

Get the guardrails, intelligence and real-time defenses your SaaS security needs, whether the risk comes from humans, connected apps or AI agents.















The Salesloft breach. Midnight Blizzard. ShinyHunters... These hits aren’t isolated events. They’re a clear attack pattern on SaaS.
SaaS is the attacker’s new playground – stolen tokens, excessive access rights, hijacked accounts, unsafe configs – each one capable of triggering cascading breaches.
Now layer in AI agents that make decisions, trigger workflows, and access sensitive SaaS data at machine speed, without any human oversight. They’re fast, efficient and productive. And they’re a security ticking time bomb.

Humans, GenAI chatbots, shadow integrations, AI agents – if it touches your SaaS, Obsidian’s on it. If it’s connected, we see it. If it’s risky, we flag it. If it’s malicious, we stop it.
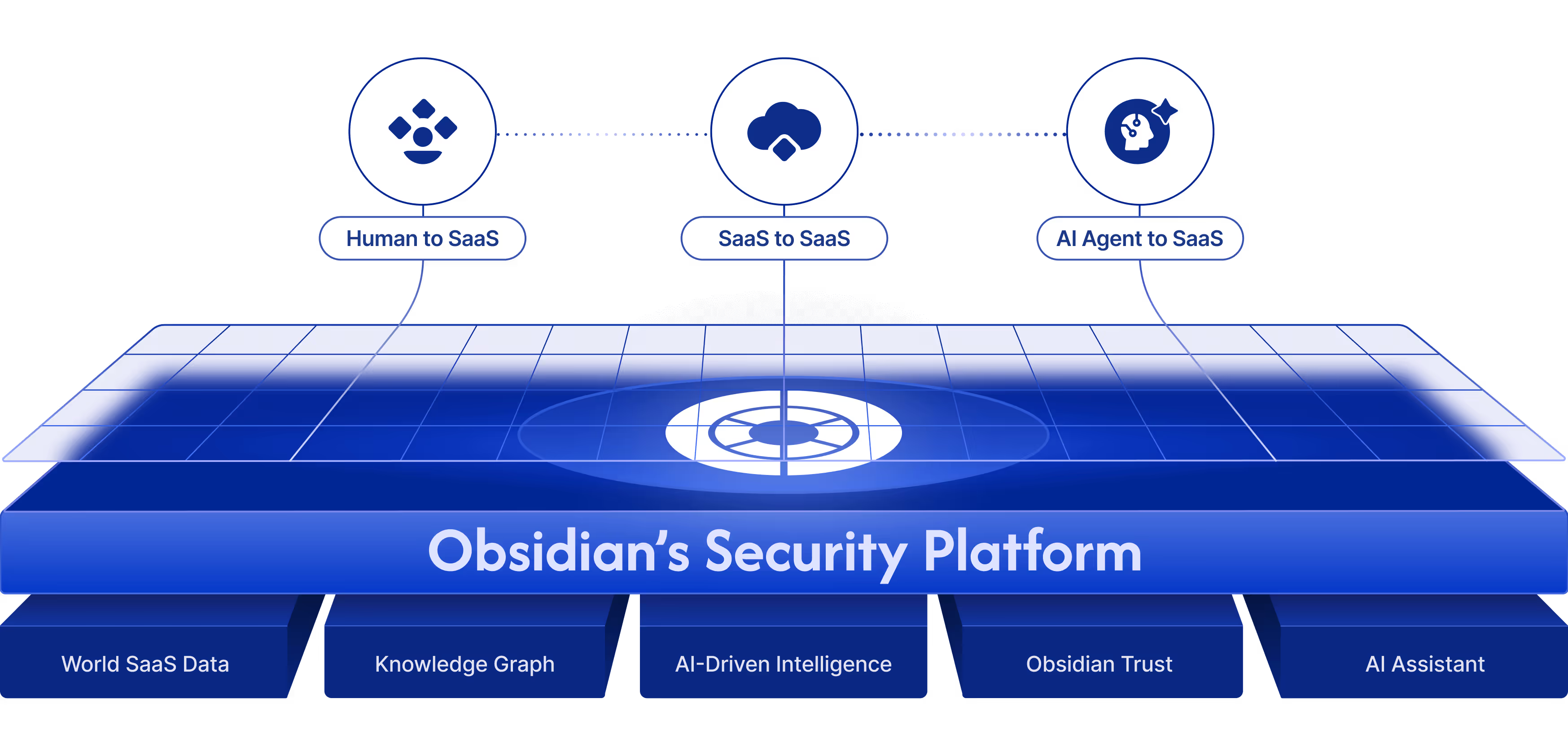
We capture real-time user and agent activity, maintain the largest SaaS breach intel, and integrate rich in-app config and activity data that others simply don’t have.
Our continuous self-learning model gets smarter with every signal and live customer threats, sharpening detection and surfacing SaaS risks as they happen.
Track and analyze the state and activity of users, apps and integrations by retaining history and correlating it with threats to expose real risks that stateless tools miss.
Unified, normalized, and contextual – mapping identities, access, activities and risks for a live map of your SaaS estate, so nothing slips through the cracks.
Harden SaaS configs, eliminate drift, and enforce best practices before misconfigurations become breaches.
Detect SaaS threats as they happen, shut them down fast, and keep constant watch to prevent escalation.
Keep AI in check by controlling SaaS-connected apps and agents, stopping data leaks and risky autonomous activity before they spread.
From privilege sprawl to supply chain breaches, shadow AI to prompt security, see how Obsidian stops the attack patterns shaping today’s SaaS threats.
See and control autonomous agents triggering actions
Detect unapproved AI tools before they expose sensitive data
See and control autonomous agents triggering actions
Enforce least privilege and monitor elevated access
Secure AI prompts
and prevent prompt injection attacks
Detect and shut down token abuse in minutes before data is stolen
Stop token theft, malicious integrations, and cascading breaches
Prevent data exfiltration
via GenAI apps and browser extensions
Protect credentials from AI-powered phishing and browser-based attacks
Excessive privilege accounts reduced
Decrease in SaaS attack surface
Next-gen phishing attacks defeated
Faster investigations with IOC correlation in minutes
Faster remediation by blocking risky tokens
Better alert fidelity with 80%+ true positive accuracy

Anyone or anything that touches or acts inside your SaaS, we surface it so you stay in control.

Spot and harden risky drift and unsafe integrations to keep SaaS secure, compliant and resilient.
%201.svg)
Continuously monitor for malicious or risky activity, catching issues the moment they unfold.
%201.svg)
Stop threats before they spread and streamline response with built-in ITSM, SIEM and SOAR integrations.



