Obsidian customers reduce their third-party SaaS integration risk by 80% on average.

See every SaaS integration from a single interface.

Measure the exact risk that each connection poses.

Understand the scope of every integration’s privilege and access.

Take action to limit or remove dangerous or inactive integrations.
Consolidate visibility into your SaaS integrations.
When any user can connect a new application to the environment, your SaaS supply chain can quickly become unmanageable. Obsidian gives your team complete and continuous visibility into every integration supported by crucial contexts around ownership, permissions, and access.
See and filter through every application connected to your SaaS environment.
Drill into any integration to see details around its ownership, publication, activity, creation date, and more.
Identify and eliminate excessive integration risk.
Obsidian details the individual factors contributing to each integration’s overall risk level. You’ll understand exactly why specific connections are more precarious than others and be able to initiate review and removal directly from the Obsidian interface.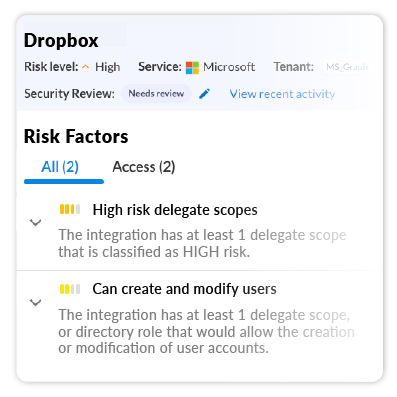
Measure the severity of each integration’s risk with aggregate scores that help your team prioritize accordingly.
Review the exact privileges and scopes attributed to every integration. See which permissions introduce the most risk.
Collaborate on and maintain records of security reviews for integrations directly through Obsidian.
Stay informed as risks and scopes evolve.
Be sure that previously trusted integrations don’t undergo sudden, unexpected changes in their potential risk levels. Obsidian lets your team know when a connection changes abruptly to facilitate review and prevent a potential compromise.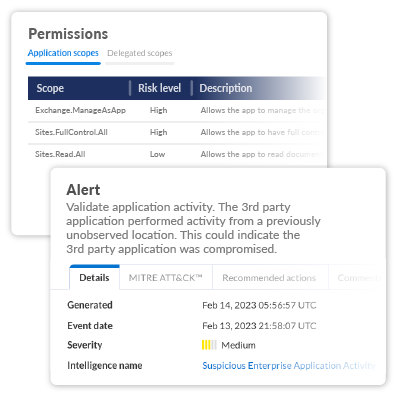
Track fluctuations to an integration’s allocated permissions and aggregate risk score over time.
Monitor historical activity for every integration. Uncover opportunities to prune inactive connections and minimize risk.