What is Cloud Detection and Response?
Cloud detection and response (CDR) is a new approach to cloud security that enables security teams to defend cloud applications and infrastructure from account compromise, insider threat, and access misuse. Cloud detection and response delivers consolidated visibility and data-driven analytics to detect, investigate, and mitigate threats in the cloud.
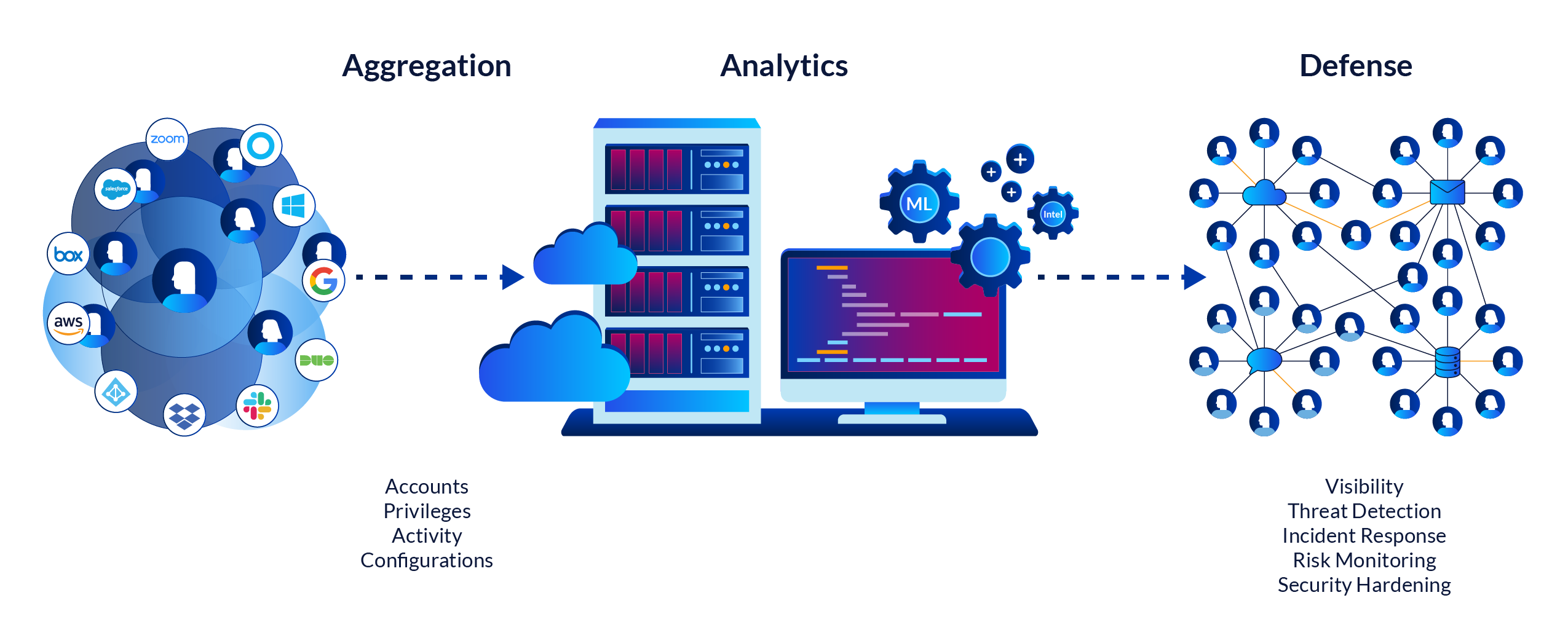
Cloud detection and response solutions continuously aggregate, normalize and analyze large volumes of data about accounts, privileges, configurations, and activity from SaaS and cloud services to provide insights, situational visibility, and alerts around risks and threats.
Existing cloud security solutions such as Cloud Access Security Brokers (CASBs) adopt a perimeter gateway approach to cloud security. CASBs work by trying to sit in the critical path of all point-to-point communication between users’ devices and cloud services. Not only does this approach not work, but you end up with a brittle architecture of forward proxies, reverse proxies, and agents that is operationally heavy to deploy and maintain.
Even with such a solution in place, attackers can still penetrate defenses and gain access to cloud assets. This is because attackers are successfully masquerading as users and service accounts, utilizing legitimate access to resources in the cloud services through a variety of techniques such as credential stuffing, social engineering, spear phishing and brute force password guessing. Account compromise and insider threat are on the rise, yet the data needed for security professionals to hunt and investigate these attacks breaks down as the attacker, and company data, move from the endpoint to the cloud.
Cloud detection and response solutions focus on providing continuous, consolidated visibility of users, privileges, and activity across cloud applications and services. Security teams are able to see which users have accounts in each application, which accounts have privileges, and what users and service accounts are doing in the applications. They have this visibility consistently across all their applications and services and all in one place.
Security teams can mitigate identity risk early, as well as detect, investigate and respond to threats such as account compromise and malicious insider activity. CDRs continuously collect, record, normalize and enrich data about service configurations, accounts, privileges, and activity from SaaS, PaaS and IaaS cloud services. CDRs bring a new capability to the cloud security stack.
Security professionals, threat hunters, and security operations center (SOC) teams can use the consolidated activity stream to uncover access patterns that reveal new threats or indicate compromise. In addition, CDRs also have machine learning-powered analytics to automate detection of anomalous or dangerous activity and to uncover misconfigurations and identity risk. Going beyond prevention, these Cloud detection and response capabilities help security teams of all sizes identify threats and investigate incidents preemptively.
Cloud Detection and Response Capabilities
Consolidated Visibility
CDRs provide continuous and consolidated visibility into who has access to what in the different cloud services, and what users are doing across these services. This allows security teams to detect risks and threats, proactive hunt for emerging security issues, and to investigate and respond to incidents quickly. CDRs connect to hundreds of APIs to aggregate data about accounts, privileges, and activity across SaaS and cloud services. They normalize this data, resolve accounts to identities, and enrich the data with threat intel and context (locations, devices, browsers, etc.)

Automated Detections Built on Analytics and Machine Learning
CDRs analyze vast amounts of data across different cloud services to identify patterns that signal risk and threats. The problem with modern cloud environments is that threats are drowned in a sea of irrelevance. By alerting on policy violations and risky behavior informed by machine learning analytics and rules, CDRs help SOCs distill the signal from the noise so they can prioritize their efforts.
Risk Monitoring and Protection
Best-in-class CDRs go beyond detection capabilities to identify signs of a weak security posture, such as unused and stale privileges and poorly configured services. With these insights, security administrators are able to continuously enforce a robust security posture and preempt attacks from happening.