

Don’t leave your business exposed. Protect your critical data and workflows before attackers exploit SaaS and AI integrations to break in.
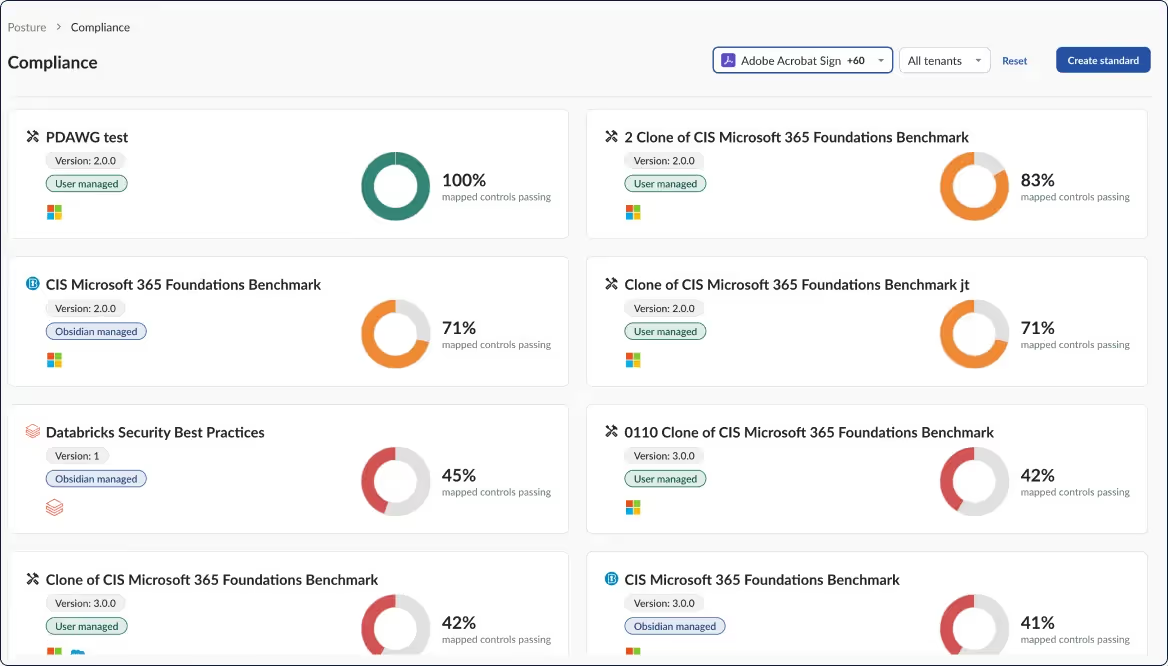
Track progress for external and custom frameworks. Detect compliance gaps to align with regulatory requirements within minutes. Get recommended actions to meet any standard.
Surface privileged accounts across services causing the most risk (e.g. admins without MFA enabled). Get recommendations to reduce over-privilege. Revoke dormant accounts and unnecessary access permissions.
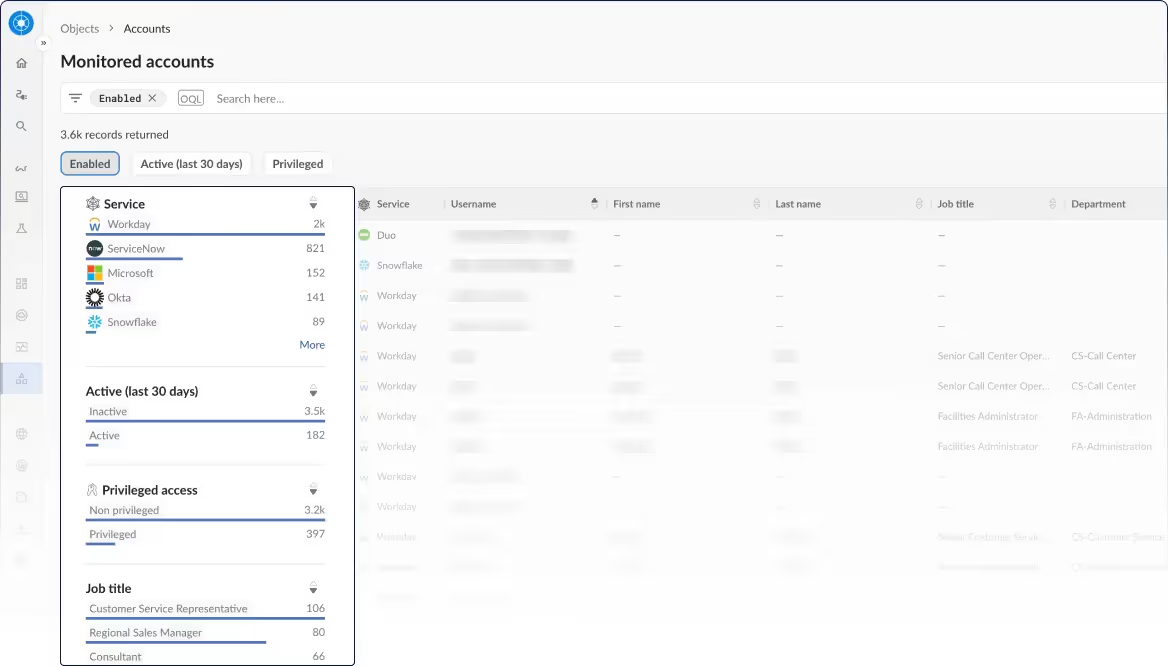

