Coding is an art. Its form and function are intertwined. Stacked in simple and neat lines, code can address the world’s greatest challenges and create opportunities we never thought possible.
Before immersing myself in the security world, I ran art galleries on both coasts; New York and Laguna Beach. Besides the commercial aspect of art, I enjoy the act of creating. My drawings, designs and paintings take inspiration from painters like Christopher Wool, Barbara Krueger, Sam Francis, Jackson Pollock and graphic designer David Carson.
At Obsidian, I see parallels between my craft and what our engineers do everyday. The lines of code on their monitors may be to enrich the data of an organization’s user population but, to me, I see the stippled brushstrokes of an impressionist painter.
I have brought together my passion for art and my career in cybersecurity to create a series of prints that focus on the beauty of code. Each piece blends my love for watercolor, my background in graphic design, and my admiration for the power of code.
1. Code Red
The first in the series is “Code Red,” which is a homage to Ryan Permeh, the co-founder and chief scientist at Cylance Inc. I had the honor of working with Ryan while I supported Cylance’s executive team from 2015-2017. He is a leader that has as much dedication to his team as passion for the products he creates. In 2001 when he served as the Founding Software Engineer at eEye, Ryan and co-founder Marc Maiffret discovered a worm that was targeting the US Gov and multinational corporations. While the worm was unable to penetrate the White House, major corporations lost billions of dollars in damages. They named the worm “Code Red” because they were drinking Code Red Mountain Dew at the time they confirmed the worm was a threat.

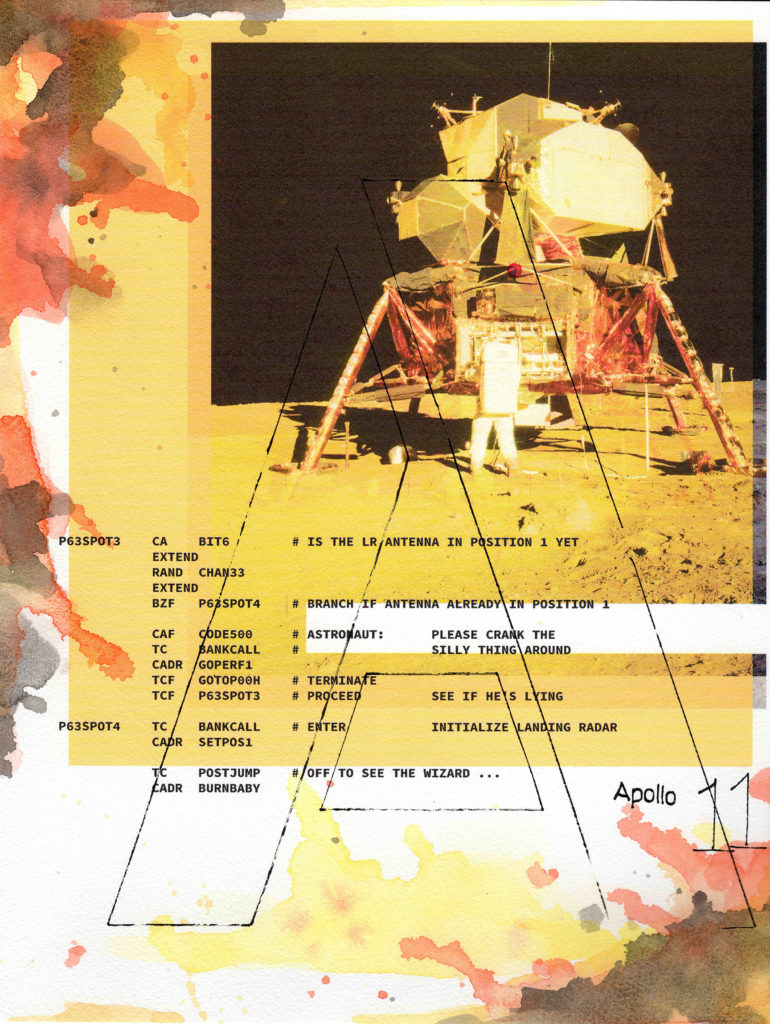
2. Apollo 11 Project
The Apollo 11 space program holds deep significance to me because my dad was a telemetry engineer at North American Rockwell in the 60s. Their operations facility in Downey, California focused extensively on testing the command and service modules before they shipped to Cape Canaveral. This testing insured Buzz Aldrin, Neil Armstrong and Michael Collins made it back to earth safely. The Apollo 11 project consists of thousands of lines of code with easter eggs peppered throughout, revealing the camaraderie of the original programming team. “Please crank the silly thing around” in one comment, for example, refers to the repositioning of the antenna for the landing radar. “Off to see the wizard…” in another leaves us imagining how excited the engineers must’ve felt as their code successfully ran. The code that put us on the moon is a marvel given the limited software tools available at the time.
3. Truncation
“Truncation” is a creative request from Obsidian’s Senior Security Researcher Jody Forness.
What is truncation? Here’s a deep dive from Jody: Integer truncation vulnerabilities result from the unintended consequence of converting a large number into an integer type that will only store a small number. For example, on a 32-bit machine, an int will store numbers from -2147483648 to 2147483647. An unsigned short will only store numbers from 0 to 65535. So, if one function defines a value as an integer, but then passes that same value to a function that defines the value as an unsigned short, some of the number will be “truncated”. In this example, the value 65536 has a binary representation of 10000000000000000 and when “converted” to an unsigned short “integer”…which can’t hold the entire value, the compiler will truncate to “0″. The user ID of “0” represents root. So a user ID of 65536 would unintentionally have elevated privileges as well.
The source of this example is from “The Art of Software Security Assessment” by Mark Dowd, John McDonald, and Justin Schuh.

