensitive data with visibility and browser-level controls.