Expose shadow SaaS in your supply chain and reduce your attack surface with full discovery, visibility, and governance.
Find, score, and approve every SaaS and AI integration. Remove inactive connections and manage changes to reduce risk.
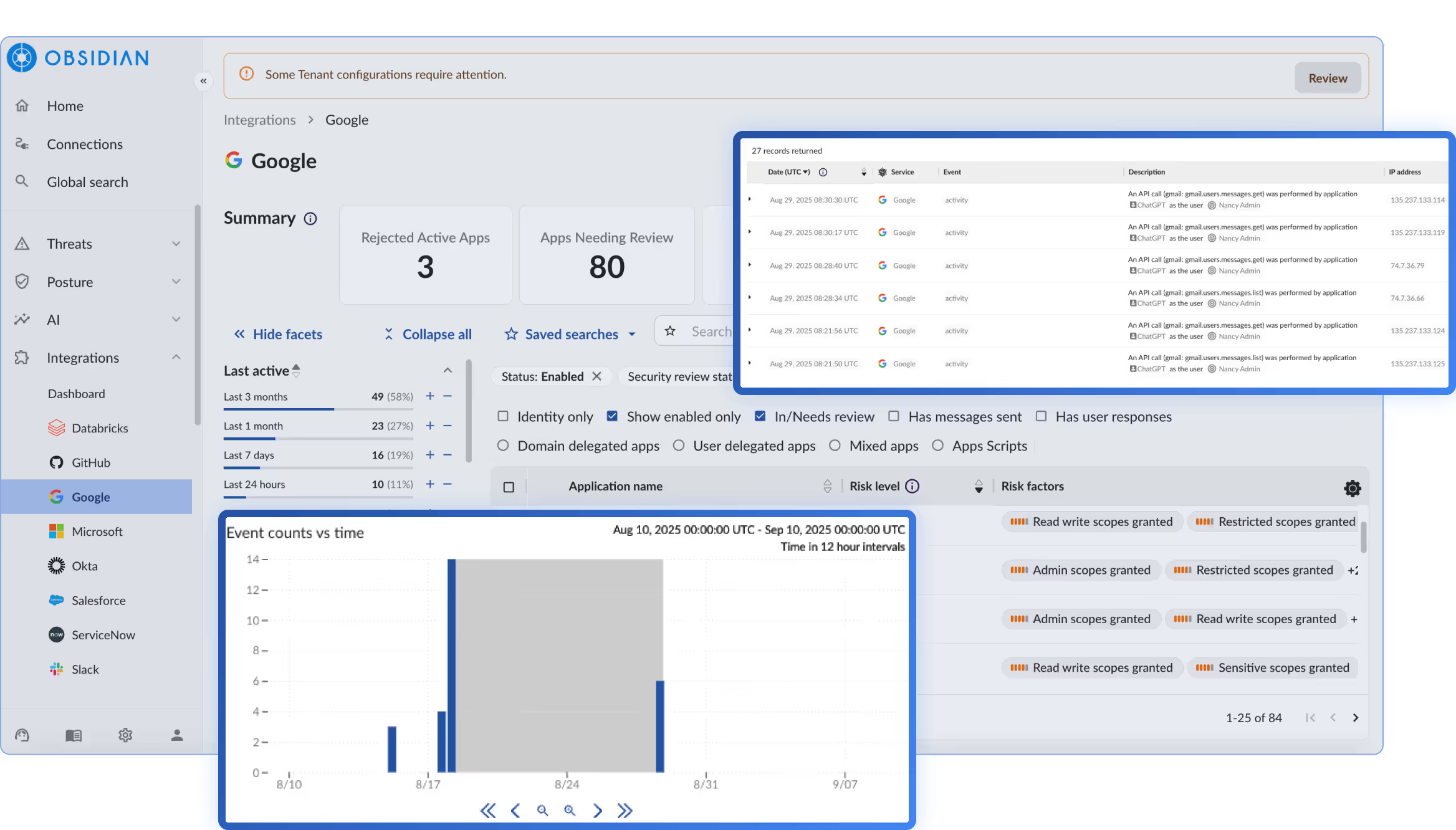












Obsidian Security helps organizations detect and minimize GenAI risks, enabling safe and responsible use across the business.