4. Duff’s Device
Duff’s Device is a creative request by our VP of Product Sean Borman. What is Duff’s Device? Here’s Sean’s take on it.
On very rare occasions, programming might involve some creative rule bending to get the job done. Doing something in a way that the original designers of the language probably never anticipated and might even be horrified to observe. When you come across code like this, you might stare at it and swear that it’s just broken. Yet it works. You’ll curse that you don’t know how it works. You’ll stare at it some more. Then the light goes on – the epiphany! And then it’s “How they hell did they come up with that?” You marvel at the ingenuity. The sheer sneakiness.
Well, here’s such a story. It’s become something of a cult classic (even if it’s a pretty small cult).
Tom Duff was a programmer working at Lucasfilm in the 1980s. You know, Lucasfilm, famous for that “Star Wars” thing. Well, Lucasfilm used some cutting edge technology and tended to push it to the limit. Tom was working on improving the performance of a real-time animation playback program that ran at only half the speed required. Tom traced the problem to code that copied large blocks of data. The naive implementation was too slow, but Tom figured he could use a well-known optimization technique called “loop unrolling” to eliminate half the instructions, thus doubling performance.
Tom wrote the loop unrolled code in the “C” programming language but used a fiendish trick that seriously bent the language rules. While Tom’s code was technically still legal “C” his creative rule bending almost certainly could not have been imagined by Dennis Ritchie, the creator of the C programming language. Tom’s hack was so bad that Tom later wrote to Dennis showing his code, along with the following admission:
“Disgusting, no? But it compiles and runs just fine. I feel a combination of pride and revulsion at this discovery. If no one’s thought of it before, I think I’ll name it after myself.”
And thus was born “Duff’s device.”
We’ll leave it to you to read the code and discover the surprise, disgust and admiration for Tom’s creative rule breaking.
Source: https://www.lysator.liu.se/c/duffs-device.html

5. SQL Injection
We end the year with “SQL Injection.” This exploitation technique is a favorite of Jed Mitten, our Senior Security Researcher. Here’s Jed’s explanation: SQL Injection has been a prime target for web application exploitation, and it has enjoyed the #1 spot on the OWASP Top 10 list for over a decade [1]. It involves accessing the backend SQL database through the browser by manipulating the query string. It has been used in hundreds of security incidents, defacements, and service interruptions [2], and thus all user-controlled web parameters must be sanitized first. The continued exploitation of SQL injection goes to show that security and convenience are still forever at odds with one another.
[1] https://www.owasp.org/index.php/Category:OWASP_Top_Ten_Project#tab=Main
[2] https://codecurmudgeon.com/wp/sql-injection-hall-of-shame/

6. Morris Worm
Robert Morris is the “OG” insider threat of our time. In 1988, before the World Wide Web, Cornell grad Morris hacked into a MIT terminal and released his worm into the world. (then, a collection of computers used by the military and universities) The worm targeted computers running a specific version of the Unix operating system, reproducing itself endlessly while rendering email and basic functions impossible. Though the worm was harmless, its speed and scale broke the internet. To counteract the worm, computers had to be pulled offline and wiped clean before they could be plugged back in. This took several days, and would’ve been *more than* catastrophic in today’s cloud era.
The FBI investigated Morris and found him guilty under the Computer Fraud and Abuse Act. Morris’ trial was a wake up moment for the security industry, which felt a growing urgency to create new infrastructure to address cyber crime. Spared from jail time, Morris was given a fine, probation, and an order to complete 400 hours of community service.
Morris went on to co-found ViaWeb and Y Combinator. MIT bore no grudges when they hired him to become an assistant professor in 1999.

Last updated 2/11/2020. Steph Yeo & Sunny Volkert