Obsidian aggregates a vast amount of data from SaaS applications to build a consolidated, normalized view of access, privilege, and activity. This data is a gold mine for security teams that want to understand what is happening in their applications and quickly detect and investigate signs of trouble. In order to unlock the real value of data, you need the right interface to consume it. Obsidian offers a powerful, highly scalable built-in search interface that allows threat hunters, compliance teams and incident responders to find events or patterns of interest.
For the first time, you have the ability to search for events, users, accounts and more across all your monitored SaaS applications. Are files with sensitive names being shared externally? Is a data exfiltration attempt triggering API rate limits? Was a user assigned additional admin privileges? Obsidian search makes it easy for you to find such events. In this post, we will look at the search capabilities in the Obsidian platform.
Why Search?
Widely used SaaS applications like Office 365, Salesforce, G Suite and Box provide activity logging as a built-in security control. These apps record a prodigious amount of user and machine activity that can quickly overwhelm even experts.
Search is the most intuitive interface for making sense of the data with analytics. Search provides the means to marry human instinct and machine data. It has long been the interface of choice for proactive security, threat hunting, and incident response.
Obsidian Search
Let us now dive into what Obsidian offers. Obsidian allows you to search and filter data in the Obsidian platform using a domain-specific language called Obsidian Query Language (OQL). OQL is based on the widely used open-source Apache Lucene project.
Here’s a quick summary of what you can do with search:
Search Based on a Broad Set of Criteria
The richness of the Obsidian data model enables search across a broad set of criteria, including:
- User (privileged/non-privileged)
- Email address
- Location
- Service
- Event type
- Event privilege level
- Event status
- Date and time
- IP address
- Devices
You can cast a wide net using a few criteria, or look for something specific like all events associated with a known suspicious IP address.
Save Searches You Want to Run Frequently
You can save time and effort by saving frequently used search queries.
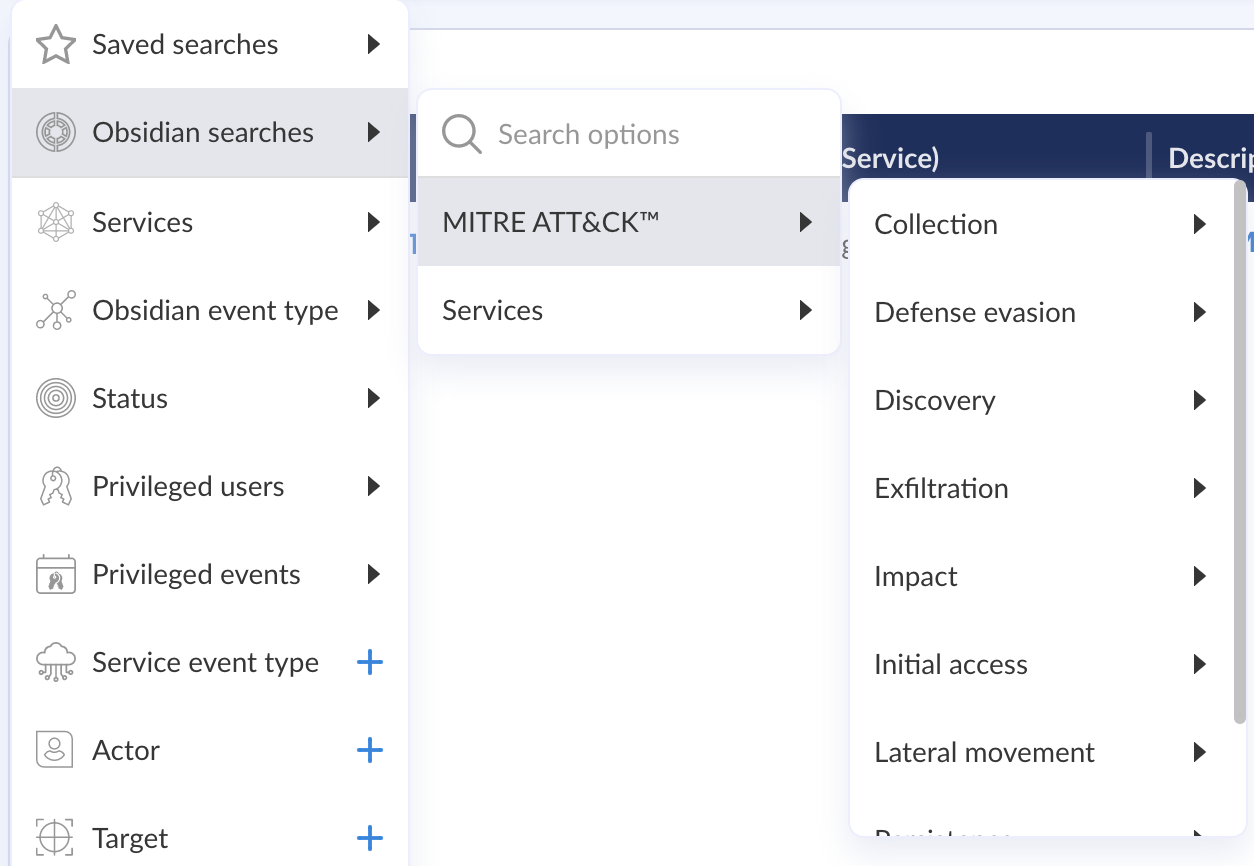
Use the Built-in Search Library
Use the library of 100+ helpful built-in searches that Obsidian provides to identify signs of trouble or to simply better understand what is happening in the applications . Built-in searches mapped to the MITRE ATT&CK framework are created by the Obsidian security research team to help security teams get up and running quickly. They are updated on an ongoing basis as our team discovers new queries that are useful for detection and response. You can also clone the search query and customize it according to your needs.
Examples
Let’s now look at a few examples of searches to whet your appetite and highlight the power of search. We will go progressively from broad searches to more and more specific ones.
- See all Zoom activity over the past 7 days:
timestamp:[now-7d TO *] service:zoom
- See all activity in a country but excluding the home office:
geo.country:”united states” -geo.city:"newport beach"
- See if a new mail forwarding rule was created in Office 365:
event:"microsoft.New-InboxRule" AND raw:*forward*
Here, we are running the search on native alerts generated by Microsoft. The Obsidian platform aggregates events and alerts from the SaaS applications in addition to generating its own events and alerts.
- See all pdf downloads by user John Doe until over a year ago for an insider threat investigation:
name:*pdf event:obsidian.download actor.name:”John Doe” timestamp:[* TO 2019-06-15T00:00:00.000Z]
Obsidian ‘download’ events have been normalized across all services to capture all activities that can be understood as a file download event on any platform, like Box and G Drive.
Conclusion
Search is an essential ingredient of every detection and response solution. The search capability in the Obsidian platform allows security teams to unlock the full potential of the data in their SaaS applications, enabling people and machines to work together.